Writing a classy pc program typically requires numerous detailed
information. If we do that in Java, we have to know the syntax of the
language, the wide selection of libraries accessible to help us within the work,
the varied instruments required to confirm and construct our applications. If we do that
in Python as a substitute, we’re confronted with a distinct syntax, libraries which can be named
and work otherwise, a complete different ecosystem to construct and run our work.
Confronted with these particulars, a pure response is to recruit individuals who
are educated a few particular ecosystem. Thus we see job descriptions that say “at
least three years of Java”, and even deeper necessities for subsets of that
neighborhood, with expertise in particular instruments. What use is a talented
Python programmer to such a crew?
We have at all times felt that such needs are wrong-headed. The traits
that we have noticed separating efficient software program builders from the chaff
aren’t issues that rely on the specifics of tooling. We reasonably respect
things like: the information of core ideas and patterns of programming, a
knack for decomposing advanced work-items into small, testable items, and the
skill to collaborate with each different programmers and people who will
profit from the software program.
Throw such a Python programmer right into a Java crew, and we might count on them to
prosper. Positive they’d ask numerous questions in regards to the new language and
libraries, we might hear numerous “how do you do that right here?” However such questions
are shortly answered, and the impediments of Java-ignorance quickly wither
away.
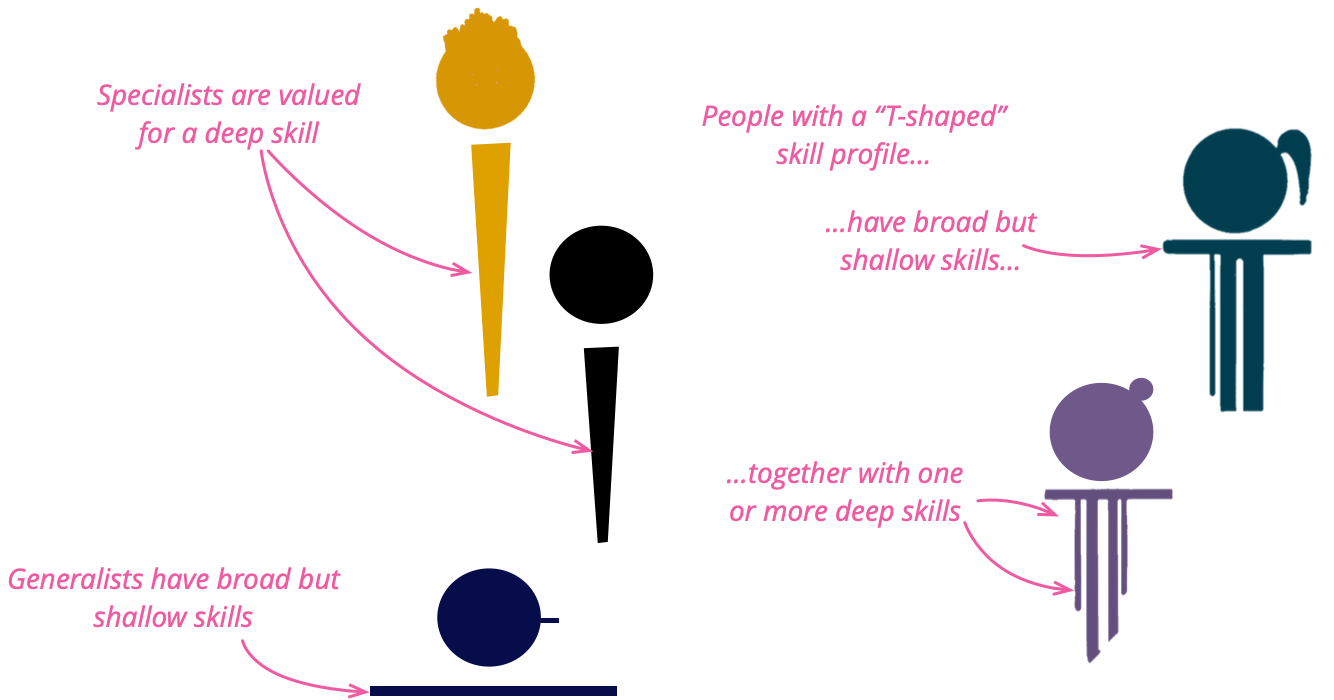
This echoes a protracted debate in regards to the relative worth of specialists and
generalists. Specialists are seen as folks with a deep ability in a selected
topic, whereas generalists have broad however shallow abilities. A dissatisfaction
with that dichotomy led to the thought of “T-shaped folks”: people that mix
deep information in a single matter, with a broad however shallow information of many
different matters. We have seen many such folks shortly develop different deep legs,
which does not do a lot for the “T-shape” identify (as we’ll talk about beneath), however in any other case results in
success. Usually expertise of a distinct setting results in attempting issues
that appear revolutionary in a brand new house. Of us that solely work in a single
technological neighborhood are on the fixed danger of locking themselves
right into a information silo, unaware of many instruments that would assist them of their
work.
