The healthcare business in america is a considerably difficult space. There are lots of medical health insurance plans (non-public medical health insurance for almost all and public medical health insurance for low-income individuals and the disabled), many suppliers, and plenty of numerous funds coming from quite a few payers.
The complexity of this multi-layer system, in flip, makes it fairly exhausting to control, management, and defend each single a part of it. That’s the reason many sources are more and more reporting varied leaks of confidential knowledge.
Between January and September 2024, US healthcare organizations suffered 491 main knowledge breaches with over 500 information compromised. Hereby, the determine has risen during the last ten years.
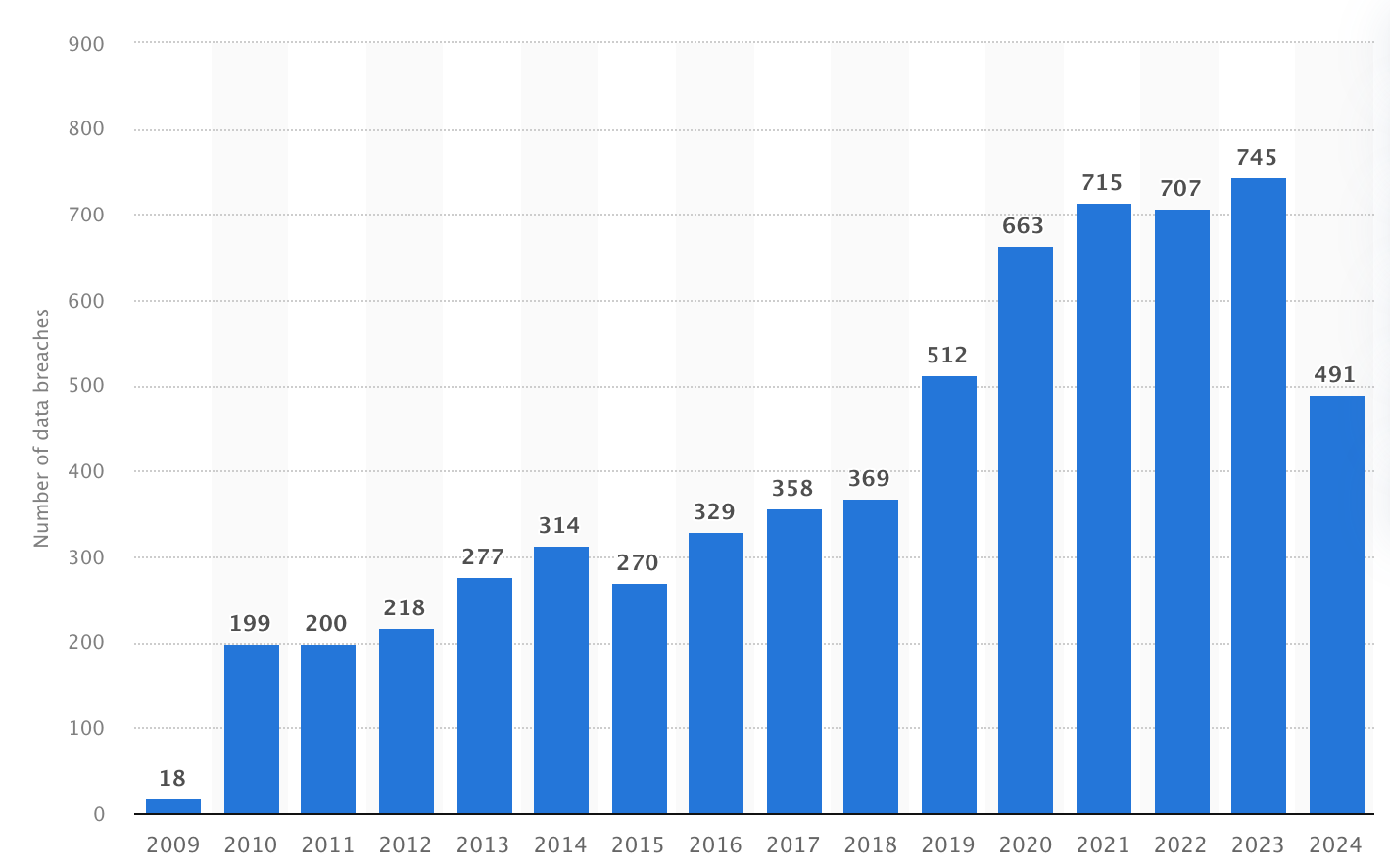
Variety of healthcare knowledge breaches in america (2009-2024), Statista
To stop any diploma of data leakage, all medical apps within the US are obliged to comply with HIPAA rules (Well being Insurance coverage Portability and Accountability Act).
