Again in Could 2023, I wrote the blogpost You might not care the place you obtain software program from, however malware does as a name to arms, warning in regards to the dangers of operating software program downloaded from so-called “trusted sources” of pirated software program. In fact, these information have been something however reliable and contained malware, corresponding to ransomware or infostealers, particularly focused at that demographic. My hope was that by educating the general public in regards to the dangers concerned, individuals would study find out how to keep away from such harmful apps and search safer alternate options.
Within the 12 months or so since that blogpost, issues haven’t gotten significantly better: From studying the ESET Menace Report for the first half of 2024, we have now seen a marked enhance within the variety of data stealers being detected. And this time, they aren’t simply embedded in pirated Home windows video games, cracks, and dishonest instruments, but in addition impersonating generative AI instruments. Nor are they restricted to Home windows, both. The GoldDigger household of information-stealing malware runs on Android OS, and the long-running Ebury malware marketing campaign has been energetic in stealing bank cards, cryptocurrencies, and SSH credentials for over a decade on UNIX-like working techniques.
infostealer detections over a two-year interval, from August 2022 to August 2024, exhibits they remained energetic all through this era, though there have been noticeable drops in exercise round December and January of every 12 months.
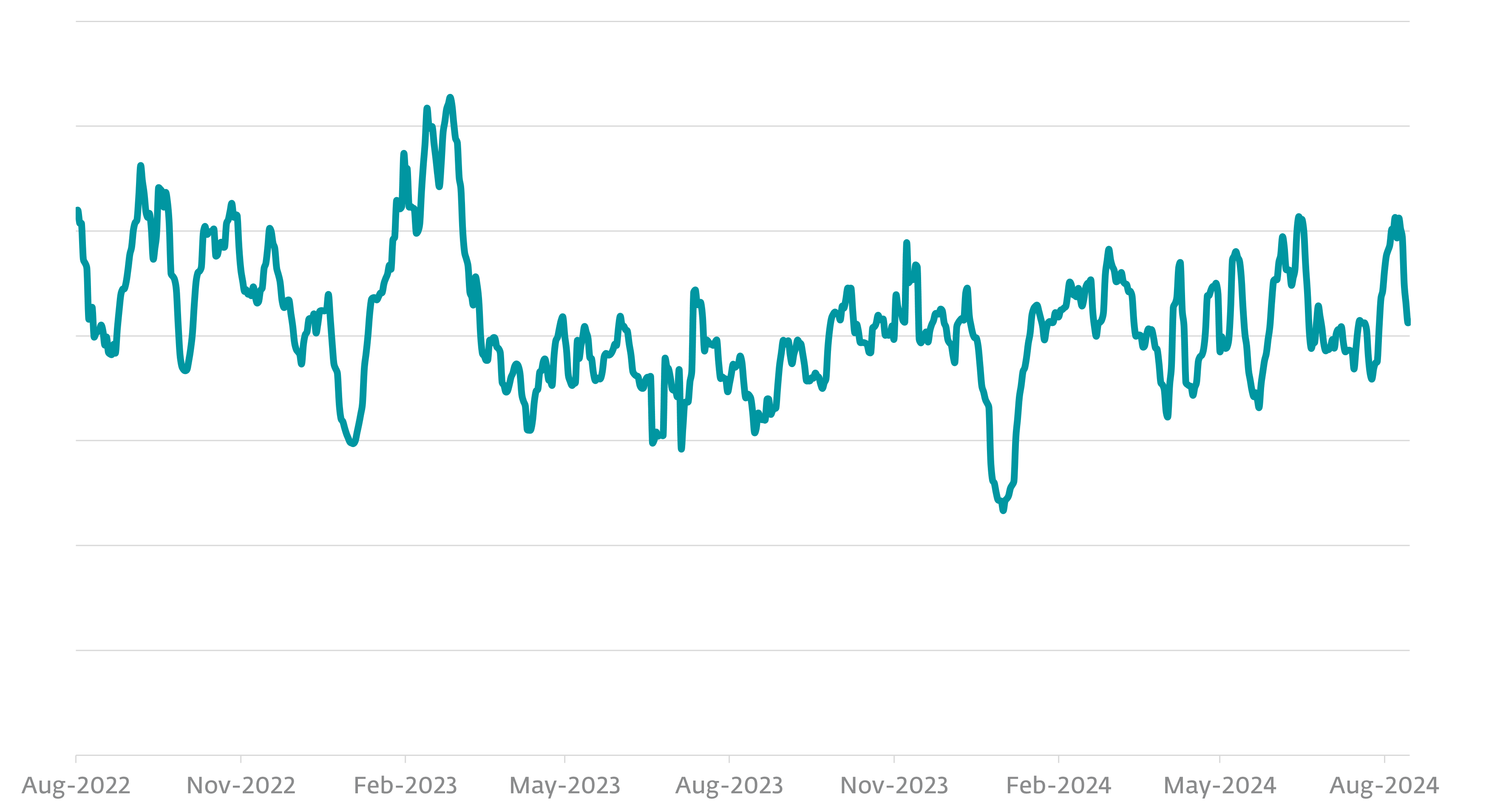
We’re unsure of the precise purpose for this, however speculate that it could be as a result of decreased laptop utilization by the victims or their attackers taking a break for the vacations, which has change into widespread as particular person felony hackers have morphed into organized felony enterprises, resembling one thing like companies.