This skill goes past simply developer abilities. We have seen our greatest
enterprise analysts acquire deep abilities in a few domains, however use their
generalist abilities to quickly perceive and contribute in new domains.
Builders and Consumer Expertise people typically step outdoors “their lanes” to
contribute extensively in getting work carried out. We have seen this functionality be an
important high quality in our greatest colleagues, to the diploma that its significance
is one thing we have taken without any consideration.
However more and more we see the software program {industry} push for
rising, narrower specialization.
So over the past 12 months or so we have now began to withstand this industry-wide
push for slim abilities, by calling out this high quality, which we name an
Professional Generalist. Why did we use the phrase “professional”?
There are two sides to actual experience. The primary is the acquainted depth: an in depth command
of 1 area’s inside workings. The second, essential in our fast-moving area
is the power to be taught shortly, spot the
fundamentals that run beneath shifting instruments and tendencies, and apply them wherever we land.
For instance from software program groups, builders who roam throughout languages, architectures, and downside areas might seem to be
“jack-of-all-trades, master-of-none,” but repeated dives beneath floor variations assist them
develop sturdy, principle-level mastery. Over time these generalists can dissect unfamiliar
challenges, spot first-principles patterns, and make assured design selections with the
assurance of a specialist – and quicker. Being such a generalist is itself a
subtle experience.
We have lengthy seen that not simply anybody succeeds as an Professional Generalist,
however as soon as we perceive the traits which can be key for such Professional Generalists,
organizations can form studying applications, hiring filters, and profession paths
that intentionally develop them. Certainly our hiring and profession development at
Thoughtworks has been cultivating this ability for over twenty years, however doing
so informally. We expect the {industry} wants to vary gears, and deal with Professional
Generalist as a first-class ability in its personal proper: one thing we identify,
assess, and practice for. (However beware, we discover many Professional Generalists,
together with a minimum of one creator of this text, cringe on the phrase “professional”.)
The Traits of an Professional Generalist
After we’ve noticed Professional Generalists, there are specific attributes
that stand out.
Curiosity
Professional Generalists show numerous curiosity. When confronted with a brand new
know-how or area, their default response is to need to uncover extra about it, to see
how it may be used successfully. They’re fairly blissful to spend time simply exploring the brand new
matter space, build up some familiarity earlier than utilizing it in motion. For many, studying new
matters is a pleasure in itself, whether or not or not it is instantly
relevant to their work.
This attribute is noticeable when Professional Generalists get a solution
to a query. Moderately than simply typing in some code from Stack Overflow,
an Professional Generalist’s curiosity normally motivates them to make sure they
perceive the reply, taking the chance to broaden their information,
and examine that the reply they bought is suitable. It is also current when
asking a query. There may be an artwork to asking questions that elicit deeper
solutions with out main the witness.
Collaborativeness
Studying a few new matter space might require studying, watching movies, and prototyping. However
we see the best support right here is one other very important attribute: collaborativeness.
A smart Professional Generalist is aware of that they’ll by no means actually find out about a lot of the issues
they run into. Their T-shape will develop a number of legs, however by no means sufficient to span all of the
issues they should know, not to mention need to know. Working with individuals who do have these
deeper abilities is important to being efficient in new domains.
Working with an otherly-skilled employee permits the generalist to
contribute whereas the expert collaborator spots more practical paths that
solely a specialist would know. The generalist appreciates these
corrections, studying from them. Studying entails each understanding extra about
the brand new area, but additionally studying to distinguish between areas the place the
generalist can do major contributions and areas the place the generalist
wants assist from the specialist. We discover Professional Generalists are by no means
afraid to ask for assist, they know there may be a lot they’re blind to, and
are desirous to contain those that can navigate by way of these areas.
An efficient mixture of collaborative curiosity requires
humility. Usually when encountering new domains we see issues that do not
appear to make sense. Efficient generalists react to that by first
understanding why this odd habits is the way in which it’s, as a result of there’s
normally a motive, certainly a very good motive contemplating its context. Typically,
that motive is not legitimate, or was lacking an essential consideration
within the first place. In that state of affairs a newcomer can add appreciable
worth by questioning the orthodoxy. However at different occasions the explanation was, and
continues to be legitimate – a minimum of to some extent. Humility encourages the Professional
Generalist to not leap into difficult issues till they’re certain they
perceive the complete context.
This humility extends to recognizing the totally different trade-offs we see
throughout architectures. An structure designed to help giant volumes
of straightforward transactions will differ from one designed to deal with a couple of
advanced interactions. Professional Generalists are comfy in a world the place totally different
trade-offs make sense in several circumstances, normally as a result of their
travels have uncovered them to those variations.
