North Korean hackers have disguised malware in seemingly innocent macOS apps utilizing subtle code to bypass safety checks and goal unsuspecting customers.
In a current discovery, researchers at Jamf Risk Labs uncovered malware embedded in macOS apps that look innocent on the floor. Utilizing the favored app-building instrument Flutter, cybercriminals made apps that slipped by typical safety measures.
Flutter, developed by Google, has change into a favourite instrument for creating apps that work seamlessly throughout macOS, iOS, and Android. Its codebase permits builders to construct an app as soon as and have it look constant throughout all platforms.
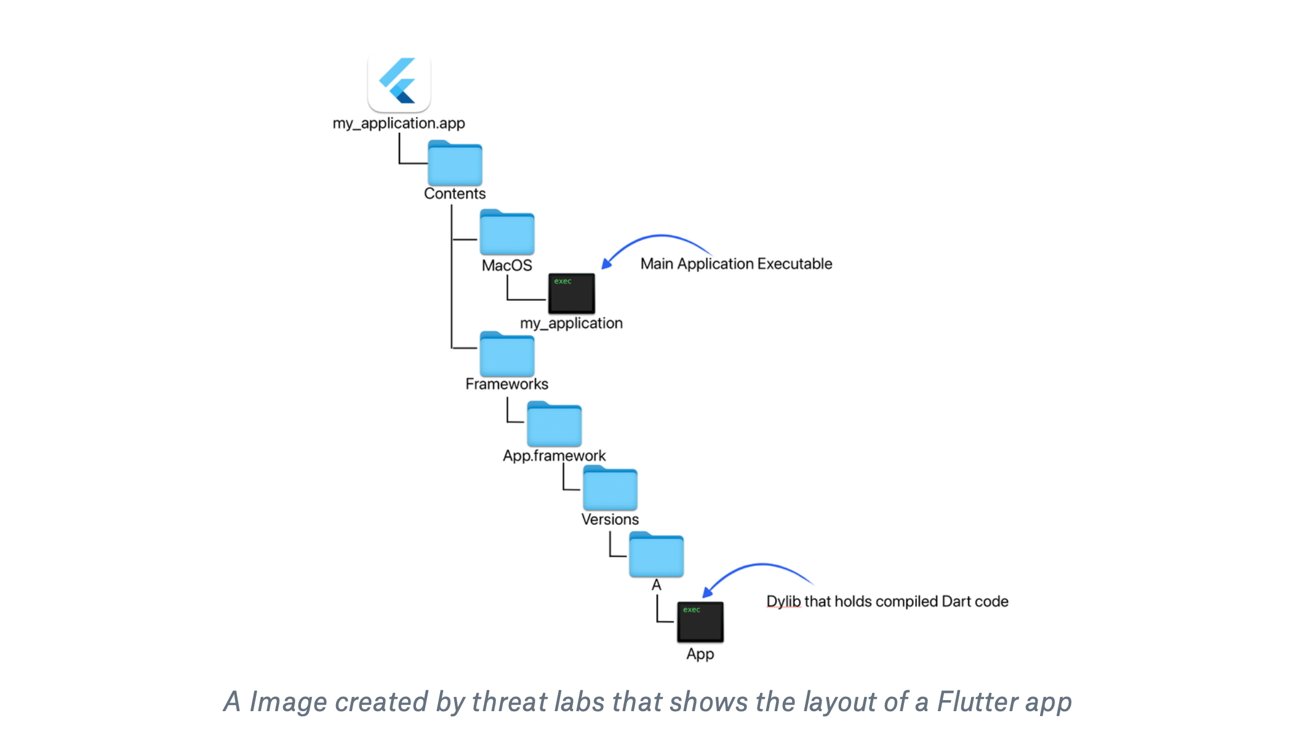
However Flutter’s distinctive setup may make issues tough — particularly when recognizing hidden code. In a typical Flutter app, the principle code (written in a language referred to as Dart) is bundled right into a “dylib” file, a dynamic library later loaded by Flutter’s engine.
Whereas nice for performance, that kind of code construction naturally obscures the code, making it tougher to examine. Hackers took benefit of this complexity, hiding malicious code in a method that is arduous to detect.
How you can macOS Flutter assault works
Jamf Risk Labs discovered three variations of the malware, every tailor-made to a distinct programming atmosphere — Flutter, Go, and Python. All three used comparable strategies to achieve out to exterior servers, believed below North Korean management, to execute further malicious instructions.
The Flutter-based malware centered on a misleading app named “New Updates in Crypto Trade.” The app gave the impression to be a easy recreation, inviting customers to play with out suspicion.
Nevertheless, hidden in its code was a operate that linked to a website beforehand linked to North Korean cyber operations. The operate enabled the app to obtain further malicious scripts able to remotely controlling an contaminated Mac.
In the meantime, the Python variant posed as a easy notepad app and linked to the suspicious area, downloading and operating malicious AppleScripts to remotely management the sufferer’s pc. Probably the most regarding components of the malware is its means to execute distant AppleScript instructions.
AppleScript is a instrument in macOS that automates duties and lets apps talk. The malware makes use of AppleScript to remotely management the system and carry out actions like capturing knowledge or putting in malware. Notably, the malicious scripts had been written backward to evade detection.
How you can defend your self in opposition to macOS Flutter malware
There is no indication but that these apps have been utilized in an precise assault, however the malware appears to be in a testing section. Given North Korea’s historical past of focusing on monetary sectors, cryptocurrency customers and corporations may very well be within the crosshairs.
Customers ought to obtain apps from Apple’s Mac App Retailer at any time when potential, as apps obtainable there endure safety opinions. Though not foolproof, the App Retailer’s screening course of reduces the chance of downloading dangerous software program.
By default, macOS permits customers to obtain apps solely from the App Retailer and recognized builders, a setting accessible within the “Privateness & Safety” part within the Settings app.
One other key step in staying safe is frequently updating macOS and put in apps, as Apple ceaselessly releases safety patches. Preserving gadgets and apps updated helps safeguard in opposition to newly found vulnerabilities.
Lastly, strategy cryptocurrency-related apps with warning, as hackers typically goal them utilizing faux variations. Apps that promise fast good points or “sound too good to be true” schemes might carry hidden dangers.