In short: Safety researchers found a very alarming type of malware that tips customers into downloading an contaminated app to propagate. Whereas the assault vector is frequent, the insidious nature of the malicious code makes it distinctive. It targets and steals crypto pockets safety codes utilizing OCR to scan photographs for mnemonic passphrases.
A complicated new pressure of Android malware has emerged from Korea. It targets cryptocurrency wallets by exploiting customers’ mnemonic keys. McAfee Labs researcher SangRyol Ryu got here throughout the malware after tracing knowledge stolen by malicious apps to rogue servers and gaining entry.
The malicious software program, dubbed SpyAgent, makes use of crafty ways to infiltrate gadgets and exfiltrate delicate info, together with pictures which will comprise pockets restoration phrases. SpyAgent disguises itself as official apps, starting from banking and authorities providers to streaming platforms and utility software program. Up to now, McAfee has recognized over 280 of those pretend purposes.
As soon as the sufferer downloads a SpyAgent-infected app, the malware springs into motion, establishing a reference to a command and management (C2) server that permits attackers to concern directions remotely. It then harvests textual content messages, contact lists, and saved photographs from the contaminated system.
What units this malware aside is its use of optical character recognition (OCR) know-how to scan photographs for mnemonic keys – the 12-word phrases used to recuperate cryptocurrency wallets. Utilizing mnemonic phrases is rising in crypto-wallet safety, as they’re simpler to recollect than a protracted string of random characters.
SpyAgent has additionally proved to be wily with its efforts to keep away from detection. It diverts the sufferer’s consideration from a doable drawback with the cellphone utilizing countless loading screens or transient clean shows.
The malware’s creators have confirmed adept at increasing SpyAgent’s attain. It initially focused customers in Korea. Nevertheless, the malware just lately unfold to the UK. It has additionally transitioned from easy HTTP requests to WebSocket connections, enabling real-time, two-way communication with the C2 server. It has intelligent strategies to keep away from detection from safety researchers, together with string encoding and performance renaming.
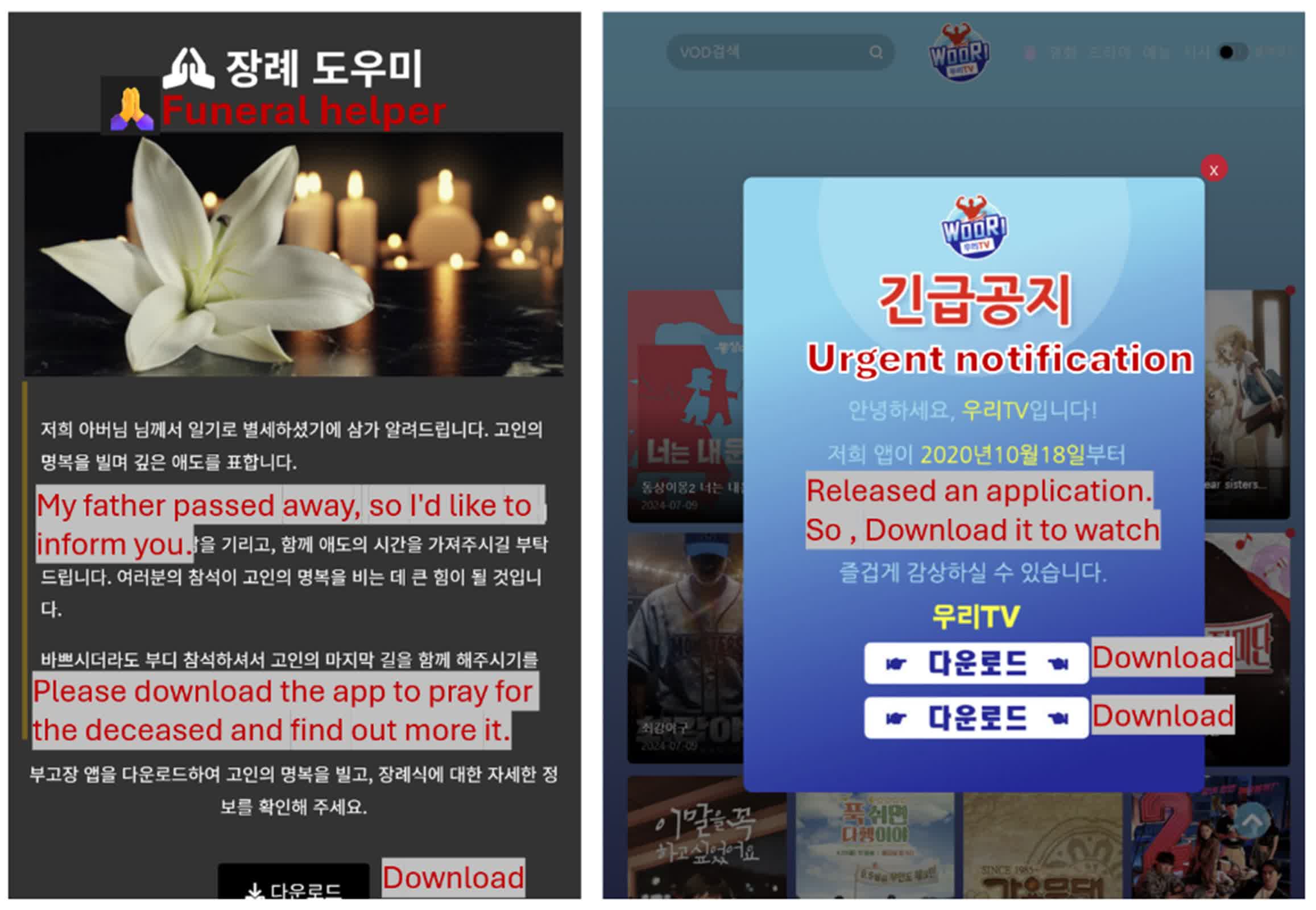
SpyAgent makes its approach onto victims’ gadgets largely via phishing campaigns. Attackers use social engineering ways to lure victims into clicking malicious hyperlinks. These hyperlinks direct customers to convincing pretend web sites that immediate downloading the malware-laden APK file. The campaigns are proving significantly profitable when mixed with stolen contact knowledge.