Buyer Focus
This curiosity and eagerness to collaborate with folks with totally different abilities does increase a
hazard. Somebody pushed by curiosity can chase each shiny object. That is the place the
attribute of customer-focus comes into play. We are sometimes impressed with
how an Professional Generalist takes every unfamiliar know-how and questions the way it helps the
buyer. We’re followers of Kathy Sierra’s notion that our objective as software program builders is to assist our
prospects change into “badass” at what they do.
Buyer-focus is the mandatory lens to focus curiosity. Professional
generalists prioritize their consideration on the issues that may assist them
assist their customers to excel. This encourages studying about what their
prospects do, and the way they’ll enhance their work. It focuses consideration on
applied sciences that contribute to constructing these issues. Buyer-focus
energizes collaboration, encouraging the change of data between
buyer and technologist, and permitting the Professional Generalist to
coordinate different technologists in the direction of enabling the shoppers’
excellence.
Favor Elementary Data
Software program growth is an enormous area, the place no one can know every little thing, or perhaps a
cheap fraction of every little thing, so all of us have to prioritize what matters we be taught. Professional
Generalists favor elementary
information, that does not change into outdated with adjustments when platforms replace. These are
typically expressed as patterns or rules. Such information tends to age slowly, and is
relevant when people transfer into new environments. For instance the essential strikes of refactoring
are the identical no matter language you’re programming, the core patterns of distributed techniques
reappear often (and it is no coincidence that is why we wrote books on these matters – we
like ebook gross sales that final for a few years).
Mix of Generalist and Specialist Expertise
Thus generalists typically have deep information of fundamentals, and we normally see them have
deep information of some different matters too. They mix a broad basic ability with a number of
areas of deeper information, normally acquired as it is necessary for merchandise they’ve labored
on, coupled with the curiosity to dig into issues that puzzle most individuals. These deeper
areas might not be related to each engagement they work on, however is a sign for his or her acumen
and curiosity. We have realized to be suspicious of people that current as a generalist but
haven’t got a couple of deep specialties.
We talked about earlier than {that a} widespread identify for this abilities profile is that
of the “T-shaped” individual, implying a mix of specialist and generalist
abilities. Whereas the T-shape moniker did catch on, it comes with a
main downside within the metaphor, we do not discover such people have solely a
single deeper ability. They normally have a couple of, of various depth. We’re not
the one folks to establish this downside, and there have been a number of
different names proposed to explain this skill-set, though the options
all have their very own issues.
The vertical stroke of a ability set represents broader, long-lasting
domains, not particular instruments or frameworks. An professional generalist subsequently pursues depth
in distributed-data techniques—partitioning and replication methods, fault-tolerance
mechanisms, consistency fashions, and consensus algorithms—as a substitute of mastering solely
Databricks notebooks. Within the cloud, they concentrate on cloud-native structure: auto-scaling
heuristics, multi-region fail-over and so on reasonably than
specializing in AWS-specific configuration syntax. On the entrance finish, they research browser-based
UI structure—rendering pipelines, state-reconciliation patterns, and accessibility
primitives—as a substitute of the most recent React APIs.
Sympathy for Associated Domains
Professional generalists typically discover themselves in unfamiliar territory—be
it a brand new software program stack, a brand new area, or a brand new function. Moderately than chasing
exhaustive element from day one, they domesticate a tough, perceptive sense of
what works within the new setting. That helps them make decisions that
go together with the grain—even when it differs from their earlier expertise.
Jackie Stewart, a triple Components 1 world champion (1969-93),
described how, whereas he wasn’t an engineer of the automobiles he drove, he
nonetheless wanted a way of how they
labored, how they responded to what the motive force was attempting to do, a
sense he known as mechanical sympathy.
Martin Thompson introduced this
idea into software program, by speaking about how the same information
of how pc {hardware} works is significant to writing high-performance
software program.
We expect that the notion of mechanical sympathy has a broader
sense in software program, in that we do have to domesticate such a
sympathy for any adjoining area to those we’re engaged on. When
engaged on a database design, we’d like such a sympathy for the
user-interface so we will assemble a design that may work easily with
the user-experience. A user-experience designer wants such a sympathy
with software program constraints so when selecting between equally priceless
consumer flows, they keep in mind how onerous it’s to construct them.
This additionally reveals itself with new groups. When becoming a member of a brand new crew, professional
generalists are likely to hearken to the established ways in which a crew works,
introducing totally different approaches thoughtfully. Even when coming in as
leaders, they do not default to ripping up current workflows in favor of
these extra acquainted to them. Their curiosity extends to understanding why
totally different folks work in several methods, attempting out unfamiliar working
types, then incorporating their expertise to develop practices to
enhance from the present state.
Assessing Professional Generalists
We now have two essential checkpoints for recognizing —after which nurturing
—professional generalists: the hiring interview and ongoing profession
development.