On this information, we’ll stroll you thru the whole lot it’s worthwhile to find out about HIPAA-compliant app growth—from important certifications and software program growth phases to widespread errors, prices, and future tendencies.
What’s HIPAA and Why Does It Matter?
Basically, HIPAA is a federal American regulation whose goal is to guard affected person well being info (PHI). It units requirements for the storage, transmission, and entry of healthcare info to keep away from breaches and undesirable entry.
For medical institutions that plunge into well being app growth providers, HIPAA compliance isn’t solely a authorized matter—it’s a dedication to determine belief, keep away from hefty fines, and defend knowledge.
Non-compliance and HIPAA violations can imply financial penalties of 1000’s to tens of millions of {dollars}, along with damaging repute.
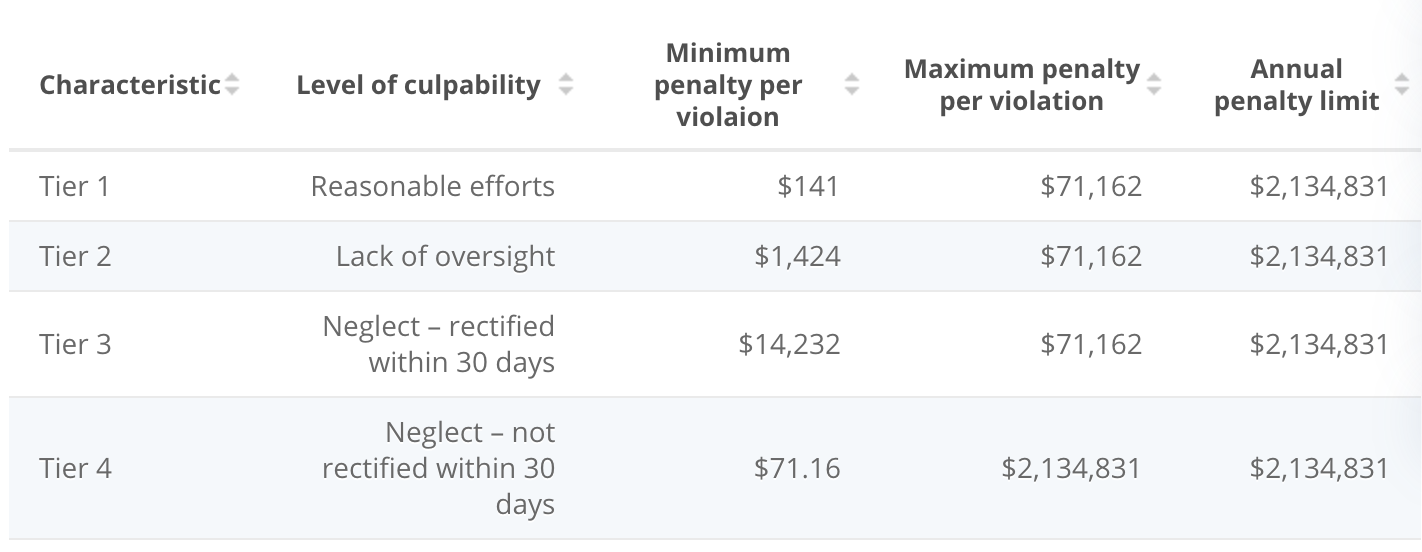
Quantity of fines for HIPAA violations (August 2024), Statista
Key HIPAA Guidelines and Their Influence on App Improvement
The HIPAA legislation was handed in 1996 with a purpose to make the healthcare system extra sufficient and immediate. The legislators had been conscious that digital methods have the prospect to reveal sufferers’ non-public well being info.
Subsequently, HIPAA was cut up into a number of separate rules that altogether should defend people’ private well being info or mitigate the implications of breaches.
- The Privateness Rule: The Privateness Rule creates requirements for the use and disclosure of well being info. It protects individuals’s non-public well being information and provides them the suitable to seek out out about using their info. The rule applies to sure organizations, together with hospitals, docs, and insurance coverage corporations, that are referred to as “lined entities.”
