Think about a recreation within the new gaming atmosphere the place you don’t simply full ranges and accumulate trophies, however actually personal each sword, artifact, or perhaps a piece of digital land.
The place your efforts are rewarded not simply with factors, however with tokens which have real-world worth, the place the destiny of the challenge isn’t determined by a company, however by you — alongside 1000’s of different gamers across the globe. This isn’t science fiction; it’s the fact ushered in by Web3 gaming.
On this article, you’ll uncover how Web3 gaming works, the way it differs from conventional fashions, what powers its financial system, and why each main studios and indie builders are shifting to those new applied sciences. We’ll additionally present how SCAND helps construct world-class Web3 options — and why now’s the proper time to enter this fast-growing business.
What Is Web3 Gaming?
Web3 gaming is a brand new method to creating and taking part in video video games, constructed on decentralized applied sciences.
Not like conventional gaming, the place all property and knowledge are owned by builders or publishers, Web3 video games are powered by blockchain and permit gamers to personal in-game digital property and non-fungible tokens, take part within the governance of recreation tasks, and immediately earn from their in-game exercise.
How Is Web3 Gaming Totally different From Conventional Gaming Fashions?
In conventional video games, customers don’t have any full management over their in-game gadgets or progress. All knowledge is saved on centralized servers, and recreation property may be blocked, deleted, or misplaced when switching platforms.

Not like conventional video games, Web3 video games are constructed from foundations of openness and true digital possession. On this case, gamers actually personal their in-game property as NFTs — not simply use them, however purchase, promote, commerce, and even switch them to different video games.
And so they can truly form the way forward for the sport by means of voting for options or updates inside decentralized communities like DAOs. It’s an entire new dynamic: gamers aren’t simply shoppers anymore — they’re co-creators, buyers, and collaborators.
Key Applied sciences Web3 Gaming
On the coronary heart of each Web3 recreation are applied sciences, reminiscent of blockchain, sensible contracts, gaming NFTs, and tokens. Blockchain retains every thing safe and clear, so gamers can belief that each transaction and interplay is recorded and verifiable.
Sensible contracts deal with the behind-the-scenes mechanics — like robotically giving out rewards or triggering actions when sure in-game situations are met.
NFTs flip recreation property into one thing actually distinctive and ownable, whether or not it’s a personality, a uncommon merchandise, or a bit of digital land. Tokens act as the sport’s forex and even give gamers a say in how the challenge evolves.
Collectively, these instruments create a decentralized recreation financial system the place gamers don’t simply play — they earn, contribute, and truly personal a part of the world they’re in.
How Does The Web3 Sport Work?
In a typical Web3 recreation, the participant begins by connecting their crypto pockets — no conventional sign-up required. From there, they’ll earn or buy in-game property, which instantly turn into their digital property.
These property, represented as NFTs, may be bought on marketplaces, transferred to different customers, and even utilized in different video games. Each motion is recorded on the blockchain, making certain full transparency and safety. Tokens earned by means of battles, quests, or energetic participation may be spent inside the recreation or exchanged for real-world worth.
On this approach, gameplay turns into not simply entertaining but additionally doubtlessly rewarding on a monetary stage.
Conventional Gaming Fashions vs. Web3 Gaming
To higher perceive how Web3 is altering the method to gaming, let’s examine it to the normal gaming mannequin. Beneath is a desk that illustrates the important thing variations between a centralized and decentralized method to gaming, from asset possession to participation in governance and knowledge safety.
| What’s Being In contrast |
Conventional Gaming |
Web3 Gaming |
| Who owns your stuff? |
All of your in-game gadgets belong to the sport’s builders, a government, or the platform itself |
You actually personal your gadgets as NFTs and tokens — they’re saved in your pockets |
| Are you able to commerce your gadgets? |
Normally not — or solely inside strict platform guidelines |
Sure — commerce, promote, or switch freely because of blockchain |
| How clear is it? |
Most techniques run on closed, centralized servers you’ll be able to’t actually see into |
Every thing is recorded on-chain — open, clear, and verifiable |
| Do you get a say? |
Selections are made behind closed doorways by the sport studio |
With DAOs, gamers can vote on updates, guidelines, and even funding decisions |
| Are you able to earn from taking part in? |
Sometimes, solely the sport firm income |
Gamers can earn tokens, commerce NFTs, and be part of an actual in-game financial system |
| Can gadgets transfer between video games? |
Probably not — your stuff stays locked in a single recreation |
Some gadgets and progress can carry over to different video games or platforms |
| How protected are your property? |
In case your account will get banned or the server shuts down(a basic single level of failure), you possibly can lose every thing |
Your property are in your pockets — you management them, not the sport firm |
Conventional Gaming vs. Web3 Gaming
Options of Web3 Gaming
Web3 video games are altering not simply how we play, however how we personal, work together inside the trendy gaming sector, and earn from the gaming expertise. Beneath, we’ll discover the important thing options that set Web3 gaming other than conventional fashions and outline its distinctive worth for gamers, builders, and buyers alike.