Hiring
Conventional interview loops nonetheless revolve round product
trivia—“Clarify Spark’s shuffle phases,” “How does Databricks Delta
time-travel work?” A candidate who has by no means touched these instruments can
nonetheless be precisely the form of individual we’d like: somebody who shortly
grasps unfamiliar ideas, breaks advanced techniques into manageable
elements, and collaborates throughout features. Specializing in a single stack
or cloud supplier dangers filtering out such expertise.
To floor that potential, widen the dialog past device
recall. Ask candidates to speak by way of previous experiences:
- How did they method a very difficult state of affairs?
- When have they ventured into an unfamiliar area, and the way did
they stand up to hurry?
- How do they collaborate with folks inside and out of doors their very own organisation or
self-discipline?
These tales reveal studying velocity, techniques considering,
and folks abilities—the uncooked materials of an professional generalist.
Instance · Course of-control engineer We as soon as met an engineer
whose whole résumé was industrial PLC work—no general-purpose
language, no net, no cloud. But his report of diagnosing
control-system failures and the questions he requested in the course of the
interview confirmed distinctive studying agility. Employed for these
qualities, he grew right into a revered technical chief and later a
product proprietor. Rejecting him for not understanding “our” instruments would have
been a pricey miss.
Profession development
Contained in the organisation, slim verticals can freeze development: UI
builders, QAs, information engineers, or cloud specialists seldom step
outdoors their lanes. The expansion paths map one-to-one with vertical
silos: UI Engineer → Senior UI Engineer → UI Architect, or Knowledge
Engineer → Senior Knowledge Engineer → Principal Databricks Guru. The
unintended message is, “wander outdoors your lane and your progress
stalls.
We now have discovered that encouraging folks to experiment—letting them
make errors and be taught in adjoining disciplines—yields exceptional
advantages. A enterprise analyst writing code out of curiosity, a
front-end engineer dabbling in DevOps, a knowledge engineer attempting
product evaluation: every cross-pollination broadens each the
particular person and the crew.
Instance · Medical-domain analyst A non-technical skilled
from healthcare joined us as a enterprise analyst. His ardour for
tech pulled him into code evaluations and pairing classes. Over time he
turned an excellent tech lead and a broader strategic thinker than
many conventional “pure” engineers.
Each tales underscore the identical lesson: if we base evaluation and
development solely on a guidelines of instruments, we forfeit the possibility to
work with good, adaptable folks—and we hamper the organisation’s
skill to innovate.
Rising Professional Generalists
From Instruments to Fundamentals
IT tendencies get triggered by pivotal innovations that allow new enterprise
alternatives. Product suppliers and gear distributors shortly construct merchandise,
and the {industry} focus typically shifts to experience in instruments and frameworks
reasonably than the underlying technical tendencies. For instance, within the Nineties,
when graphical-user-interface two-tier architectures have been in style, the
important ability was mastering Object-Oriented Programming — its iterative,
collaborative design — but most consideration centred on instruments like Rational
Rose, the C++ programming language, and frameworks reminiscent of Microsoft
Basis Lessons. When the Internet arrived, understanding Internet structure
