
A brand new Rust-based model of the Qilin (Agenda) ransomware pressure, dubbed ‘Qilin.B,’ has been noticed in assaults, that includes stronger encryption, higher evasion from safety instruments, and the flexibility to disrupt knowledge restoration mechanisms.
Qilin.B was noticed by safety researchers at Halcyon, who warned concerning the menace and shared indicators of compromise to assist with early detection.
Qilin updates its encryptor
Beginning with the brand new encryption scheme, Qilin.B customers AES-256-CTR with AESNI capabilities for CPUs that help it, rushing up the encryption.
Nonetheless, the brand new pressure retains ChaCha20 for weaker or older programs that do not have the suitable {hardware} for AESNI, making certain sturdy encryption in any case.
Qilin.B additionally incorporates RSA-4096 with OAEP padding for encryption key safety, making decryption almost unattainable with out the personal key or captured seed values.
Upon execution, the brand new Qilin malware provides an autorun key within the Home windows Registry for persistence and terminates the next processes to liberate essential knowledge for encryption and disable safety instruments.
- Veeam (backup and restoration)
- Home windows Quantity Shadow Copy Service (system backup and restoration)
- SQL database providers (enterprise knowledge administration)
- Sophos (safety and antivirus software program)
- Acronis Agent (backup and restoration service)
- SAP (enterprise useful resource planning)
Present quantity shadow copies are wiped to stop simple system restoration, and Home windows Occasion Logs are cleared to hinder forensic evaluation. The ransomware binary can also be deleted after the encryption course of has been accomplished.
Qilin.B targets each native directories and community folders and generates ransom notes for every listing processed, together with the sufferer ID within the title.
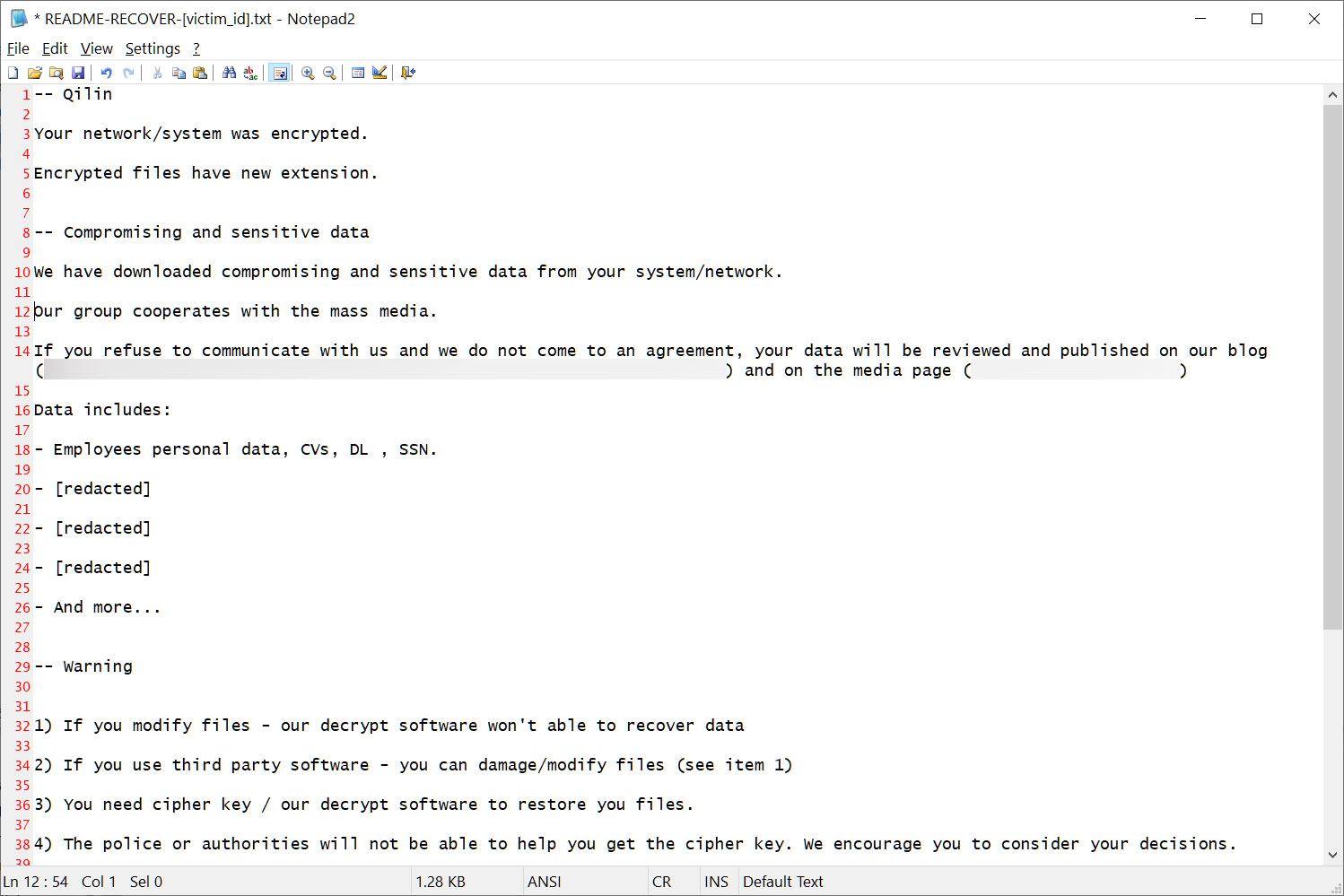
Supply: BleepingComputer
For max attain, it modified the Registry with a separate entry to allow sharing of community drives between elevated and non-elevated processes.
Though the above usually are not ground-breaking options within the ransomware area, they’ll have a extreme and far-reaching affect after they’re added to a household utilized by infamous menace teams in extremely efficient assaults.
Final August, Sophos revealed that Qilin deploys a customized info-stealer in assaults to gather credentials saved within the Google Chrome browser and prolong their assaults to total networks or re-introduce itself on breached networks even after cleanups.
Beforehand, Qilin was utilized in extremely damaging assaults in opposition to main London hospitals, Court docket Companies Victoria in Australia, and automotive big Yanfeng.
The group additionally makes use of a Linux variant targeted on VMware ESXi assaults, however the variant Halcyon noticed issues Home windows programs.