- The Safety Rule: The HIPAA Safety Rule executes requirements for safeguarding digital well being knowledge. It regulates any group that collects or processes this sort of info from corresponding software program, e.g., wellness or physician apps. The rule requires them to have sufficient protections in place—respectable insurance policies, protected methods, and protected storage on bodily units.
- Breach Reporting: If there’s an information breach, HIPAA Breach Reporting mandates the app supplier to tell customers, the Division of Well being and Human Companies (HHS), and typically the media.
- The Enforcement Rule: The HIPAA Enforcement Rule encompasses compliance and investigation provisions, analysis of civil cash penalties for violating the HIPAA Administrative Simplification Rule, in addition to procedures for listening to.
Should-Have Options in a HIPAA-Compliant Software program
Once you make a healthcare app that holds confidential affected person knowledge, HIPAA compliance is necessary. However being compliant isn’t a lot about checking bins as it’s about placing sure options in place that safeguard private well being particulars.

First, your cell app requires knowledge encryption. This implies all well being knowledge have to be encrypted to unreadable kind when it’s being saved or transmitted. Subsequently even when somebody steals the info, they will be unable to learn it.
Then be sure you have resilient person authentication, which implies solely authenticated individuals (docs, nurses, or sufferers) ought to be capable of log in and see particular info. This may be through passwords, two-factor authentication (e.g., a code texted to your cellphone), and even face ID or fingerprint.
Moreover, you would need to implement role-based entry management. Not all people wants to have the ability to view the whole lot.
For instance, a doctor might want to view medical information, however a receptionist will solely must view appointment knowledge. Position-based management minimizes entry to an absolute minimal of what’s crucial.
Moreover, embody computerized log-out. If an individual forgets to log off of the cell app, it ought to log them out after a brief interval of inactivity to forestall different people from inadvertently accessing confidential information.
In case your utility offers messaging, video calling, or sharing recordsdata, all of these parts should even be unassailable. All communication must be made safe in order that nobody outdoors the applying can pay attention in or see non-public paperwork.
And simply in case issues do go amiss, your app ought to have a breach notification attribute. It must be able to detecting the issue and notifying customers and correct authorities rapidly, as HIPAA requires.
Lastly, keep in mind that it’s an ongoing job to stay protected. Once you develop HIPAA-compliant cell software program, your app should have house for normal updates and safety fixes to defend in opposition to new risks as they’re recognized.
Steps to Construct a HIPAA-Compliant Cellular App
In 2023, it was reported that 35% of US companies that export knowledge overseas stated privateness rules are an added price. Moreover, 17% stated rules had been a notable barrier to cross-border commerce.
But, the absence of a basic knowledge privateness safety legislation on the federal entrance makes any firm conflicting with different states or areas which have extra uncompromising commitments.
Thus, HIPAA-compliant cell app growth providers (irrespective of whether or not iOS or Android) have to be structured right into a course of that features not solely writing the code, but in addition constructing belief, defending well being knowledge, and adhering to strict rules at each step.
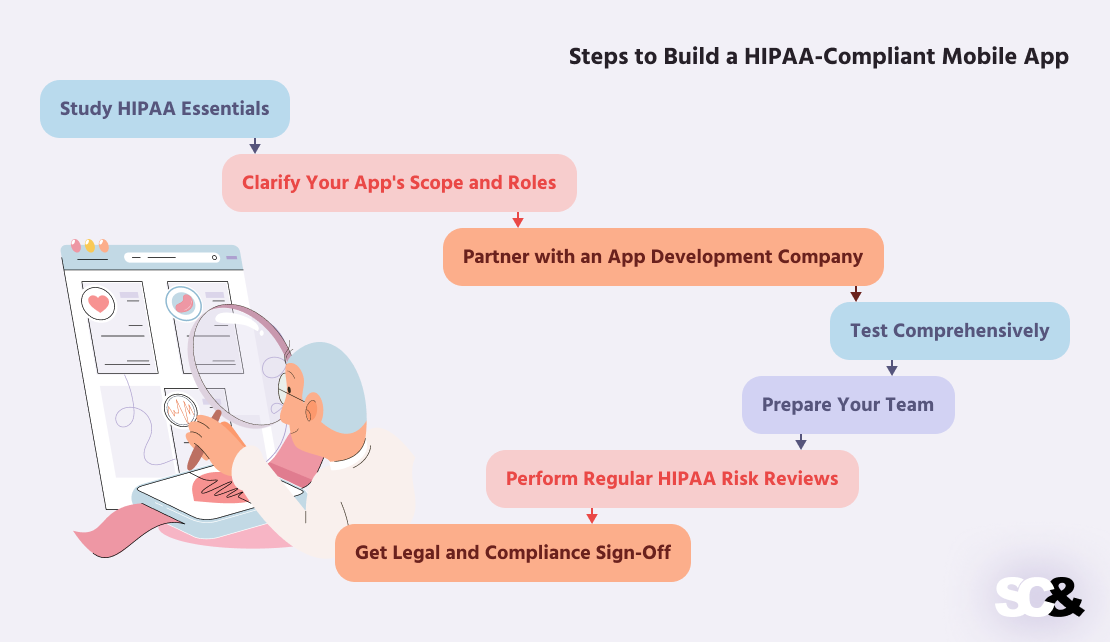
1. Examine HIPAA Necessities
Earlier than writing a single line of code, begin by getting your self acquainted with what HIPAA requires usually. It’s worthwhile to know what sort of knowledge constitutes protected well being info, what decrees cowl the storage and disclosure of that info, and what technical, bodily, and administrative precautions are mandated.