Whereas ESET acknowledges many households of infostealers, the highest ten account for simply over 56% of these detected by ESET, with Agent Tesla on the prime, with 16.2%.
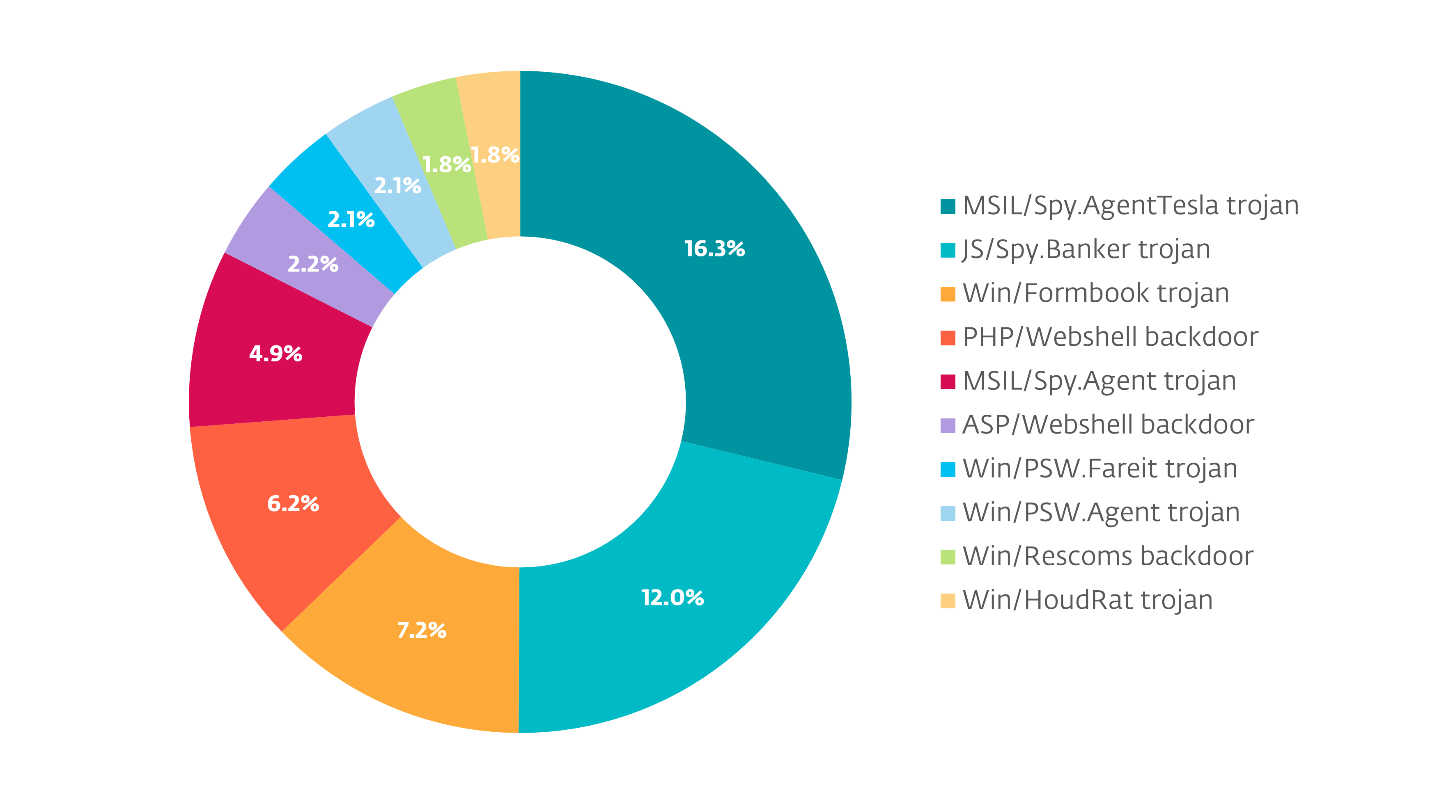
One factor to remember is that whereas most of those detections are for Home windows-based malware, there are data stealers which can be net primarily based as effectively. Though they’d decrease encounter charges, it’s doable that they have been capable of efficiently steal data from individuals not operating ESET software program, so their impression could also be better.