and global-scale caching was essential, however early hype gravitated towards
applied sciences like J2EE. In at present’s cloud period, with advanced microservice
based mostly architectures, big-data applied sciences, and expansive DevOps
toolchains, the foundational self-discipline of distributed techniques is usually
ignored whereas certifications in particular instruments dominate.
One of many greatest issues with extreme concentrate on instruments and framework
experience is when it’s cemented into organizational buildings. Groups and
organisations get structured round device experience, with hardened
boundaries making it troublesome for folks from one crew to amass abilities
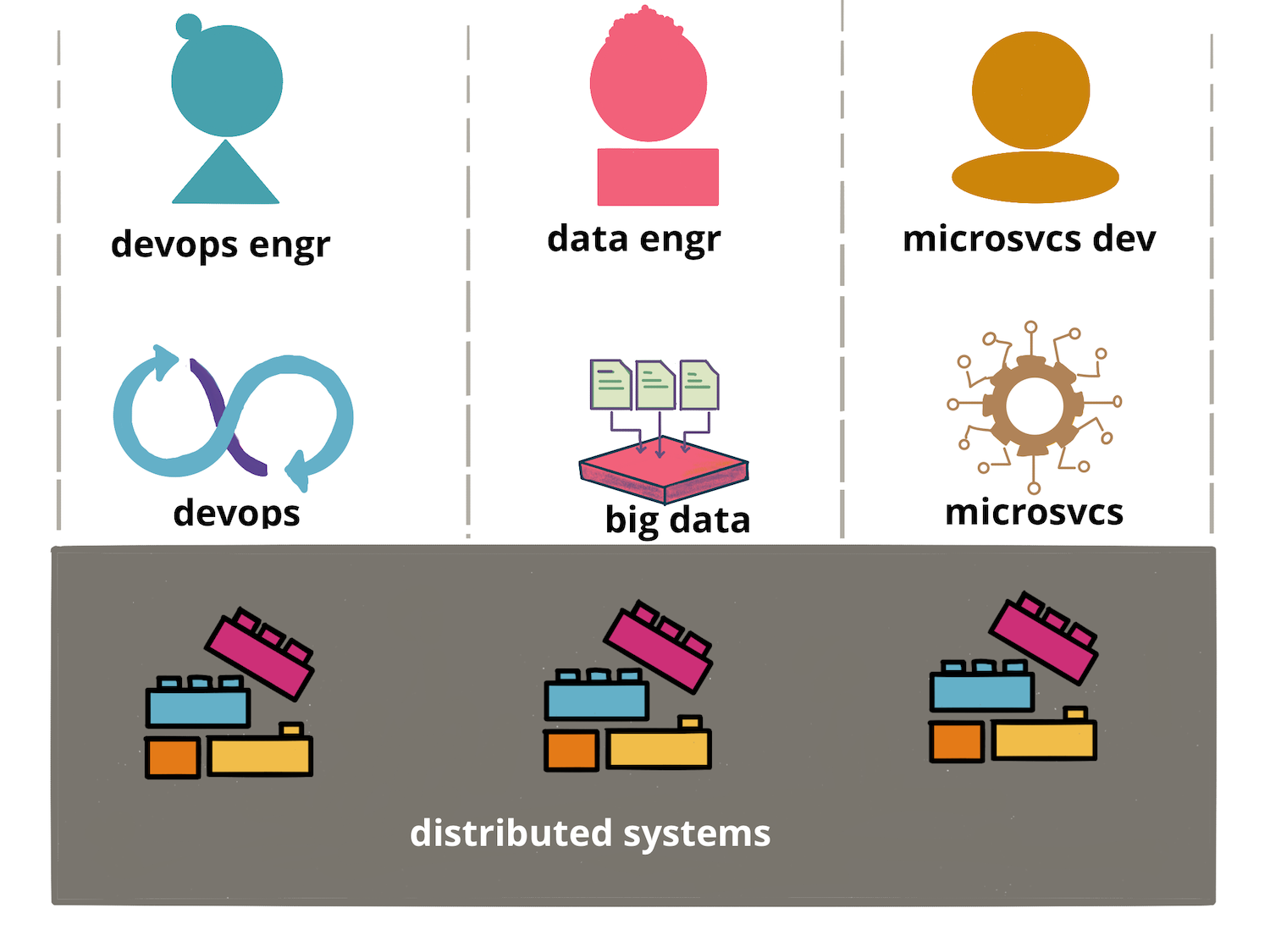
from others. Past language preferences like Python or Java, you may see
this crystallise within the three most
widespread software program verticals—Software Improvement, Knowledge Engineering,
and DevOps. Are labels like “Software Improvement,” “DevOps,” and “Knowledge Engineer” simply innocent
shorthand for the work we do? Not likely. As soon as these phrases harden into profession lanes, they
solidify the very silos that the Agile and DevOps tradition was meant to dismantle. The
labels change into an organisational anti-pattern—turning stream right into a sequence of hand-offs when
it needs to be a cross-functional dash. All three share the identical
distributed-systems foundations, and anybody who masters these fundamentals
can navigate all three with out getting misplaced in every vertical’s
ever-growing toolset. An professional generalist acknowledges this and makes the
deliberate effort to grasp these fundamentals.
Why does our consideration preserve drifting towards device experience? It is not
as a result of persons are shortsighted or lazy; it is as a result of the basics are
onerous to see amid the noise. Key concepts disguise beneath stacks of product docs,
YouTube tutorials, vendor blogs, and convention talks. At one finish of the
spectrum lie dense tutorial papers and college programs; on the different, vendor certifications tied to a single product. Connecting
these dots — chopping by way of the floor to succeed in the necessities — takes
deliberate effort. One confirmed support is the language of patterns: reusable
problem-solution pairs that seize the core precept with out the model
labels. That is why we belive in investing in exploring, distilling, and
sharing such patterns — so the {industry} dialog can shift from “Which
device ought to I be taught subsequent?” to “Which underlying rules and patterns
should I grasp?”
In our expertise, the nice grasp of this widespread language of patterns
and rules additionally strengthens the product-service partnership. As we speak
the connection is usually one-way: product groups ship options, service
groups eat APIs. Product groups determine the right way to certify an engineer as an
professional in a product and repair groups goal to do these certifications.
Cloud suppliers and gear distributors typically demand a sure variety of
“licensed professionals” earlier than they may recognise a service supplier as
a reliable accomplice. But our expertise reveals little correlation between
certifications and
competence. The concentrate on fundamentals pays off when competence is
most wanted: an engineer versed in Raft can untangle a Kubernetes
control-plane stall which may puzzle a number of licensed admins, and a
Delta Lake write anomaly could be resolved from first-principles reasoning
about optimistic-concurrency management as a substitute of looking vendor docs.
