In cross-platform app growth, there are two highly effective frameworks that stand out from the remaining — .NET MAUI and Flutter. Each possess their very own set of robust factors, ecosystems, and use instances. On this article, we’ll evaluate .NET MAUI and Flutter intimately so you’ll be able to decide the higher one to your subsequent venture.
What Is .NET MAUI?
.NET MAUI (Multi-Platform App UI) is a cross-platform growth framework made by Microsoft that means that you can construct apps for Android, iOS, Home windows, and macOS utilizing a single codebase. It’s Xamarin reimagined, with a deal with delivering higher efficiency, a extra streamlined growth expertise, and full assist for .NET 6 and later.
MAUI makes use of C# and XAML to develop purposes, and the end result seems to be and acts like a local utility on all platforms. This single construction facilitates simpler growth, testing, and upkeep, making it simpler to construct and preserve apps on completely different platforms.
MAUI works carefully with the .NET ecosystem, so builders can use the instruments and strategies they already know. It additionally makes it simple to construct apps that appear like native ones on every platform, while not having to jot down separate code for iOS, Android, or Home windows.
What’s Flutter?
Flutter is a cross-platform open supply framework developed by Google. It permits the creation of purposes for cellular gadgets, net and desktop methods based mostly on a single code. The event relies on the Dart programming language, additionally created by Google particularly for quick and versatile work with person interfaces.
A latest 2023 developer survey reveals Flutter is the most well-liked cross-platform framework. About 46% of builders worldwide choose to make use of Flutter for cellular app growth.
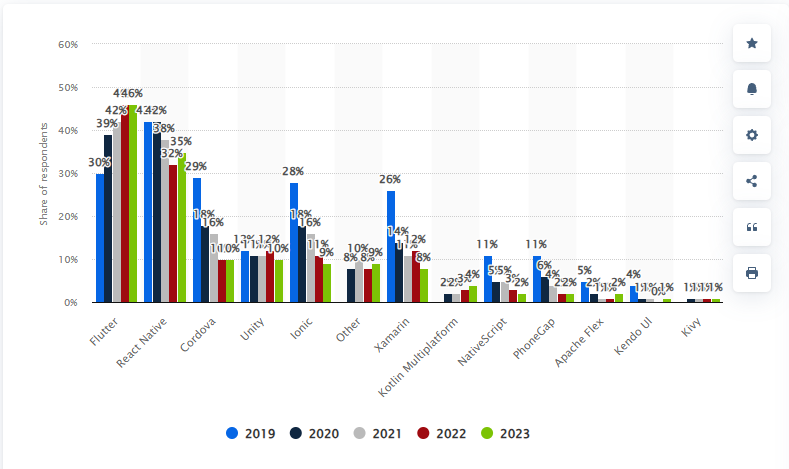
Cross-platform cellular frameworks utilized by software program builders worldwide from 2019 to 2023, Statista
Flutter works in a singular means. As an alternative of utilizing the default buttons and controls from every platform, it attracts every little thing itself. This offers builders full management over how issues look, and the app’s design stays the identical on all gadgets.
The framework makes use of reactive coding. The Flutter app display screen updates instantly when associated information modifications. Every thing in Flutter makes use of a single codebase strategy the place all parts work as widgets — from easy buttons to advanced layouts.
Flutter provides quick reload which immediately reveals app updates. This hastens the app growth course of and helps take a look at designs. Flutter additionally gives entry to native options by way of well-designed plugins, making cellular utility growth extra environment friendly.
Flutter vs .NET MAUI: Professionals and Cons
The selection between Flutter and .NET MAUI depends upon many components — from the technical necessities of the venture to the competencies of the crew. Each frameworks provide highly effective instruments for cross-platform growth however differ in strategy, efficiency, programming languages and supported platforms.
Beneath is a abstract comparability of the important thing benefits and limitations of Flutter and .NET MAUI that will help you consider which one is a more sensible choice to your subsequent utility.
