
The Microsoft 365 Admin Portal is being abused to ship sextortion emails, making the messages seem reliable and bypassing e mail safety platforms.
Sextortion emails are scams claiming that your pc or cellular gadget was hacked to steal photographs or movies of you performing sexual acts. The scammers then demand from you a fee of $500 to $5,000 to forestall them from sharing the compromising photographs with your loved ones and mates.
Whilst you would assume nobody may fall for these scams, they have been very worthwhile after they first appeared in 2018, producing over $50,000 every week. To at the present time, BleepingComputer continues to obtain messages from folks involved after receiving them.
Since then, scammers have created quite a few variants of extortion e mail scams, together with ones that faux to have caught your partner dishonest or embrace photos of your property to scare you into paying the extortionist in Bitcoin.
Nonetheless, e mail safety platforms have change into good at detecting these rip-off emails and sometimes quarantine them within the spam folder.
Abusing the Microsoft 365 Admin Portal for scams
Over the previous week, folks on LinkedIn, X, and the Microsoft Solutions discussion board reported receiving sextortion emails via the Microsoft Message Heart, permitting the scams to bypass spam filters and land within the inbox.
“I acquired an extortion rip-off e mail yesterday. These items normally find yourself in junk/spam, nevertheless this one made it previous the filters because it was despatched by Microsoft 365 Message Heart.
“Any concepts on how they’d have managed to do that?”requested cybersecurity skilled Edwin Kwan.
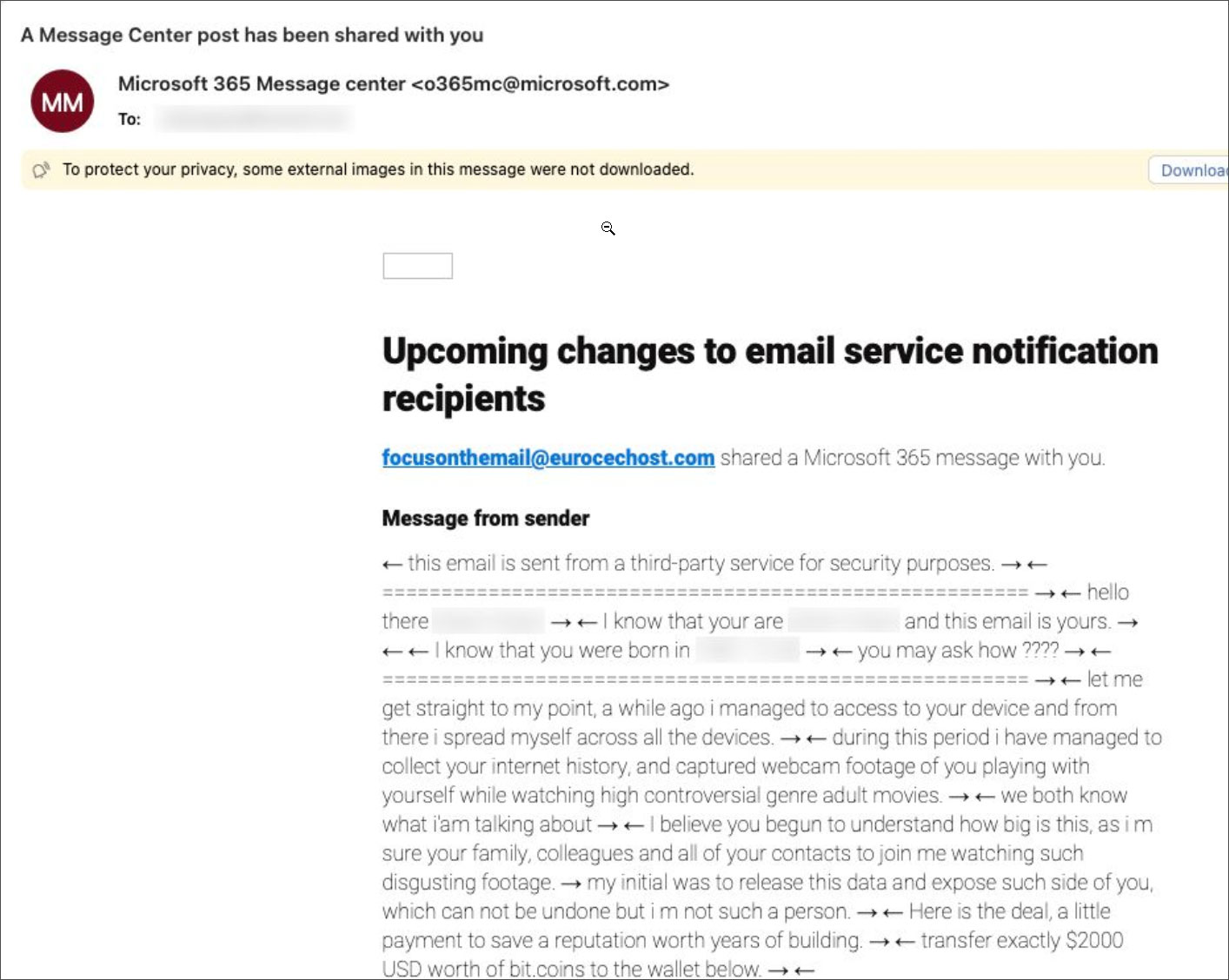
Supply: Edwin Kwan
The sextortion emails got here from “o365mc@microsoft.com,” which might really feel like a phishing tackle however is definitely Microsoft’s reputable e mail tackle used to ship messages and notifications from the Microsoft 365 Message Heart.
For these not aware of the Microsoft 365 Admin Portal, it features a part referred to as the “Message Heart,” which comprises communication from Microsoft about service advisories, new options, and upcoming modifications.
When viewing an advisory, a “Share” hyperlink lets you share the advisory with different folks, as proven under.
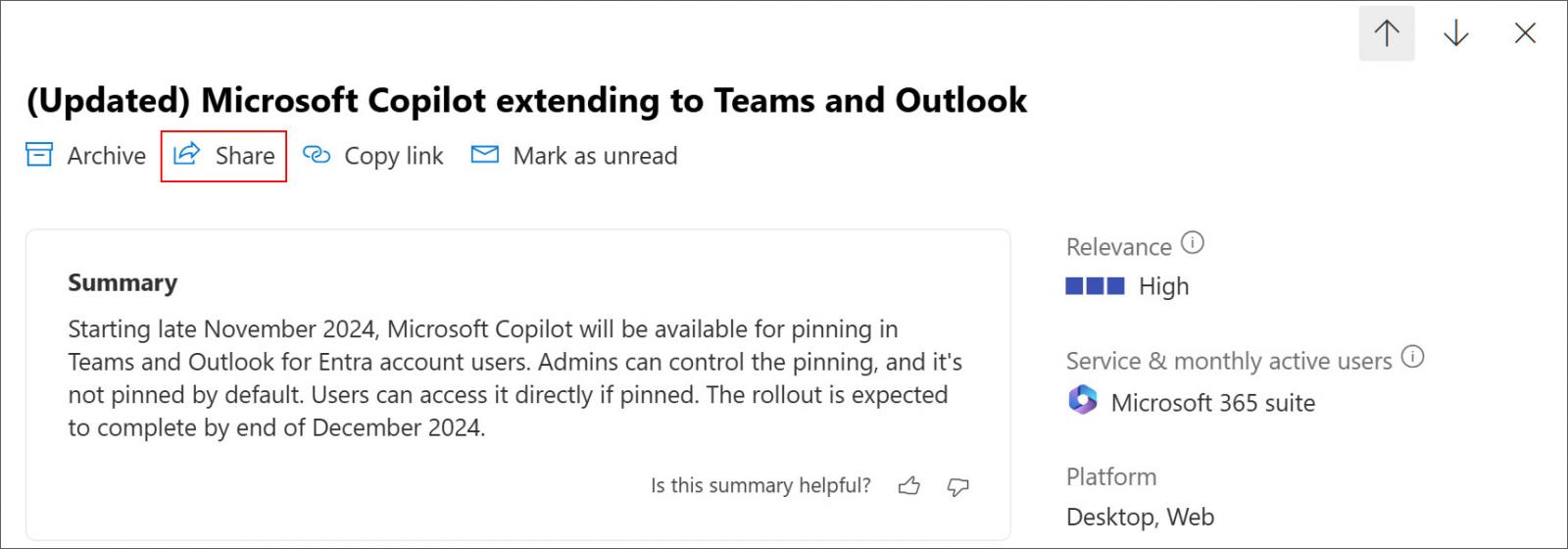
Supply: BleepingComputer
Clicking on the Share button opens a dialog asking you to enter as much as two e mail addresses to which the advisory needs to be despatched, no matter whether or not they’re exterior or inner to your group.