2. Make clear Your App’s Scope and Roles
Second, explicitly state what your healthcare utility will do, who will use it (sufferers, physicians, staff, and so on.), and what sort of well being knowledge it can management. At this level, resolve whether or not your app is a “lined entity” or a “enterprise affiliate” as a result of HIPAA instructions are barely completely different for every.
3. Associate with an App Improvement Firm
One of many smartest strikes you can also make once you dive into HIPAA-compliant app growth is to accomplice with an utility growth workforce, equivalent to SCAND, that has experience within the subtleties of healthcare software program growth.
A superb accomplice will assist you choose the suitable cell app growth method, select a tech stack for various cell units, and handle implementing all of the required safety features, together with encryption, person authentication, audit logs, and computerized logouts.
They’ll additionally make sure that your app contains acceptable role-based entry management, so customers solely see the knowledge they really want.
4. Check Comprehensively
Compliance and safety testing go hand in hand when making software program. Past useful exams, it’s necessary to check for vulnerabilities, encryption weaknesses, misconfigured entry controls, and logging issues. If possible, rent exterior safety professionals to assessment your app.
5. Put together Your Crew
Ensure that everybody concerned, from app builders to assist workers, understands HIPAA fundamentals. Coaching is part of compliance. Even an awesome app may be made non-compliant when affected person info is mishandled by somebody who isn’t conscious.
6. Carry out Common HIPAA Danger Critiques
Carry out a danger evaluation earlier than launching your app (and recurrently afterward). This may uncover any spots the place your app’s safety, knowledge dealing with, or infrastructure may very well be in danger.
7. Get Authorized and Compliance Signal-Off
Have authorized and compliance professionals assessment your app and documentation previous to going stay. They’ll assure that your app is HIPAA compliant in all respects and assist with the last-minute particulars, equivalent to signing Enterprise Affiliate Agreements (BAA) with any third-party distributors that you just use.
8. Watch, Replace, and Keep Compliant
HIPAA compliance isn’t a one-off exercise—it’s steady. After going stay, proceed to observe your app for exposures, recurrently revise it, and carry out periodic audits to maintain your self in compliance with all the provisions as legal guidelines and expertise change.
Widespread Errors in HIPAA Compliance and The way to Keep away from Them
It’s troublesome to develop a HIPAA-compliant app when even minor errors could cause severe issues, equivalent to knowledge breaches or authorized ramifications. The brilliant aspect is that almost all of them may be bypassed if you realize what to search for.

Some of the widespread errors isn’t understanding what protected well being info is. PHI isn’t merely medical information—it’s any particular person info associated to an individual’s wellness. Should you don’t defend any such info adequately, you could possibly unknowingly violate HIPAA tips.
One other widespread mistake is skipping the chance evaluation (you will discover extra about it under). Earlier than you launch your app, it’s worthwhile to examine for potential safety threats.
Many builders both overlook this step or put it off. However if you happen to don’t assess your app’s safety, you’ll be able to’t know if there are defects that want correcting.