As soon as builders throughout roles share the lingua franca of a system’s
internals, the partnership turns into bidirectional — each side can
diagnose, suggest, and refine options collectively. Higher but, the
engineers who’ve a very good grasp of the basics are capable of accomplice
properly with a number of product and platform groups, without having to have
product particular coaching for every product
An Instance Workshop: Breaking silos and constructing partnerships
We have seen that we will develop the Professional Generalist ability by way of mentoring
and publicity to diversified ecosystems, however one of many penalties of
recognizing Professional Generalist as a first-class ability is that we must always
present coaching in the same approach that we do with specialist abilities. Such
coaching at present barely exists in our occupation. We have begun to fill that
hole with workshops which can be intentionally centered on creating the Professional
Generalist competence, and we expect there needs to be extra coaching alongside
these traces.
To assist stimulate serious about this, this is the main points of such a workshop,
aimed toward builders to attach Software Improvement, Knowledge Engineering,
and DevOps. The workshop views this work by way of a distributed techniques
lens, shifting consideration to shared constructing blocks and establishing a
widespread language throughout groups. Though this instance is developer-centric,
we expect the identical precept could be tailored simply as successfully to any function that
advantages from cross-disciplinary perception.
As we noticed earlier, every self-discipline—Software Improvement, Knowledge Engineering, and DevOps—faces the identical
distributed-systems realities, but we nonetheless lack a shared language. The important thing challenges of
these techniques are the identical. They have to replicate state,
tolerate partial failures, and nonetheless supply consistency ensures to finish customers.
A list of patterns across the implementation of
partitioning, replication, consistency, and consensus—that lets each
crew speak in regards to the fundamentals with out tool-specific jargon is an efficient begin.
One workshop won’t flip folks into professional generalists, nevertheless it does give them a head-start and a transparent
window into the challenges their friends deal with day by day. That visibility lowers the barrier
to cross-discipline duties and deepens everybody’s understanding of the merchandise and platforms
they use.
The workshop construction – Constructing the miniature
One of many challenges in instructing the summary patterns is that the builders have to do some psychological mapping
to attach the sample to the product in use. For this reason we selected an method to construction
the workshops round particular merchandise, however then concentrate on the patterns which can be most related
and utilizing the product as a window into the broader ideas.
The way in which we structured the workshops to show distributed-system patterns, is by coding
pocket variations of Kafka, Kubernetes, and Delta Lake. The concept is to select a flagship product
from every broad space of specialty, and construct it step-by-step. Implementing a flagship system
in just some hundred traces flips your perspective from ‘a consumer’ of a product
to ‘a builder’. An essential mindset shift. To maintain the
train grounded in actuality, write it within the product’s personal language, mirror its file and
methodology names, and depend on actual infrastructure — ZooKeeper or etcd, an on-disk log, stay
sockets. The consequence stays shut sufficient to the unique to spotlight the pivotal design
decisions whereas nonetheless supplying you with a protected canvas for experimentation. This method is highly effective,
as a result of every goal is usually open supply, the second the miniature works, you may open the
full codebase on GitHub, recognise the listing construction, and really feel assured submitting a
patch. The miniature isn’t a toy; it’s a gateway.
We now have three workshops, one for every of the three techniques.
Construct Your Personal Kafka — a miniature written in Java.
We use ZooKeeper for membership and retailer each message in a single append-only log. Even
on one node you meet the basic fsync dilemma: flush each write for security or batch for
pace.
Add a second course of and also you’re out of the blue confronted with many selections. You want partition
chief election, quorum acknowledgements, an in-sync reproduction record, and a high-water-mark
so shoppers by no means learn uncommitted information. (A cluster-wide controller comes later, as soon as
a number of partitions seem.) Every mechanism maps to a manufacturing characteristic in Kafka. After
strolling this code you recognise why a dealer stalls when a duplicate slows and know precisely
which metric to graph subsequent time it occurs.
The takeaway sample is straightforward: an append-only log guarded by quorum replication—a design
you’ll encounter all through trendy distributed techniques.
Kubernetes from the Inside Out.
Begin by writing a controller that watches a JSON doc in etcd, then calls reconcile()
till the native Docker daemon displays that desired state. In a short time it’s a must to select
the right way to record working containers, queue occasions, and preserve spec and standing distinct—precisely
the issues that dominate the Kubernetes code base.
Add actual failure circumstances and issues get tough. What ought to the controller do when a
container exits? How does a Postgres container preserve its information? Every determination forces you to
motive about restart insurance policies and persistent-volume claims. After that train, the dense
Go structs in kube-controller-manager really feel like pure continuations of a mannequin you
already perceive. The core studying: the facility of a declarative desired state converged
by
reconcile loops – the widespread sample of orchestration in trendy distributed techniques
ACID on Object Storage – A miniature Delta Lake.
