We proceed our collection of articles targeted on testing programs that incorporate Multi-Issue Authentication (MFA or 2FA) safety mechanisms. In our earlier article about MFA testing, we explored why firms working in regulated industries should undertake these mechanisms to strengthen their safety.
Though there’s a variety of MFA options out there, most firms favor those who present a easy and easy person expertise, equivalent to MFA by way of SMS, e-mail, or TOTP.
On this article, we’ll delve into an important subject: what are the challenges associated to testing workflows that embrace MFA, and what methods might be adopted to beat them?

1. Key Challenges in MFA Check Automation
1.1 Dependency on Exterior Units
By design, MFA depends on exterior units, equivalent to telephones for receiving SMS or apps for producing TOTP codes. This reliance complicates check automation, particularly when a number of accounts are concerned:
- Electronic mail MFA: QA groups generally use alias-based e-mail constructions (e.g., person+alias@area.com) to streamline account creation. Nonetheless, these strategies may be restricted or disabled in company settings, complicating automation efforts. On high of that, retrieving emails from third-party suppliers is a problem.
- SMS MFA: Every person account usually requires a novel telephone quantity. This results in logistical points, equivalent to managing bodily SIM playing cards or sharing check telephones, which undermines effectivity and scalability. Ever needed to name your colleague to allow them to share the MFA code retrieved on their telephone?
- TOTP MFA: Time-based One-Time Passwords require safe dealing with of personal keys. Automating checks turns into intricate, as these keys are often inaccessible after initialization.
1.2 Restricted Automation Feasibility
MFA workflows work together with exterior programs, making them arduous to automate and sometimes impractical, significantly for third-party providers like e-mail suppliers (e.g., Outlook). Automating such interactions is resource-intensive and sometimes restricted by service suppliers that block bot connections.
1.3 Dangerous Method #1: Disabling MFA in Check Environments
To avoid wasting time, some groups disable MFA in testing environments. Whereas expedient, this method introduces vital dangers:
- Elevated Safety Threat:
- Accounts turn into much less safe in testing environments, as MFA turns into non-compulsory.
- Divergent habits from the manufacturing atmosphere undermines check validity, as you would possibly uncover points in manufacturing brought on by a misconfiguration.
- Much less Consultant Checks: Checks fail to mirror real-world manufacturing situations, rising the chance of undetected bugs surfacing in manufacturing.
- Human Errors: Configuration variations between testing and manufacturing environments complicate deployments, generally leading to unintended coverage misconfigurations in manufacturing.
- Incomplete Checks: Key steps like login processes or transaction validation are skipped, lowering the flexibility to detect points in vital functionalities.
1.4 Dangerous Method #2: Intercepting MFA in Testing Environments
Whereas higher than disabling MFA, this method nonetheless dangers configuration divergence between environments and potential errors throughout deployment (i.e. discovering points in manufacturing).
1.5 A pricey however Efficient Method: Interfacing with Third-Social gathering Suppliers
This methodology, though generally pricey and sophisticated, might be extremely helpful in case your service suppliers (e-mail or SMS) provide APIs or interfaces suitable with automation instruments like Cypress or Robotic Framework. Instruments like Eggplant may also assist obtain this aim.
These integrations will let you immediately extract MFA codes and incorporate them into your automated check scripts.
Nonetheless, it’s usually essential to proactively talk with these suppliers, as they could be reluctant to permit automated entry to their programs. For example, you would possibly discover it’s fairly arduous to automate outlook login and e-mail content material retrieval by means of an internet interface. Regardless of these challenges, this method ensures real looking testing aligned with manufacturing eventualities.
2. Methods for Automating and Testing Finish-to-Finish MFA Workflows
2.1 Align Testing Environments with Manufacturing
Guaranteeing parity between testing and manufacturing environments is important for figuring out potential points successfully. Leveraging instruments to retrieve MFA codes by way of e-mail, SMS, or APIs can provide the next advantages:
- Improved UX/UI Detection: Reproducing manufacturing situations helps determine anomalies within the person expertise or interface.
- Load Administration: Testing below production-like constraints uncovers system weaknesses, equivalent to throttling points or utilization limits for MFA providers.
- Third-Social gathering Service Validation: Verifies correct integrations and ensures messages aren not misplaced. Load testing may also reveal vulnerabilities below heavy utilization.
2.2 Collaborative Guide Testing Options
For handbook testing, collaborative options can simplify MFA administration inside QA groups:
- Electronic mail: Use shared mailboxes with aliases (e.g., testing+xyz@firm.io) to centralize code reception. In case your IT division doesn’t will let you use such options, you would possibly want to contemplate another method from a 3rd get together. For example, digital mailbox providers like GetMyMFA provide non-public e-mail addresses to retrieve MFA codes.