Selecting the inaccurate providers and instruments is a frequent mistake too. Not all cloud providers or instruments are HIPAA-compliant. Should you use a service that won’t execute a BAA, it isn’t protected to make use of for the processing of PHI.
| Widespread Errors | Why It’s a Downside | The way to Keep away from It |
| Not understanding what PHI contains | You might by accident expose or mishandle protected knowledge with out realizing it. | Be taught what qualifies as PHI—it’s not simply medical information however any health-related knowledge. |
| Skipping the chance evaluation | Safety flaws go undetected, growing the prospect of knowledge breaches. | All the time carry out an intensive HIPAA danger evaluation earlier than launch. |
| Delaying the chance evaluation | Suspending it means you may miss vulnerabilities throughout vital phases of dev. | Make it a part of your early and ongoing growth course of. |
| Utilizing non-compliant instruments or cloud providers | Utilizing platforms that received’t signal a BAA may end up in non-compliance and knowledge publicity. | Select distributors and instruments that explicitly assist HIPAA and supply BAAs. |
The way to Conduct a HIPAA Danger Evaluation
A HIPAA danger evaluation is necessary for making certain that your app stays compliant and protects delicate well being knowledge. It might sound difficult at first, however if you happen to break it down into steps, it turns into a lot simpler to deal with.
First, it’s worthwhile to perceive precisely what sort of well being knowledge your app handles. Embrace not simply medical information, but in addition private info like:
- Names
- Telephone numbers
- Insurance coverage particulars
- Appointment dates
Understanding what knowledge you’re accumulating, storing, or sharing helps you determine what must be protected.
Subsequent, it’s worthwhile to decide who has entry to that knowledge, equivalent to your workforce, sufferers and healthcare suppliers, or third-party distributors. Not everybody ought to have full entry to all the info, so it’s necessary to arrange entry controls that enable customers to see solely the knowledge they want.
As soon as you realize what knowledge you might have and who can entry it, it is best to take a look at your present safety measures. Are you utilizing encryption, safe logins, and correct entry management to guard the info?
You additionally want to think about bodily safety, like how and the place you retailer the info. If there are any gaps in your safety, you’ll want to handle them to remain compliant with HIPAA.
Then, it’s worthwhile to take into consideration the potential dangers to the info. These may come from inside errors, like an worker by accident exposing info, or exterior threats, like hacking makes an attempt. By figuring out these dangers, you’ll be able to determine what elements of your app could be susceptible and what must be improved.
After that, consider the influence of those dangers. How dangerous wouldn’t it be if a breach occurred? Would delicate knowledge be uncovered? How seemingly is it that this may occur? This helps you prioritize which dangers have to be handled first.
Once you’ve discovered the dangers, it’s time to take motion. You may must strengthen your encryption, enhance login safety, restrict who has entry to sure knowledge, or conduct common safety checks.
It’s additionally necessary to doc the whole lot you do in the course of the danger evaluation. Preserve observe of what knowledge you deal with, the dangers you’ve discovered, the safety measures you’ve put in place, and any adjustments you make. That is necessary for HIPAA compliance and can make it easier to throughout audits or if any points come up sooner or later.
Lastly, do not forget that HIPAA compliance isn’t one thing you do exactly as soon as. As your app adjustments and new threats emerge, it’s worthwhile to recurrently assessment and replace your danger evaluation. This fashion, you’ll be able to preserve your app compliant and make sure the knowledge stays protected.
The way to Get a HIPAA Compliance Certification
HIPAA certification is verified by HIPAA coaching to validate the understanding of corresponding compliance requirements, usually performed yearly. Profitable trainees are awarded a HIPAA compliance certificates.

For a corporation, HIPAA certification is when a third-party verifier confirms whether or not the corporate abides by all of the rules wanted to guard well being info.
Having a HIPAA certificates of compliance is a big a part of proving that your app or enterprise is solely safe, and there are some issues you are able to do to show you’re HIPAA compliant:
- Change into acquainted with HIPAA’s Privateness, Safety, and Breach Notification Guidelines that comprise tips to guard PHI.
- Perform an evaluation for specifying potential gaps for governing PHI.
- Develop and put in place administrative, bodily, and technical safeguards to handle acknowledged dangers.
- Educate workers on HIPAA insurance policies and procedures related to their roles to take care of PHI within the acceptable method.
- Rent an unbiased firm to examine your compliance measures through audits and value determinations.
- Implement corrective actions on the idea of audit findings to close any compliance gaps.
- On profitable compliance, get hold of a proper certification of adhering to HIPAA requirements.