Create a listing of Parquet recordsdata and pair it with a textual content log; every information change appends
a JSON file naming the brand new information file. Transfer this setup right into a miniature object retailer and
each append turns into its personal key-value write, with the Parquet file as the worth. To
deal with concurrent writers, wrap the append in an optimistic lock that retries if the log
tail adjustments. After a dozen commits start-up drags, so that you add a checkpoint file and be taught
first-hand why Delta Lake emits one each N transactions. From there, time-travel queries
drop out naturally from the log-plus-checkpoint design. The important thing takeaway, attaining ACID
ensures on ultimately constant storage by way of an immutable transaction log,
optimistic concurrency, and periodic checkpointing – a sample very important for contemporary information
lakehouses.
Every miniature leaves you with a concrete sample — append-only log, reconcile loop,
optimistic commit—that travels properly past the unique context. When the following new device
arrives, you may recognise the sample first and the product identify second, which is exactly
the behavior that turns professionals into Professional Generalists.
Professional Generalists nonetheless want Specialists
Whereas we have spent this text praising the Professional Generalist, we
concurrently don’t deny the worth of specialist information. Even essentially the most
expert Professional Generalist might should spend priceless time determining the
particulars of the right way to do one thing with a brand new platform. Their information of
widespread patterns helps them know what to search for, their ability
helps them analysis quicker, nevertheless it’s nonetheless longer than what a specialist
already is aware of. Moreover an Professional Generalist might miss a significant method
that is explicit to a website, primarily as a result of the Professional Generalist
would not know what they do not know – a entice a specialist is way much less possible
to fall into. In our expertise, a crew of Professional Generalists with out
specialist information of the core know-how of their work will nonetheless get the
job carried out, however can be considerably slower than a crew with specialist
abilities on board.
The purpose right here is that to be essentially the most environment friendly, the crew wants some
specialist ability. There must be a minimum of one deep specialist on a crew
for any core know-how that the crew is working with. However we have discovered that,
offering the crew is collaborating successfully, we do not want very many. Usually
one or perhaps two folks is sort of sufficient.
With somebody with specialist information current, a much less educated
Professional Generalist can shortly ask a query when they’re confronted with a process
that wants the depth. Equally the specialist ought to overview the work of
much less educated colleagues, to allow them to spot when people are taking the
fallacious path and present them the higher approach.
We expect it is very important have such a specialist accessible full-time on
the crew. A lot of their worth comes from being aware of questions and
points as they arrive up. On this state of affairs, the essential value to observe is
the Price of Delay – the pace of resolving
questions is far more essential that the utilization of the specialists. So
it is price having a full-time specialist even when it means they are not totally
occupied.
All of this does want everybody concerned to have proper form of
collaborative attitudes. The specialist must be somebody who’s eager to
share their information with everybody else on the crew, and is approachable
with dumb questions. The Professional Generalists want be comfy
demonstrating their ignorance, and truly take pleasure in being advised they’re doing
one thing fallacious in an unfamiliar setting. All in all there must be
loads of psychological security round.
And, after all, the folks with specialist abilities can typically be Professional
Generalists themselves, with the specialty being legs of their T.
The flip-side of that is the hazard of groups that consist solely of
specialists. Issues outdoors their specialty can simply be missed. For
instance a knowledge engineering crew that is stuffed with specialist information engineers can
miss something that is not particular to information engineering, reminiscent of high quality
technique, launch administration, and worth articulation.
Professional Generalists within the Age of LLMs
Massive Language Fashions and instruments based mostly on LLMs are rising in prominence.
We have noticed that Professional Generalist capabilities are significantly extra
priceless with these LLMs. The connection between Professional Generalists and
LLMs is usually much like that between Professional Generalists and specialists in
a crew. Equally to a specialist, an LLM can quickly reply questions that
an Professional Generalist may have when working in a brand new area. This
considerably lowers the barrier for exploring utterly new and unfamiliar
instruments, providing a fast solution to get began.
An Professional Generalist, armed with
a stable grasp of fundamentals and the knack to grasp rules and
patterns, can actually harness the facility of LLMs. They don’t seem to be simply asking an
LLM to put in writing code in a brand new language; they’re capable of ask extra insightful
questions, critically assess the AI-generated ideas towards their
broader understanding, and adapt these ideas to suit sound
architectural patterns. Their curiosity discourages them from merely
accepting a solution, however to know how proposed options work – which
is strictly the habits wanted to beat the unreliability inherent in
LLM-given recommendation.
We have seen that Professional Generalists method working with LLMs in a
totally different approach. Moderately than searching for “the reply”, they immediate them to
generate questions, explaining mechanisms, and offering examples and even
instruments that assist discover the underlying mechanisms of an concept.
