The cybersecurity panorama witnessed a big growth when the Nationwide Police Company (NPA) and the Nationwide middle of Incident readiness and Technique for Cybersecurity (NISC) launched a safety advisory on January 8, 2025.
This advisory highlighted an Superior Persistent Menace (APT) marketing campaign performed by a gaggle generally known as “MirrorFace,” focusing on organizations in Japan.
The risk actors cleverly exploited Home windows Sandbox and Visible Studio Code as a part of their assault methodology.


This text presents a complete evaluation of the Home windows Sandbox exploitation approach, drawing from technical verification analysis, to offer insights into the assault methodology, forensic artifacts, and important countermeasures that safety professionals can implement to detect and stop such assaults.
Understanding Home windows Sandbox and Its Safety Implications
Home windows Sandbox is a built-in virtualization function out there in Home windows 10 (Construct 18342 and later) and Home windows 11 that creates an remoted, momentary desktop setting.
This light-weight digital machine permits customers to run probably unsafe purposes with out risking everlasting adjustments to their host system.
By default, Home windows Sandbox is disabled and requires specific activation by means of both the graphical person interface or command-line interface.
As soon as enabled, it offers an setting that runs below a default person account named WDAGUtilityAccount, which notably belongs to the Directors group.


This administrative privilege inside the sandbox setting creates a big safety consideration that attackers have realized to take advantage of.
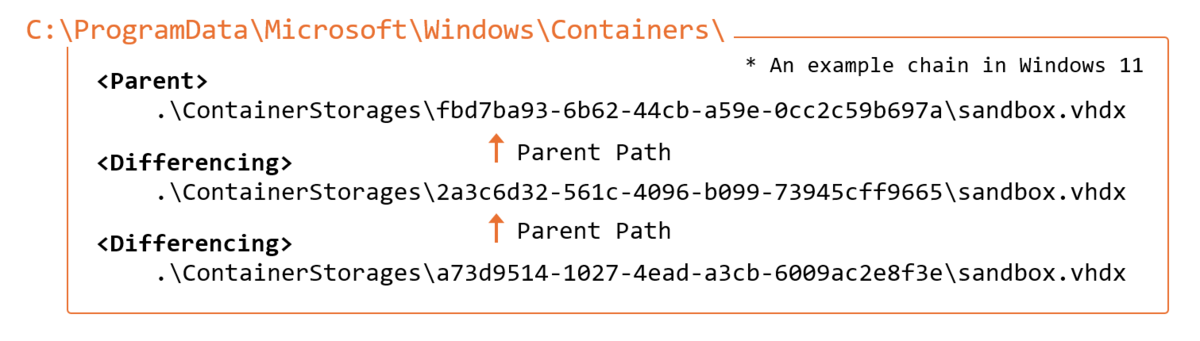
The sandbox makes use of Digital Arduous Disk (VHDX) expertise and employs a differential backup mechanism. When launched, it creates VHDX-related folders below C:ProgramDataMicrosoftWindowsContainers, containing each dad or mum and differential digital disks.

C:ProgramDataMicrosoftWindowsContainers folderA key safety limitation inside the sandbox is that Home windows Defender is disabled by default and can’t be enabled by means of both GUI or PowerShell instructions.


This protecting hole creates an opportune setting for malware execution with out safety product interference.
One other necessary side is the aptitude to configure Home windows Sandbox by means of WSB information – XML-based configuration information that may outline community entry, folder sharing between host and sandbox, automated command execution at startup, and useful resource allocation parameters.
The safety implications of Home windows Sandbox change into significantly regarding when contemplating latest purposeful updates.


As of October 24, 2024, Microsoft launched KB5044384, introducing important adjustments to Home windows Sandbox performance, together with the addition of wsb.exe command for command-line management, background execution functionality, and GUI-configurable settings.
These enhancements, whereas bettering professional use circumstances, concurrently make detection of malicious sandbox actions more difficult.
Essentially the most regarding developments embody the power to run the sandbox within the background with out person consciousness, configuration with out traceable WSB information, and persistence of information inside the sandbox setting till explicitly terminated.
MirrorFace’s Subtle Assault Methodology
The risk actor MirrorFace, believed to be a subgroup inside the broader APT10 umbrella, developed a complicated assault methodology leveraging Home windows Sandbox as a stealth mechanism.
Their assault marketing campaign utilized LilimRAT, a personalized model of the open-source Lilith RAT.
This malware was particularly designed to function inside Home windows Sandbox, as evidenced by its code that checks for the existence of the WDAGUtilityAccount person folder – terminating if this folder is just not discovered.
This deliberate design alternative demonstrates the attackers’ focused method to utilizing Home windows Sandbox as an operational setting.
The assault circulate begins after the preliminary compromise of a goal system, the place the risk actors allow Home windows Sandbox, which requires administrative privileges, adopted by a system restart.