Though there isn’t any HIPAA certification issued by the federal government, you’ll be able to work with a reliable third-party auditor. These consultants will audit your methods and examine if they’re HIPAA compliant.
Should you meet their audit, they offers you a report or certificates stating you’re compliant, one thing that is essential for displaying purchasers and companions that you’re following the rules.
Value of HIPAA Compliance
HIPAA compliance may be from extraordinarily inexpensive to extraordinarily expensive, relying upon the dimensions and complexity of your group or app. There is no such thing as a fastened price to develop into compliant, however having an thought of the place the prices most frequently lie, you’ll be able to funds accordingly and never be caught off guard.
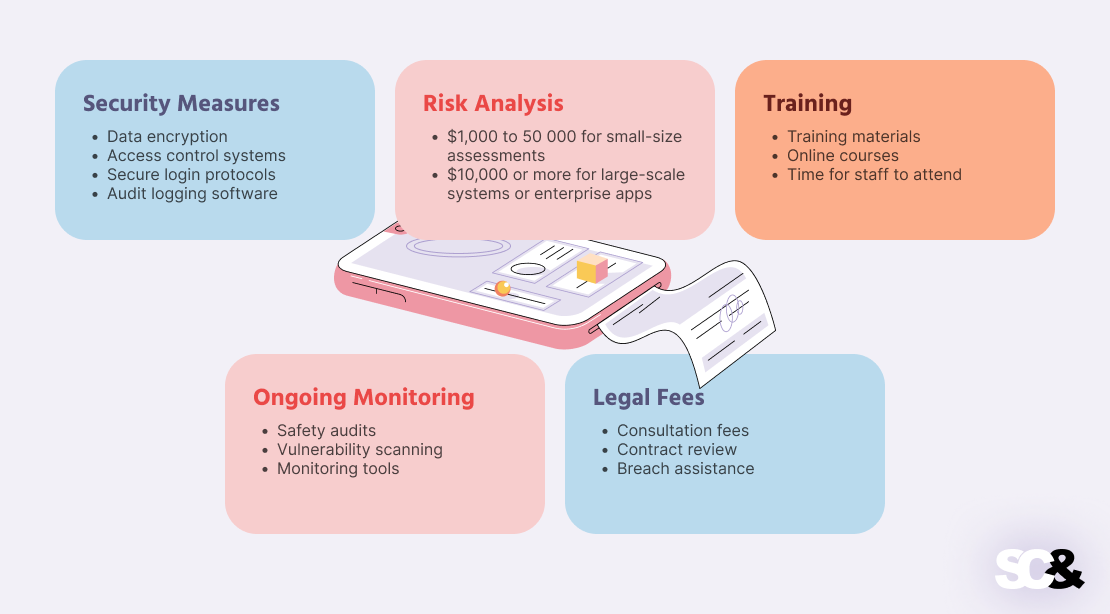
First, it’s worthwhile to contemplate the prices related to implementing the mandatory safety measures:
- Information encryption
- Entry management methods
- Safe login protocols
- Audit logging software program
- Safe cloud internet hosting providers (with signed BAAs)
Relying on the applied sciences concerned, these software program options may be costly to deploy, particularly for small companies. Spending on good safety, nonetheless, is the value you should pay for shielding delicate well being info and attaining compliance.
Then, there’s the expense of paying professionals to do a correct danger evaluation and audit your methods. Danger evaluation is a crucial side of HIPAA compliance that checks for weaknesses and enhancements wanted.
Most corporations choose to rent third-party auditors or safety consultants, who usually cost by the hour or have a flat charge. Charges differ however can vary from:
- $1,000 to $5,000 for small-size assessments
- $10,000 or extra for large-scale methods or enterprise apps
Additionally on the record is coaching your staff. Since HIPAA requires all staff to pay attention to learn how to deal with the protected well being info appropriately, you’ll must spend money on coaching periods. These bills usually embody:
- Drawing up or shopping for coaching supplies
- Paying for entry to on-line programs or certification instruments
- Giving time for workers to attend coaching periods
One other half to think about is the price of recurring monitoring and auditing. When you might have obtained compliance, you should keep your methods updated. This includes:
- Inside or outdoors security audits
- Successive publicity scanning
- Monitoring instruments to detect and react to doable breaches
Although these bills fluctuate, common inspections are crucial to stay in compliance and keep away from fines.