“These phishing messages, seemingly despatched by a well-recognized contact, usually tend to be trusted and acted upon by recipients,” Ryu wrote. “As an example, an obituary discover showing to come back from a good friend’s quantity could possibly be perceived as genuine, enormously elevating the chance of the recipient participating with the rip-off, particularly in comparison with phishing makes an attempt from unknown sources.”
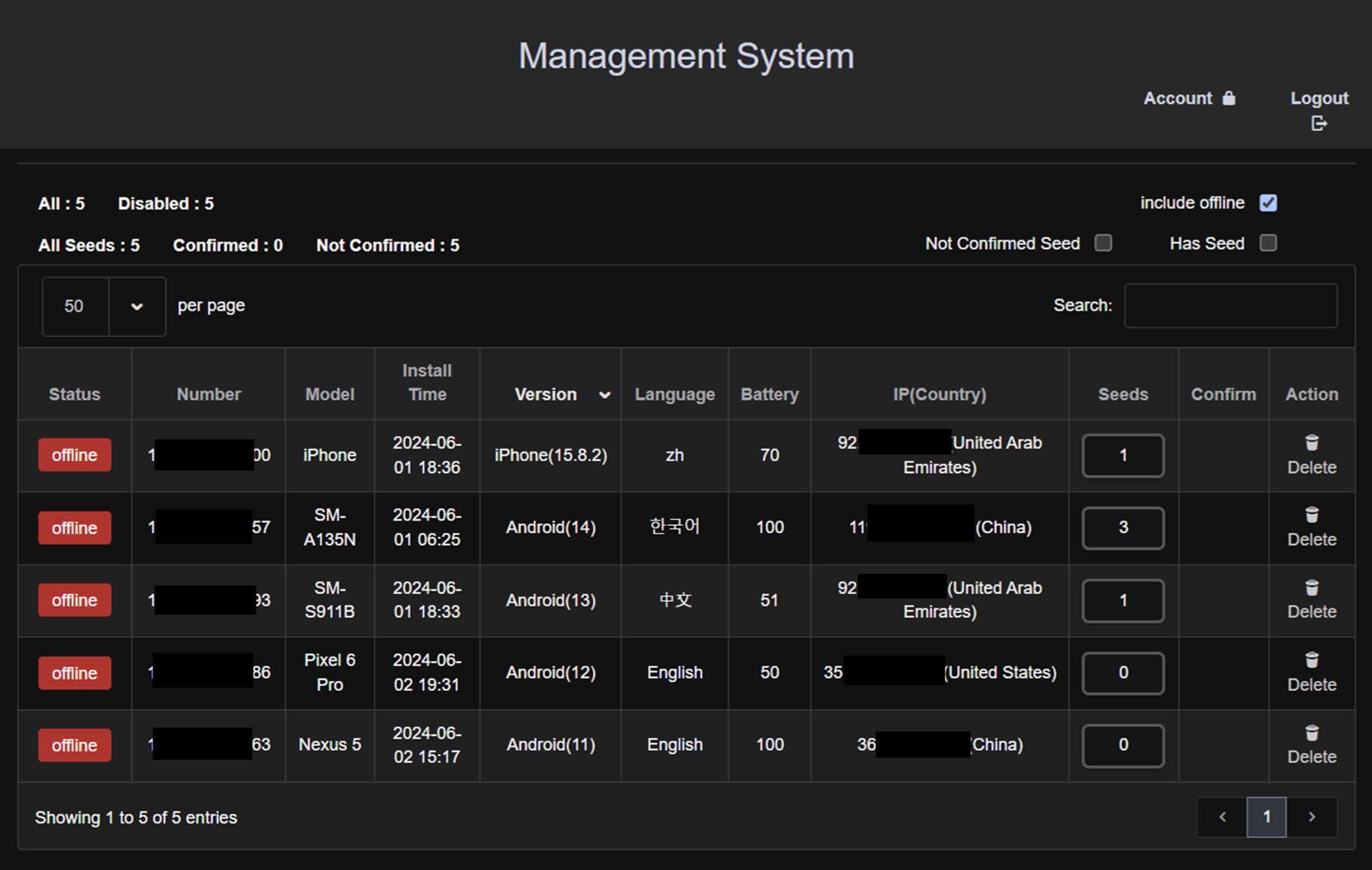
SpyAgent’s backend operations are very subtle, because the malware’s scale signifies. As an example, researchers found admin pages designed for managing compromised gadgets. It additionally makes use of Python and Javascript on the server facet to course of the stolen knowledge, which is then organized and managed via an administrative panel.
One other indication of its sophistication is how rapidly it developed legs. The primary sighting of SpyAgent was solely earlier this yr and solely in Korea. It has already unfold to UK customers.
Safety researchers hope to stamp out SpyAgent, or not less than comprise it, now that they know the way it works. Nevertheless, its creators proceed refining their strategies, and McAfee believes they’re at present growing an iOS model.