They strategically place three key parts on the compromised host: a batch file, an archiver utility (similar to 7-Zip), and an archive file containing the malware payload.
The attackers then create and execute a WSB configuration file that establishes folder sharing between host and sandbox, permits community connectivity, allocates reminiscence assets, and most critically, robotically executes the batch file upon sandbox startup.
This batch file usually comprises instructions to extract the archive, create a scheduled activity that executes the malware with SYSTEM privileges, and run the scheduled activity.
What makes this method significantly insidious is that when Home windows Sandbox is executed through Activity Scheduler below a distinct person account (similar to SYSTEM), it runs within the background with out displaying a window, successfully concealing its operation from customers.
The malware executed inside this remoted setting communicates with command and management (C2) servers through the Tor community, encrypting communications and obscuring the C2 infrastructure.
For the reason that malware operates inside the sandbox in keeping with the WSB configuration, it may possibly entry information on the host machine whereas evading monitoring instruments that solely observe host system actions.
Moreover, the absence of Home windows Defender inside the sandbox setting permits attackers to function with out safety product interference.
The latest Home windows Sandbox function updates have additional enhanced the attackers’ capabilities.
The brand new wsb.exe command-line performance permits for background execution with out seen home windows, configuration with out traceable WSB information, and chronic knowledge storage till specific termination.
These developments considerably enhance the assault floor and complicate detection efforts for safety professionals.
Efficient Monitoring, Investigation, and Mitigation Methods
Defending in opposition to Home windows Sandbox exploitation requires a multi-layered method encompassing monitoring, forensic investigation, and preventive controls.
On the monitoring entrance, a number of processes related to Home windows Sandbox will be tracked to detect its activation: WindowsSandbox.exe, WindowsSandboxClient.exe, cmproxyd.exe, and in newer Home windows 11 builds, WindowsSandboxServer.exe, WindowsSandboxRemoteSession.exe, and wsb.exe.


Since Home windows Sandbox makes use of the host machine’s community adapter, normal community monitoring stays efficient for detecting communication with C2 servers, although further detection mechanisms for Tor community site visitors could also be crucial when this anonymity community is employed.
An necessary discovery for detection is that sandbox processes are executed inside the reminiscence house allotted to the host machine.
Particularly, strings and artifacts from processes working contained in the sandbox will be discovered inside the vmmemWindowsSandbox course of (Home windows 11) or vmmem course of (Home windows 10) on the host machine.
This offers a important alternative for safety instruments to scan these reminiscence areas for indicators of compromise, even when the malicious actions are confined to the sandbox setting.
Reminiscence scanning of those processes can probably detect malware and assault instruments that may in any other case stay hidden.
From a forensic investigation perspective, a number of artifacts can present proof of Home windows Sandbox exercise.
On the host machine, the Grasp File Desk ($MFT) and Replace Sequence Quantity Journal ($UsnJrnl) might file the creation of WSB information, mounted folders, and VHDX information.
Prefetch knowledge would possibly comprise information of WSB and VDHX file loading, whereas the Home windows Registry comprises utility associations associated to Home windows Sandbox.


Occasion logs may also present helpful details about sandbox activation and utilization.
Extra importantly, if VHDX information are recovered whereas sustaining the dad or mum and differential digital disk chain, they are often mounted for complete evaluation of sandbox actions.
Throughout the mounted sandbox setting, investigators can entry helpful artifacts together with $MFT, $UsnJrnl, Registry, browser historical past, and occasion logs, although some knowledge sources like Prefetch and SRUM should not out there.
For preventive management measures, organizations ought to think about conserving Home windows Sandbox disabled by default and implementing strict person privilege administration to forestall unauthorized activation.
Since enabling Home windows Sandbox requires administrative rights, proscribing administrative privileges can successfully block this assault vector.
Moreover, AppLocker insurance policies will be deployed to forestall Home windows Sandbox execution even when it’s enabled or when customers have permission to allow it.
When AppLocker blocks Home windows Sandbox, these occasions are recorded within the occasion logs, offering a further detection mechanism.


The exploitation of Home windows Sandbox by the MirrorFace APT group represents a complicated evolution in assault strategies that leverage professional working system options to evade detection.
By working inside an remoted setting that runs with administrative privileges however lacks safety controls, attackers can execute malware, entry host system information, and talk with C2 infrastructure whereas minimizing their digital footprint.
Are you from SOC/DFIR Groups?: Analyse Malware Incidents & get dwell Entry with ANY.RUN -> Begin Now for Free.