Professionals of .NET MAUI
In the event you already work with .NET and write in C#, MAUI is nearly excellent. It really works nicely with different .NET instruments and gives entry to many ready-made libraries, so that you don’t must reinvent the wheel.
As well as, MAUI makes use of native UI parts, which implies your apps feel and look pure on any platform, be it Android, iOS, Home windows, or macOS. A handy venture construction helps you write the identical code for all gadgets and never waste time on typical cross-platform points.
Working turns into much more nice should you use Visible Studio: every little thing is at your fingertips — debugging and testing. With the assistance of a single API, you’ll be able to shortly entry machine capabilities, and most frequently you don’t even want to jot down separate code for every platform.
The new reload function is a lifesaver. You make a change within the interface and instantly see the end result with out restarting. It hastens debugging and design experiments.
Microsoft totally helps .NET MAUI growth as a key a part of .NET applied sciences. The platform will get common updates and new options. This gives security for longer tasks.
Cons of .NET MAUI
However, like several younger expertise, MAUI nonetheless has its personal flaws. It’s new and has fewer ready-made options, plugins, and documentation than extra mature frameworks. And should you haven’t labored with .NET earlier than, you’ll must work a little bit tougher to get used to it.

Pace is one other consideration. MAUI purposes are slower than native ones. This isn’t crucial for many duties, however when you’ve got a extremely loaded utility, it’s value holding in thoughts.
MAUI already has a group and it’s rising, however to this point it’s a lot smaller than Flutter. There are fewer ready-made options and specialised instruments too.
And never every little thing is so excellent with “write as soon as, run in all places”. Typically, particularly in advanced tasks, you continue to have to jot down separate code for every platform. In any other case, you received’t get the specified conduct.
Professionals of Flutter
Flutter is a good software for many who need to launch an app on all platforms without delay shortly and superbly. You write as soon as and it’s prepared for Android, iOS, and even the online. It saves time, cash, and nerves.
All due to the highly effective system of UI widgets, with the assistance of which you’ll be able to construct a cool interface with out pointless complications. Flutter takes care of each Materials Design and iOS requirements — every little thing will look neat and trendy.
One other benefit is the recent reload. In the event you change a line of code, you’ll be able to instantly see what you’ve bought. It is extremely handy to check concepts and shortly discover errors.
Google actively helps Flutter and releases updates and enhancements. The platform has a transparent growth plan, so that you don’t have to fret that it’ll all of a sudden be deserted. And due to its personal rendering engine, interfaces look equally good in all places — each on Android and iPhone.
The Flutter group is a separate story. It’s large, lively, and pleasant. 1000’s of plugins, tutorials, guides — and all that is continuously up to date.
One key benefit of Flutter is its excessive efficiency. It compiles straight into native code, with none intermediate layers like JavaScript. This implies much less lags, fewer ready, and extra person enjoyment.
Cons of Flutter
Nevertheless, not every little thing is ideal. Flutter makes use of the Dart language, which isn’t as well-liked as JavaScript or C#. In case your crew doesn’t realize it, you’ll have to spend time studying it. Nevertheless, those that are already accustomed to object-oriented programming is not going to discover it troublesome to get used to it.
There may be additionally a second with the dimensions of purposes — they develop into a bit heavier than, for instance, native options. This can be problematic for customers with restricted reminiscence or sluggish Web.
Typically, in an effort to use some native machine options, you’ll have to both search for third-party plugins or write platform-dependent code. This complicates the method a bit.
Apart from, new OS options don’t seem in Flutter instantly — it takes time for the crew to implement them. So if you wish to use the most recent iOS or Android function, you’ll have to attend.
One final thing: Flutter doesn’t use native interface parts, so if Android modifications the type of buttons, your app received’t decide it up robotically. You’ll must replace it manually. And customers who’re used to the native look might discover the distinction.
