In context: A brand new hacking method raises issues about how cyber warfare and espionage proceed to evolve. As nation-state actors develop extra refined strategies, the road between bodily and digital safety turns into more and more blurred.
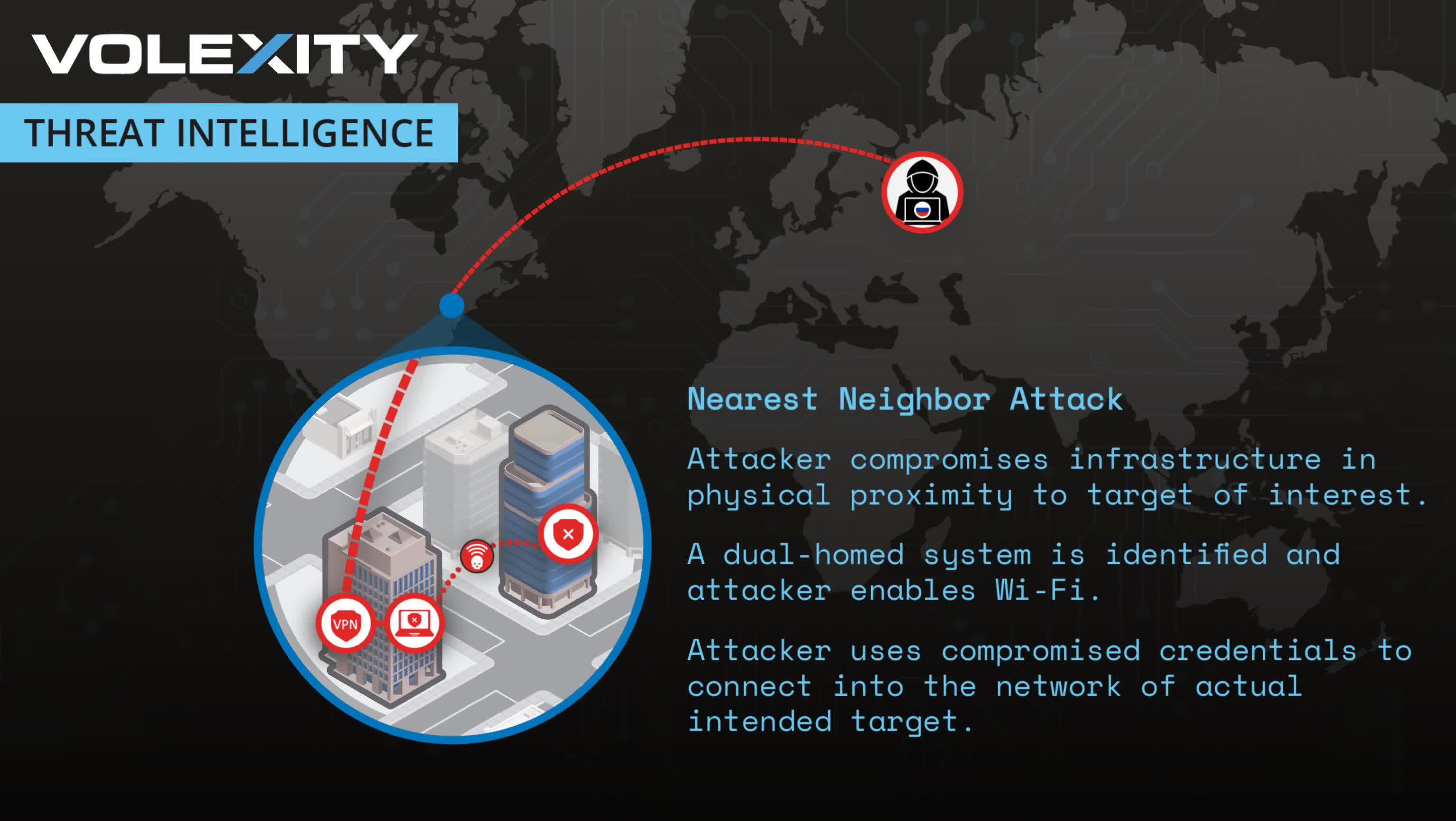
Russian hackers have devised a extremely refined technique of breaching Wi-Fi networks from afar that researchers have dubbed the “nearest neighbor assault,” because it permits hackers to infiltrate goal networks with out bodily approaching the premises.
The brand new method entails a multi-step course of that leverages vulnerabilities in neighboring networks to breach the supposed goal. As an alternative of risking detection by getting near the goal, as has been the norm in earlier Wi-Fi hacking makes an attempt, hackers can now orchestrate their assaults from a protected distance.
Cybersecurity agency Volexity uncovered this unprecedented Wi-Fi hacking method whereas investigating a community breach focusing on a buyer in Washington, DC, in 2022. The agency’s researchers traced the intrusion to a Russian hacker group recognized by varied monikers, together with Fancy Bear, APT28, and Unit 26165, a part of Russia’s GRU army intelligence company.
Wired notes that cybersecurity researcher Steven Adair revealed how his agency found this method on the Cyberwarcon safety convention held this week in Arlington, Virginia.
A “nearest neighbor assault” operates by way of a sequence of calculated steps. Hackers first breach a weak community in a constructing close to the supposed goal. They then achieve management of a laptop computer inside this compromised community. They use the gadget’s Wi-Fi from there to breach the focused community. This technique permits the attackers to stay bodily distant whereas exploiting native Wi-Fi vulnerabilities.
Within the case investigated by Volexity, the assault’s sophistication prolonged past a single soar. The researchers found proof of a daisy chain of Wi-Fi community breaches that concerned as much as three separate networks earlier than reaching the ultimate goal. The assault’s success hinged on a number of technical parts, together with credential exploitation, two-factor authentication bypass, and area title leakage. The hackers have been very decided, in line with Volexity, making a number of intrusion makes an attempt even after preliminary discovery.
This method is an evolution of the GRU’s earlier “close-access” hacking strategies. In 2018, officers caught Russian spies making an attempt to hack the Wi-Fi community of the Group for the Prohibition of Chemical Weapons in The Hague utilizing tools hidden in a automotive trunk. The “nearest neighbor assault” appears to instantly reply to the operational safety dangers uncovered by that incident.
This new assault vector presents important challenges for cybersecurity professionals. Organizations should now contemplate the safety of neighboring networks as a part of their risk panorama. The flexibility to conduct these assaults from afar will increase the potential pool of attackers and complicates figuring out who’s behind an assault.
In gentle of this new risk, cybersecurity consultants advocate a number of protecting measures, together with limiting Wi-Fi vary, obfuscating community names, implementing extra sturdy authentication protocols, and monitoring Wi-Fi entry factors, particularly these close to home windows or exterior partitions.
Cybersecurity consultants warn that nearest-neighbor assaults could change into extra prevalent. John Hultquist, a risk intelligence professional at Google-owned Mandiant, means that this method represents a “main enchancment” for close-access operations, and hackers are probably to make use of it extra ceaselessly.
Picture credit score: Volexity
