
A novel acoustic assault named ‘PIXHELL’ can leak secrets and techniques from air-gapped and audio-gapped methods, and with out requiring audio system, by means of the LCD displays they connect with.
In a PIXHELL assault, malware modulates the pixel patterns on LCD screens to induce noise within the frequency vary of 0-22 kHz, carrying encoded indicators inside these acoustic waves that may be captured by close by gadgets equivalent to smartphones.

Supply: Arxiv.org
The researchers’ checks confirmed that information exfiltration is feasible at a most distance of two meters (6.5 ft), attaining an information charge of 20 bits per second (bps).
Whereas that is too gradual to make giant file transfers sensible, real-time keylogging and stealing small textual content information which may include passwords or different info are nonetheless doable.
Covert audio channel
PIXHELL was developed by Dr. Mordechai Guri of the Ben-Gurion College of the Negev, recognized for his in depth analysis in strategies to leak information from air-gapped environments.
Simply final week, the researcher printed one other paper on a novel side-channel assault dubbed “RAMBO” (Radiation of Air-gapped Reminiscence Bus for Offense) that may steal information from an air-gapped surroundings by producing digital radiation from a tool’s RAM parts.
The PIXHELL assault methodology takes benefit of the unintended acoustic emissions from LCD screens ensuing from coil whine, capacitor noise, or intrinsic vibrations that can not be bodily eradicated from the gadgets.
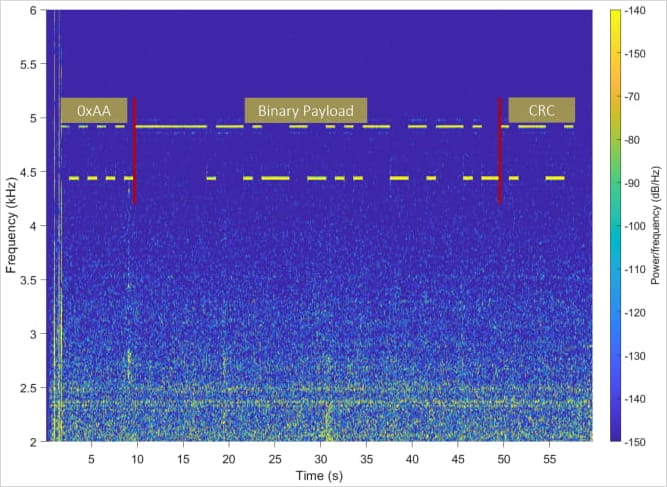
Utilizing specifically crafted malware, an attacker can encode delicate information like encryption keys or keystrokes into acoustic indicators utilizing modulation schemes equivalent to:
- On-Off Keying (OOK): Information is encoded by switching the sound on and off.
- Frequency Shift Keying (FSK): Information is encoded by switching between completely different frequencies.
- Amplitude Shift Keying (ASK): Information is encoded by altering the amplitude (quantity) of the sound.

Supply: Arxiv.org
Subsequent, the modulated information is transmitted through the LCD display by altering the pixel patterns on it, which alters the sound emitted from the machine’s parts.
A close-by microphone on a rogue or compromised machine equivalent to a laptop computer or smartphone can decide up the acoustic indicators and should later transmit them to the attacker for demodulation.
Supply: Arxiv.org
Notably, PIXHELL may be executed in a setting involving a number of sign sources and a single recipient, so it’s doable to seize secrets and techniques from a number of air-gapped methods concurrently, if these have been contaminated by malware.
The sound frequencies produced by the PIXHELL malware are sometimes within the 0 – 22 kHz frequency vary which is hardly audible to people. For comparability, people sometimes detect sounds in a frequency vary between 20Hz to 20kHz and a median grownup’s higher restrict is usually round 15-17kHz.
On the identical time, the pixel patterns used within the assault are low-brightness or invisible to the consumer, which makes the assault significantly stealthy.
Potential countermeasures
A number of defenses may be carried out in opposition to PIXHELL and different kinds of acoustic side-channel assaults. In extremely crucial environments, microphone-carrying gadgets needs to be banned fully from sure areas out of an abundance of warning.
Jamming or noise era, the place background noise is launched to disrupt the acoustic indicators and enhance the signal-to-noise ratio (SNR) to make the assault impractical, can also be an answer.
Dr. Guri additionally suggests monitoring the display buffer with a digicam to detect uncommon pixel patterns that don’t match the system’s regular operations.
Full technical particulars about PIXHELL assault and potential protection methods can be found within the technical paper titled PIXHELL Assault: Leaking Delicate Data
from Air-Hole Computer systems through ‘Singing Pixels’.