Protecting in thoughts that these statistics are derived from ESET telemetry knowledge, it’s doable that different safety firms’ knowledge could present totally different outcomes. This isn’t as a result of anybody being higher than one other however the results of components corresponding to classifying threats in another way, having totally different buyer bases with very totally different threat profiles, utilization below totally different circumstances, and others.
All of which suggests we will all report totally different encounter charges for varied sorts of malware, corresponding to data stealers.
One of many issues I used to be inquisitive about was whether or not ESET’s knowledge was much like that of different safety firms. As one instance, in their malware traits report for the second quarter of 2024, sandbox vendor ANY.RUN famous that data stealers dropped from first place to fourth place from the previous quarter. Now, this doesn’t imply that there’s any distinction in knowledge high quality between ESET and ANY.RUN. There’s a broad ecosystem of safety instruments on the market, and with every firm’s instruments utilized in fairly numerous methods, these kinds of variances in reporting are to be anticipated.
Info stealing for enjoyable however largely revenue
ESET classifies data stealers below their very own separate menace class of Infostealer. Initially, they have been categorized below extra basic names corresponding to Agent or Trojan till the amount of packages participating in information-stealing exercise elevated to the purpose that it made sense to cluster them below their very own nom de plume. Different safety software program builders could classify them extra broadly as distant entry trojans or adware, which is completely acceptable, too. The purpose of detecting malware is to forestall it at first. The naming of these threats and the taxonomies below which they’re labeled is usually unimportant exterior of analysis actions or advertising and marketing actions in response to a mass malware outbreak, corresponding to WannaCryptor.
So, with all of that in thoughts, what precisely is an data stealer, and what occurs while you run one?
Because the title implies, one of these malware steals any data it may discover in your laptop that its operator considers of worth. This consists not simply of usernames and passwords for varied web sites accessed through the net browsers put in in your PC, but in addition these for functions. Recreation accounts could be stolen, looted of helpful objects, used to make present purchases, or resold of their entirety. Streaming media could be resold, as can e mail and social media accounts. As an “added bonus”, the latter can use your account to entice on-line associates into downloading and operating the knowledge stealer, turning into new victims to it, and having its puppeteers unfold it from these accounts as effectively, advert infinitum.
It’s not simply usernames and passwords that get stolen, both. Wallets for cryptocurrencies could be particularly profitable, as can account session tokens. For that matter, the knowledge stealer could even take a screenshot of the desktop on the time it was run in order that its operator can promote the screenshot and e mail handle to different criminals for sending rip-off extortion emails later.
In case you’re questioning what a session token is, some web sites and apps have a “bear in mind this gadget” characteristic that means that you can entry the service with out having to log again in or enter your second issue of authentication. That is finished by storing a session token in your gadget. One can consider it as being a specialised type of net browser cookie that tells the web site being visited (or service being accessed by means of an app) that the person has been efficiently authenticated and to permit them in. Criminals search for and goal these, as a result of they permit them to log into an account, bypassing the traditional checks. So far as the service is anxious, it simply seems such as you’re accessing it out of your beforehand licensed gadget.
The enterprise of data stealing
Info stealers are a sort of malware that’s usually offered as a service, so what precisely it did whereas on a pc goes to fluctuate a bit primarily based on what the felony who bought it wished it to search for and steal. Typically, they take away themselves after they’ve completed stealing data in an effort to make it tougher to find out what occurred and when. If the sufferer is feeling so overwhelmed by the invasion of their privateness that they delay taking fast motion, it provides the criminals extra time to make use of or fence the knowledge stolen from the pc.
However since data stealers are crimeware-as-a-service, it’s also doable that it was used to put in extra malware on the system in an effort to keep entry to it, simply in case the criminals resolve to come back again to the pc sooner or later and see if there’s something new to steal from it.
Restoration from an information-stealing assault
Except the pc’s drive(s) have to be preserved as proof, the very first thing to do could be to wipe the pc’s drive and reinstall its working system. That assumes the pc was backed up frequently, so erasing its drive(s) and dropping all the knowledge saved on it (them?) isn’t an enormous deal, since it’s already backed up elsewhere. If that’s not the case, and there’s helpful, vital knowledge saved on the pc, it could make sense to take away its drive(s), change it with a clean one, and carry out a clear set up of the working system to that. Getting some type of exterior case to place the drive in later to repeat the non-backed up knowledge off of it will likely be vital as effectively.
After wiping the pc, putting in Home windows, putting in safety software program, and getting all of that up to date, one can then begin accessing the web utilizing the pc to vary the passwords for all the on-line accounts that have been ever accessed from it.