Transparency and Safety in Blockchain Gaming
In Web3 video games, every thing is open. Each motion is recorded on the blockchain, so there’s no room for dishonest or hidden guidelines. Plus, decentralization makes the sport a lot tougher to hack.
In-Sport Belongings as NFTs
In Web3, what you earn or purchase in-game is actually yours. Gadgets come as NFTs, which suggests you’ll be able to promote them, commerce them, and even use them in different video games. You truly personal your gear — not simply borrow it.
A Token-Based mostly Financial system
Tokens in Web3 video games aren’t simply in-game factors — they’ve actual worth. You need to use them to purchase issues, earn rewards, and even vote on recreation selections. It’s an financial system that works for each gamers and builders.
Play-to-Earn: Video games That Pay
Web3 turns gaming right into a supply of earnings. By finishing quests, successful tournaments, or creating content material, you’ll be able to earn tokens and NFTs which can be price one thing exterior the sport. It’s enjoyable and financially rewarding.
Cross-Platform Compatibility
Your gadgets don’t have to remain locked in a single recreation. In Web3, that very same sword or character can present up in different video games too — so long as they’re in the identical gaming ecosystem. It’s all linked, and your progress issues extra.
Way forward for Web3 Gaming Business
In line with Market Analysis Future, the Web3 gaming market was valued at USD 6.71 billion in 2024 and is projected to achieve USD 8.94 billion quickly. By 2034, it’s anticipated to soar to USD 118.36 billion, reflecting a formidable compound annual progress charge (CAGR) of 33.23% over the forecast interval (2025–2034). This positions Web3 gaming as one of many fastest-growing segments within the digital financial system.
On the similar time, short-term traits present indicators of market correction. As reported by Statista, Web3 gaming and metaverse investments dropped to USD 1.8 billion in 2024, a 38% lower in comparison with 2023. This decline suggests a shift from hype-driven funding to a extra mature part, the place buyers have gotten more and more selective and centered on sustainable, high-quality tasks.
Collectively, these traits point out that Web3 gaming is getting into a part of sustainable progress — the place success relies upon much less on pace and extra on stable expertise, strong recreation economies, and engaged participant communities.
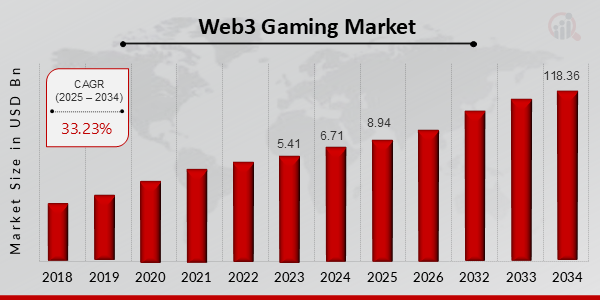
Web3 Gaming Market Overview (2025-2034)
What’s Gaming DAO
On the planet of Web3 video games, gaming DAOs are decentralized communities the place gamers take an energetic function in shaping the challenge. As a substitute of builders making all the selections, key issues — from recreation financial system balancing to new options — are put to a vote by token or NFT holders.
These DAOs are constructed utilizing sensible contracts and blockchain expertise, which suggests the principles are clear and might’t be modified on a whim. Gamers can vote on updates, affect story improvement, and even assist handle income distribution amongst guilds.
The profit is evident: gamers genuinely really feel like they’ve a say. It’s extra than simply taking part in a recreation — it’s being a part of a digital group the place you’re not only a person, however a accomplice.
Varieties of Gaming DAOs
Gaming DAOs can serve completely different functions relying on the roles of their members and the targets of the challenge. Some are centered on technical improvement, whereas others handle the group or in-game property.
Beneath are the principle kinds of Gaming DAOs generally present in Web3 tasks:
| Sort of DAO |
Description |
| Developer DAOs |
Made up of builders and technical groups. They make selections about updates, characteristic rollouts, and the sport’s general path. |
| Participant/Neighborhood DAOs |
Composed of energetic members of the gaming group. They vote on guidelines, recreation steadiness, and future occasions. |
| Investor/Fund DAOs |
Embody buyers and strategic companions. They deal with price range allocation, planning, and advertising. |
| Asset Administration DAOs |
Oversee NFT vaults, tokenized gadgets, and assets. They resolve find out how to use, commerce, or distribute recreation property. |
Varieties of Gaming DAOs
NFTs and Tokens in Web3 Gaming Platform
In Web3 video games, tokens and NFTs don’t give the participant simply instruments however liberty: to own, to resolve the destiny of the challenge, and to get rewarded within the course of. This makes the sport world extra actual. However duty comes together with it too — one has to comprehend what pitfalls lie on the trail and find out how to take care of them.