Efficiency Comparability: .NET MAUI vs Flutter
Each frameworks present good startup velocity and are appropriate for many purposes. Flutter wins in duties with wealthy UI and animations due to its personal rendering engine and direct pixel administration. .NET MAUI, then again, makes use of native UI parts, which helps save reminiscence and reduces system load in some eventualities.
Beneath we’ve ready a comparability desk for readability.
| Function | .NET MAUI | Flutter |
| UI Rendering | Makes use of native UI parts | Customized renderer (pixel-level management) |
| Animation | Much less optimized for advanced animations | Clean 60fps animations, optimized |
| Management Over Show | Entry to platform options | Direct management over display screen pixels |
| App Begin Time | Quick, with trendy velocity enhancements | Quick, with ahead-of-time (AOT) code |
| Reminiscence use | Could be extra memory-efficient with native parts | Might require extra reminiscence for customized rendering |
| Greatest Use Case | Platform-specific integration | UI-heavy apps, video games, and complicated visuals |
| Information-Heavy App Efficiency | Good efficiency | Good efficiency, depends upon community and database |
Efficiency Comparability of .NET MAUI and Flutter
When Ought to You Select .NET MAUI?
.NET MAUI is a good selection for tasks which are carefully tied to the Microsoft ecosystem or which are centered on operating on each cellular gadgets and Home windows. Beneath are the important thing eventualities by which this framework performs significantly nicely:
An excellent selection for .NET instructions
.NET MAUI brings nice outcomes for groups who know C# and .NET applied sciences nicely. It matches easily with Microsoft instruments that groups already use.
Help for Home windows-specific options
With .NET MAUI, builders can simply use particular options made only for Home windows. That is particularly useful for companies that need their apps to work nicely on each cellular gadgets and Home windows computer systems.
Integration with the Microsoft ecosystem
Microsoft Azure, SQL Server, and Microsoft 365 are greatest supported by MAUI apps. Help by the platform is made simple whereas coding. The framework makes the apps work together equally throughout platforms.
Native look on all platforms
.NET MAUI’s native UI elements give apps a local look on every platform. The apps naturally observe every platform’s design guidelines.
Entry to machine capabilities and {hardware}
.NET MAUI is greatest suited to apps requiring entry to native machine options and {hardware}. It provides a single methodology of accessing machine options whereas enabling platform-specific code when required.
When Ought to You Select Flutter?
Flutter is a strong software for creating visually intense, cross-platform purposes with a unified design and excessive growth velocity. It’s significantly nicely tailored for tasks the place quick launch, interface flexibility, and visible consistency throughout all gadgets are vital.

Good for Design-Pushed Apps
Flutter excels at creating apps with advanced UIs that want constant design throughout platforms. The widget system and direct rendering give exact UI management. Designers could make pixel-perfect seems to be on each machine.
Very best for Startups and Quick Launches
Flutter’s single codebase helps startup firms that want multi-platform apps with quick launch instances. This strategy saves money and time while you develop cross-platform apps.
Clean Animations and Visible Results
Flutter has gained reputation for dealing with advanced animations nicely. It gives clean 60fps movement that always seems to be jerky in different cross-platform instruments.
Constant and Responsive UI Throughout Screens
Consumer experience-focused apps choose Flutter for its superior UI instruments. Corporations discover it simpler to construct interactive UIs with Flutter’s many widgets. These hold the design constant throughout completely different display screen sizes.
Quick Iteration with Sizzling Reload
Flutter’s foremost benefit is how nicely it really works throughout tight growth schedules. The new reload function creates fast growth cycles with a clean workflow. Groups work extra effectively when testing and constructing options.
Energetic Neighborhood and Studying Sources
Flutter has a variety of documentation and rising group assist groups prepared to study Dart. Studying a brand new language takes endurance, however many teams discover that efficiency beneficial properties outweigh studying prices.