Every password must be modified to one thing that isn’t solely advanced but in addition totally different for every service. Merely changing Summer2024 with Autumn2024, or P@ssW0rd123 with P@ssW0rd1234 is one thing an attacker may simply guess after reviewing your whole stolen passwords. That means, if one is misplaced (or guessed), the attacker gained’t be capable to make guesses about what the opposite passwords may be. A few of ESET’s subscriptions include a password supervisor, or your net browser could have one which’s constructed into it. ESET additionally presents a free instrument for producing advanced passwords.
Enabling two-factor authentication (generally known as multi-factor authentication) for all the accounts that help it should make it exponentially tougher for attackers to compromise sooner or later, even when they know the passwords to them.
When altering passwords, it is very important make them distinctive or totally different from any beforehand used passwords: if the brand new passwords are related sufficient to the previous passwords, a felony who has all of the previous passwords will very possible be capable to make all kinds of educated guesses about what the brand new passwords may be for the assorted companies. So, be sure you’re not biking by means of similar-sounding or earlier passwords.
As talked about earlier, it’s not simply passwords you must change, however session tokens as effectively. These are focused by information-stealing malware as a result of they permit criminals to impersonate you by hijacking certainly one of your beforehand licensed periods. Some web sites and apps have the flexibility to indicate you different energetic periods or gadgets on which you accessed them, but in addition to sign off or disconnect these different energetic periods. Do this as effectively.
On the threat of sounding considerably repetitive, it is very important do that for each single on-line service. Even ones which can be not frequently used. That is extraordinarily vital for any monetary web sites, on-line shops, social media, and e mail accounts, since these are among the many most respected to criminals. If there have been any reused passwords and even related themes between them, the criminals who stole the credentials are going to attempt spraying them in opposition to all of the widespread shops, banks, and companies.
Two of the underlooked actions when recovering from an information-stealing assault are to (1) file a report with the police; and (2) notify your monetary establishments. Making legislation enforcement conscious {that a} crime has occurred could also be useful in recovering stolen accounts. Within the case of monetary establishments, having a police report back to share with them can enhance the possibilities of getting again stolen funds. Even in case you are not in the USA, submitting a report with the Web Crime Compliant Middle (IC3) might help legislation enforcement companies establish and observe information-stealing criminals.
Defensive methods
Coping with the aftermath of an data stealer assault is an extended and painful course of that may drag on for days, weeks, and even months. Whereas we have now introduced the fundamentals wanted to begin the method of recovering from such assaults, data stealers are neither the only nor probably the most broadly occurring technique of getting one’s accounts stolen. The locks and keys for our on-line identities are usernames (which are sometimes e mail addresses) and passwords, and knowledge breaches involving these have change into more and more widespread.
Having establish theft safety might help mitigate a number of the worst features of this type of violation, however like having an insurance coverage coverage (or backups of their laptop’s knowledge), it’s one thing lots of people don’t contemplate till after one thing unhealthy occurs to them.
One wonderful supply of discovering out whether or not your e mail handle has been concerned in an information breach is Troy Hunt’s Have I Been Pwned (HIBP) web site, which consistently receives up to date details about knowledge breaches which have occurred all around the globe and can notify you in case your e mail handle has been present in any of them. Whereas that doesn’t essentially imply your e mail account itself is in any hazard, it may imply the account may very well be on the service from which it was leaked. The HIBP service is free for people.
Knowledge breaches could be troublesome to keep away from, since they’re the results of securing points involving third events. Info stealers, then again, are typically the results of participating in dangerous habits. Listed below are some steps you’ll be able to take to scale back the impression and get well extra shortly from these kinds of assaults:
- Use lengthy and totally different passwords for every web site and utility. A password supervisor can significantly ease this advanced course of for you.
- Allow two-factor authentication for all companies that permit it. {Hardware} tokens or smartphone apps are safer than e mail or SMS notification, as an attacker could have entry to your e mail or smartphone.
- Some companies allow you to see all of the gadgets logged into your account. Periodically evaluate these and disable ones that you don’t acknowledge or haven’t been energetic for some time.
- Use an information breach monitoring or an identification theft safety service to inform you of compromised accounts.
- Do not use pirated software program, cracks, keygens or related instruments irrespective of how reliable you contemplate them. It’s trivial to make these seem secure and trusted when criminals have stolen the accounts ranking them.
- Hold your working system and functions updated with the newest totally patched variations.
- Use the newest model of safety software program from trusted, established distributors.
- Hold updated on the newest safety traits, points and information out of your favourite data safety blogs.
Following these can scale back the possibilities of turning into a sufferer, or enable you get well extra shortly within the occasion that you’ve got change into one.