The Function of NFTs in Gameplay
In Web3 video games, NFTs aren’t simply digital decorations, however level to precise, distinctive gaming property. They are often something a beneficial asset can be: a uncommon sword, customized pores and skin, a personality with energy or gaming abilities, or perhaps a gaming panorama.
In some situations, they solely present bodily illustration however many have actual gameplay worth together with opening up particular missions or offering further energy to a personality.
As every NFT is authenticated on the blockchain, you personal it and might commerce it, switch it to your pockets, or use it in different video games. It’s your asset, and your possession is saved on the blockchain, not simply an merchandise sitting on the sport server.
Utility and Governance Tokens
Web3 video games often run on two kinds of tokens. Utility tokens are your on a regular basis recreation forex — use them to purchase gear, improve your character, or unlock new content material. You possibly can earn them by taking part in or shopping for them on crypto exchanges.
Then there are governance tokens. These provide you with a say in the place the sport goes subsequent — whether or not it’s financial modifications, new options, or DAO proposals. It’s a bit like being a part of a membership the place your vote truly counts.
Marketplaces and In-Sport Buying and selling
One of many coolest components of Web3 gaming is the open market. Whether or not it’s constructed into the sport or on platforms like OpenSea or Rarible, these marketplaces let gamers commerce gadgets and tokens freely.
That uncommon outfit you earned? Another person could be keen to pay actual cash for it. Some video games even construct their very own decentralized exchanges (DEXs), the place gamers commerce immediately — no middlemen, no further charges. This turns in-game gadgets into actual, liquid property with worth past simply gameplay.
Dangers and Challenges
In fact, it’s not all sunshine and rainbows. The Web3 gaming financial system nonetheless has its dangers. NFT costs can skyrocket primarily based on hype — and crash simply as rapidly. If the sport’s financial system isn’t balanced proper, it could result in inflation and lack of worth.
And let’s not overlook safety: bugs in sensible contracts or pockets breaches can result in severe losses. That’s why good video games take tokenomics significantly, put money into audits, and construct with safety in thoughts — to guard their gamers and hold issues truthful.
Web3 Options by SCAND
SCAND is an skilled software program improvement firm with over 20 years of historical past and a whole bunch of profitable tasks delivered worldwide. We focus on constructing customized digital options, together with merchandise within the Web3, blockchain, and decentralized purposes house. Our workforce is already working with purchasers from the gaming business who’re taking their tasks to the following stage with the ability of Web3 applied sciences.

Our Web3 Gaming Providers
At SCAND, we provide full-cycle Web3 recreation improvement — from preliminary idea and structure to launch and scaling. We perceive the distinctive calls for of the gaming business and ship customized options centered on efficiency, person engagement, and sustainable in-game economies.
Finish-to-Finish Web3 Sport Improvement
We design and construct video games with built-in blockchain-based gaming performance — from recreation design and UI/UX to backend improvement. Our workforce works with trendy recreation engines like Unity and Unreal, paired with completely different Web3 applied sciences reminiscent of Solidity, Web3.js, Ethers.js, and extra.
NFT and Token Integration
We implement NFT mechanics and token-based economies in gaming tasks. Our options allow the creation of distinctive in-game gadgets and purposeful tokens that may be built-in into DeFi protocols or linked to exterior marketplaces.
DAO Infrastructure for Gaming Platforms
SCAND builds DAO ecosystems tailor-made to gameplay. This contains sensible contracts for voting, revenue distribution, group governance, and gamer-led funding constructions — all designed to empower participant involvement.
Sensible Contract Safety and Audits
Our workforce conducts in-depth technical audits and testing of all sensible contracts to determine vulnerabilities. We guarantee the very best stage of safety and compliance with Web3 greatest practices — a crucial issue for video games with actual financial elements.
Why Gaming Startups and Skilled Builders Belief SCAND
What units SCAND aside isn’t just our Web3 experience, however the best way we work. We construct scalable, dependable, and user-focused merchandise — and we do it with a deep understanding of the challenges gaming groups face.
Whether or not you’re a startup constructing your first title or a studio increasing into Web3, we provide the pliability to adapt and the steadiness to develop with you. Consider us as a tech accomplice who actually will get your targets — and helps you attain them quicker.