Ecosystem and Neighborhood Help
The supply of instruments and group exercise across the framework has a direct influence on the velocity of growth and the decision of points that come up.
Flutter has some of the actively rising communities amongst cross-platform frameworks. The official bundle repository — pub.dev — provides a variety of third-party options: from state administration instruments and extra UI elements to integrations with well-liked providers.
As well as, builders actively create tutorials, akin to guides, articles, and video tutorials. There are common occasions and meetups the place individuals share their experiences and data.
The .NET MAUI, in flip, is a part of the bigger .NET ecosystem. Though there are fewer specialised packages particularly for MAUI, builders can use an in depth library of ready-made .NET options.
The platform is formally supported by Microsoft: updates, patches and new options are launched usually, which is very vital for long-term and company tasks.
The standard of the documentation can also be vital: .NET MAUI has strong official documentation, and the .NET group is consistently including extra tutorials to it. Whereas the quantity of knowledge could also be smaller in comparison with Flutter, it’s normally extra structured and in-depth.
Which One to Select?
Deciding what’s the greatest answer for the venture’s targets and the crew’s expertise stack is a needed step.

.NET MAUI is right for tasks using C# and the Microsoft ecosystem primarily for just a few causes. It really works nicely in and with Visible Studio, making it an important choice for enterprise purposes, and is right when assist for Home windows is important.
Flutter is a good answer for colourful and visually sophisticated tasks, because it gives a fairly constant UI throughout completely different platforms developed inside a short while body and entry to an lively group with quite a lot of out-of-the-box options.
SCAND develops prime quality cross-platform purposes based mostly on .NET MAUI and Flutter. We provide help to outline your targets, technical necessities and venture timeline to decide on the most effective framework. From the planning section to launch and assist, we create sturdy, scalable options that exactly match your imaginative and prescient.
FAQ
Which framework is best for a cross-platform cellular app: .NET MAUI or Flutter?
There’s no one-size-fits-all reply when choosing the proper framework. Flutter’s unified codebase and higher UI options make growth extra environment friendly. This appeals to startups wanting visually wealthy apps. .NET MAUI and Flutter permit completely different approaches, however .NET MAUI’s Microsoft ecosystem integration and native elements go well with enterprise apps and C# groups higher. The proper selection depends upon your crew’s abilities and venture necessities.
Can I exploit .NET MAUI for Android and iOS apps?
Sure, .NET MAUI allows growth for 4 methods: Android, iOS, macOS, and Home windows. Builders use a single codebase to create cross-platform purposes for all 4 platforms. MAUI makes use of platform-specific renderers to make native UI elements for every system.
Which is quicker, .NET MAUI or Flutter?
Each present good velocity for many apps. Flutter works barely higher for graphics-heavy apps and animations as a result of it compiles on to native code and makes use of a customized rendering engine. MAUI’s native elements assist with platform-specific function integration. Most customers received’t discover velocity variations in typical apps.
Is Flutter tougher to study than .NET MAUI?
Your studying curve depends upon your background. Individuals who already know C# and .NET applied sciences will discover MAUI simpler to study. Flutter has detailed docs, and Dart’s design helps builders who know JavaScript or Java study it shortly.
What are the app measurement variations between Flutter and .NET MAUI?
Flutter apps are usually bigger as a result of they embrace the Flutter engine and framework. The smallest Flutter apps vary from 4-7MB for Android and 10-12MB for iOS after compression. .NET MAUI apps keep small for primary apps till including .NET libraries. Each frameworks use strategies like tree shaking and AOT compilation to cut back app measurement.
How do the communities evaluate between Flutter and .NET MAUI?
Flutter has a variety of group assist and reveals extra exercise. It provides many packages, plugins, and third-party sources. Whereas .NET MAUI is comparatively new in comparison with Flutter, it will get assist from Microsoft and builds on the massive .NET group. The variations between Flutter and .NET MAUI communities have an effect on how shortly you could find options to growth points.