- SMS: Options like GetMyMFA provide non-public digital telephone numbers, avoiding bodily units. Free choices like Obtain-SMS-Free exist however pose dangers as a result of publicly shared numbers. This represents a difficulty as your group’s SMS messages can turn into public (Search Engine indexing).
- TOTP: Securely share secret keys utilizing password managers like Bitwarden or 1Password. This allows groups to entry momentary codes with out bodily units whereas managing key entry successfully.
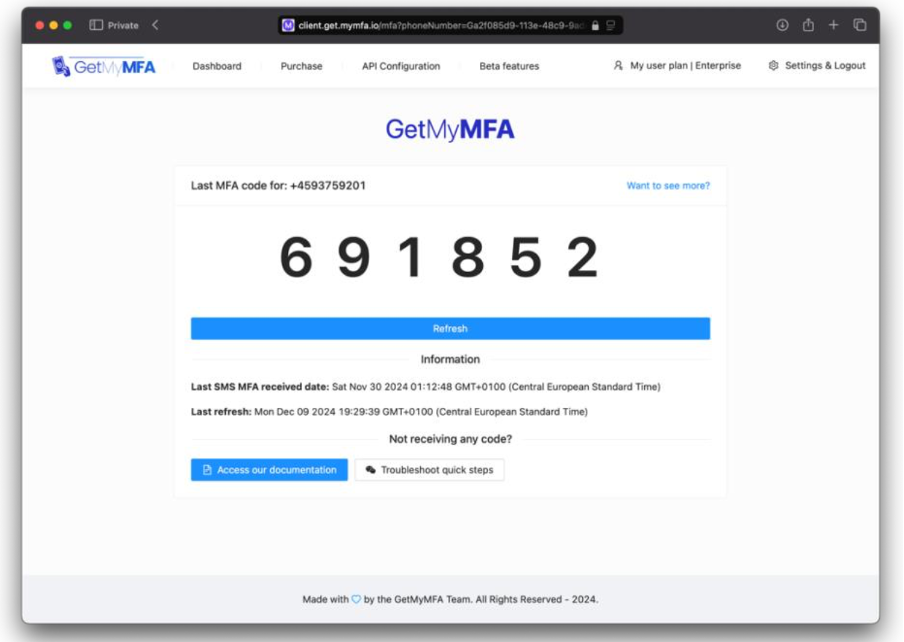
2.3 Automation Instruments for MFA Testing
Automating MFA checks requires instruments that simplify interactions with authentication mechanisms. Specialised APIs streamline this course of, lowering the necessity for advanced handbook integrations and combating suppliers on bot-blocking insurance policies. Examples embrace:
- Electronic mail APIs: Providers like MailSlurp or GetMyMFA permit producing momentary e-mail addresses to automate code retrieval by way of APIs.
MFA retrieval illustration by means of GetMyMFA’s programmatic API
-
- SMS APIs: Digital telephone quantity suppliers, equivalent to GetMyMFA, simplify automating SMS MFA workflows by exposing a public and safe API which extracts the MFA codes obtained to your non-public telephone numbers. This enables to keep away from buying and dealing with SIM playing cards. On high of that, you may simply share the telephone numbers with the QA staff members.

- TOTP APIs: Suppliers provide options for importing non-public TOTP keys, exposing OTP codes by way of APIs.
Conclusion
Successfully testing workflows that incorporate Multi-Issue Authentication (MFA) mechanisms stays a problem for QA groups, who usually find yourself disabling MFA in staging environments. Nonetheless, it’s important to check these flows to make sure the reliability and safety of programs in manufacturing. The constraints associated to automation and handbook testing (significantly the dealing with of exterior units and interactions with third-party providers) spotlight {that a} simplistic or rushed method can result in vital dangers, whether or not when it comes to safety, check validity, or tester expertise.
Utilizing specialised tools-such as e-mail inbox administration providers or digital telephone quantity platforms-alongside collaborative methods for handbook testing permits groups to simulate production-like situations as carefully as doable. These approaches not solely reduce the hole between testing and manufacturing environments, but additionally improve the staff’s skill to detect vital points earlier than deployment.
In conclusion, adopting a well-thought-out technique for MFA testing-combining the correct instruments, collaborative processes, and automation finest practices-is important to satisfy this problem. It ensures that MFA workflows carry out as anticipated in a exact and repeatable method.
Not solely does this strengthen the robustness of MFA flows, nevertheless it additionally protects finish customers and improves anomaly detection. With such an method, firms can guarantee their programs are each safe and dependable, whereas nonetheless delivering a high-quality person expertise.
In regards to the Writer: Jonathan Bernales
I’m the CTO at Germen, an InsurTech firm constructing tech platforms for each company and particular person shoppers. I’m enthusiastic about constructing and utilizing expertise that enables groups to ship high-quality code in advanced environments with out compromising on safety or pace. I’m additionally the founding father of GetMyMFA.