So, regardless of the early days of this know-how, we expect that the rise of
LLMs will additional improve the significance of expert Professional Generalists, and
thus incentivize enterprises to place extra effort into figuring out,
and coaching folks with these abilities.
Why Organizations Want Professional Generalists
The only motive why organizations ought to pay extra consideration to Professional
Generalists is the lack of alternatives to workers groups. Discovering precisely the
proper form of specialist limits the candidate pool, both from hiring from
outdoors, or by inside transfers. So long as there’s sufficient specialist
ability accessible to help, Professional Generalists typically do as properly, certainly typically
higher, than including one other specialist.
However the advantages of Professional Generalists go additional than that. Trendy
software program techniques contain many parts, needing collaboration between
specialties to ship options to manufacturing. Too typically we see stifled communication, with
people blocked whereas ready on dependent groups to schedule crucial work.
Numerous these queues between groups impedes stream, slowing down the discharge of
priceless options.
Professional Generalists can unplug the pipes. Typically they do that by making
the interplay smoother because of their overlapping abilities, typically they
know sufficient to do a few of these dependent duties themselves. Certainly one of many
biggest values an Professional Generalist brings is the power to Get Issues
Carried out. The shopper-focus drives a very good Professional Generalist to make use of their
collaborativeness, curiosity, and abilities mix to drive options to
completion. If it requires crossing competency boundaries, they may discover a
solution to do it. If they should quickly purchase some deeper abilities, they may do
so. They do danger taking over greater than they’ll chew within the course of, however that
skill to shut the deal is usually crucial in getting vital software program
out the door.
The flexibility to see advanced techniques throughout their full breadth could be
important when issues go fallacious. Faults are sometimes not within the depth of a
single know-how, however within the implicit interactions between them. If
specialists cannot see the entire image, they simply miss what falls between
the gaps.
The presence of Professional Generalists crossing the competency boundaries
also can improve information switch between competency teams, rising
everybody’s sympathy for associated domains. This mechanism additionally encourages
specialists to discover the Professional Generalist ability for themselves.
Specialists have a tendency to make use of their acquainted device in contexts the place it would not
make sense. We will not fault them for that, if you happen to’ve by no means seen a
screwdriver, you may naturally attain for a hammer first. Professional Generalists
usually tend to decide applicable instruments. There’s a danger there, of
introducing too many instruments into an setting. Typically it is higher to make use of
a familiar-but-inferior device, than to introduce a sophisticated device for a
slim process that is a burden as soon as the Professional Generalist strikes on. A smart
Professional Generalist will take that issue under consideration.
The broad view that Professional Generalist develops naturally leads them
in the direction of management roles. Crossing specialties encourages them to develop
communication abilities, notably abilities on explaining totally different
disciplines to one another. Collaboration naturally grows relationships with
key folks round a company. Buyer-focus, Getting Issues Carried out,
construct credibility with enterprise management. Organizations that take
deliberate steps to nurture Professional Generalists can reap the reward by
rising technologists with a strategic perspective, with out essentially
pushing them into administration tracks.
All that mentioned, even though we’re clearly massive proponents of
Professional Generalists, there are downsides. Maybe the best is that
though we have discovered it potential to evaluate folks for his or her Professional
Generalist ability, it is a troublesome process, typically requiring intensive
participation from known-capable Professional Generalists. Years on
the job, quizzes, and certifications are a lot simpler assessments to manage
(though we’re cynical about how they relate to delivering worth).
A crew stuffed with Professional Generalists, however with out explicit abilities for the
central domains and platforms they’re engaged on, can be much less productive –
a minimum of till the Professional Generalists develop these abilities. As we talked about
earlier, it is essential to have somebody with these deep abilities on the crew,
who can both be specialist in that area or an Professional Generalist who has
that as one of many legs of their “T”.
All in all, we have seen so lots of our colleagues develop their Professional
Generalist ability, with out the identify, and construct upon it to be vital elements
of profitable know-how and enterprise initiatives. They’re the folks we
have realized from, the folks our purchasers go to with issues to resolve and
alternatives to take advantage of. Our hope with this text is that extra folks in
our occupation (and maybe others) will begin to acknowledge “Professional
Generalist” as a first-class ability, and put extra effort in describing its
traits, the right way to assess it, and the right way to develop it. We consider that
giving this ability correct recognition can do a lot to enhance the follow of
our occupation.
Takeaways
- Professional Generalists share a number of key traits
- Curiosity
- Collaborativeness
- Buyer-focus
- Favoring elementary information
- A mix of specialist and generalist abilities
- Sympathy for associated domains
- Groups ought to mix Professional Generalists with a couple of key specialists
- Professional Generalist abilities are enhanced by LLMs
- Professional Generalists guarantee advanced duties get carried out
- We have to deal with Professional Generalist as a firstclass ability
- Consider folks’s ability as an Professional Generalist in hiring and
promotion
- Develop coaching simply as a lot as for specialist abilities