Lastly, don’t neglect authorized providers. You could have to work with attorneys to develop or negotiate Enterprise Affiliate Agreements (BAAs), and privateness insurance policies, or handle breaches. Authorized charges may embody:
- Session charges for HIPAA-related authorized questions
- Reviewing and updating contracts with distributors
- Help in case of an information breach or compliance concern
By and enormous, HIPAA compliance prices usually fall throughout the following 5 classes: implementation of safety, danger analyses, coaching of personnel, ongoing monitoring, and authorized charges.
Even though the general expense might sound excessive, the funding is important to safeguard affected person information, keep away from penalties, and acquire the belief of customers.
Profitable HIPAA-Compliant Apps You Can Consult with When Creating Your Software program
To higher perceive what it takes to make an app that adheres to HIPAA, let’s check out some examples of apps that efficiently adjust to HIPAA necessities.

These instances illustrate how completely different corporations have navigated completely different challenges in compliance and what issues you’ll be able to seek advice from when accumulating necessities to your personal utility.
Teladoc Well being
Teladoc is a prime US telemedicine platform with tens of millions of digital healthcare customers. Because the platform holds private medical info throughout video consultations, messages, and drug issuance, compliance with HIPAA is non-negotiable.
To stay compliant, Teladoc:
- Makes use of end-to-end encryption for all communication between suppliers and sufferers
- Enforces multi-factor authentication to safe person entry
- Has strict entry controls and audits all interactions involving PHI
General, Teladoc’s achievement is proof that irrespective of the dimensions, a medical platform can stay protected and handy to make use of with HIPAA mandates put on the core of its infrastructure and design.
MyChart by Epic Techniques
MyChart is a affected person portal that permits customers to assessment lab exams, schedule appointments, ship messages to docs, and handle drugs. When interacting instantly with clinics, hospitals, and different healthcare organizations, HIPAA compliance is a should.
Elementary HIPAA-priority options on MyChart embody:
- Position-based entry that limits what knowledge completely different customers (sufferers, physicians, admins) are allowed to see
- HIPAA-compliant safe messaging that meets HIPAA’s privateness and safety necessities
- Sturdy audit trails that assist observe entry to PHI
Epic’s method demonstrates how well being apps may be embedded with medical methods whereas nonetheless having sturdy knowledge privateness.
Doxy.me
Doxy.me is a telemedicine video conferencing software program of alternative for small practices and solo suppliers. In contrast to bigger enterprise-level methods, Doxy.me doesn’t compromise person expertise to develop into absolutely HIPAA compliant.
They accomplish this by:
- Providing BAAs to all paid plan customers
- Internet hosting all knowledge on HIPAA-compliant infrastructure
- Peer-to-peer video calls which are encrypted and don’t retailer PHI
Basically, Doxy.me exhibits that even easy purposes can obtain compliance wants with out over-complicating the person interface.
Future Tendencies in HIPAA Compliance and Healthcare App Improvement
As healthcare apps preserve pushing the boundaries with synthetic intelligence and distant affected person monitoring, knowledge safety might be extra consequential than ever earlier than.
First, privateness and safety should be prioritized by builders from the very starting of the event course of. This may imply producing software program that’s outfitted with sturdy encryption, authentication, and clear person permissions from the inception.
Extra well being apps may also be submitted to third-party audits sooner or later to adjust to HIPAA. Cloud suppliers will supply extra providers and instruments particularly designed to be HIPAA compliant.
On the similar time, as healthcare methods develop into extra depending on sharing knowledge, builders might want to show that knowledge is transmitted forwards and backwards securely and accessed by solely accepted people.
In different phrases, efficiently creating healthcare apps will imply that builders might want to keep on prime of latest expertise and by no means let their guard down in regard to defending affected person privateness and knowledge.
FAQs
What purposes want HIPAA compliance?
Any app that handles PHI and is utilized by healthcare suppliers, payers, or enterprise associates have to be HIPAA compliant. Telemedicine apps, EHR options, and medical billing apps come beneath this umbrella.
How a lot does HIPAA-compliant growth price?
Pricing varies however is often between $50,000 and $500,000 based mostly on safety necessities, integrations, and compliance auditing.
How typically ought to an utility be audited for HIPAA compliance?
Routine audits should be undertaken not less than yearly, with added evaluations when noteworthy updates or safety modifications are utilized.