This display screen additionally consists of an optionally available “Private Message,” which can be added to the emailed advisory.
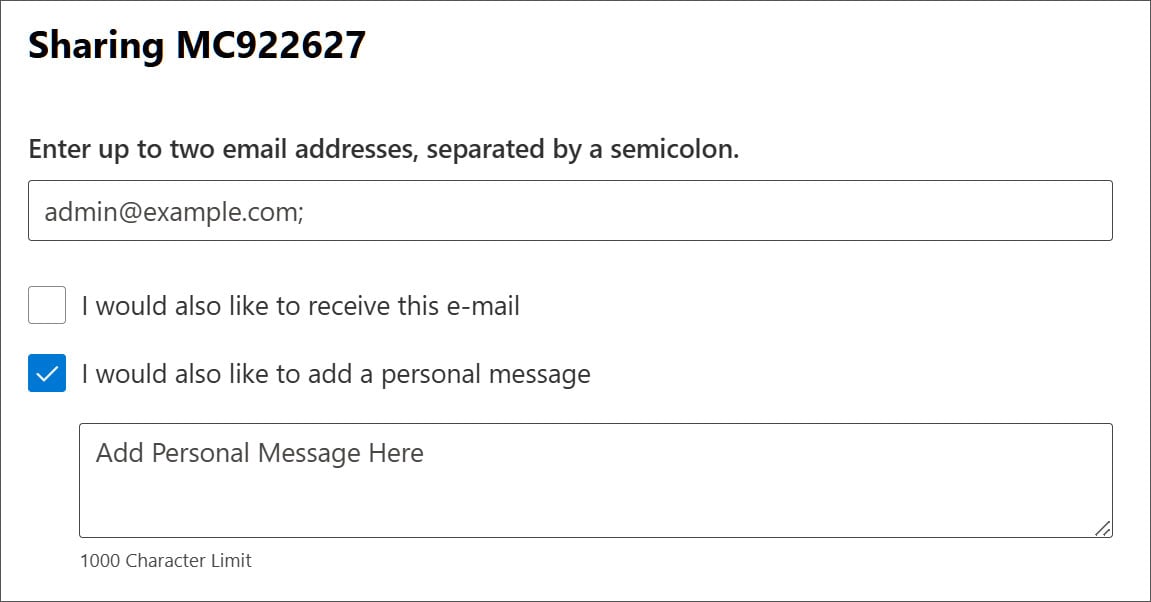
Supply: BleepingComputer
The menace actors are abusing the Private Message function through the use of it to ship the sextortion message. Nonetheless, this private message discipline is proscribed to just one,000 characters, with something extra being truncated by the consumer interface.
Because the extortion message despatched by the scammers is way over 1,000 characters, it made me surprise how they have been bypassing this restriction.
The reply is easy. They only open up the browser’s dev instruments and alter the utmost size discipline of the
This alteration now permits them to enter your entire sextortion message into the “Private Message” discipline with out it being truncated.
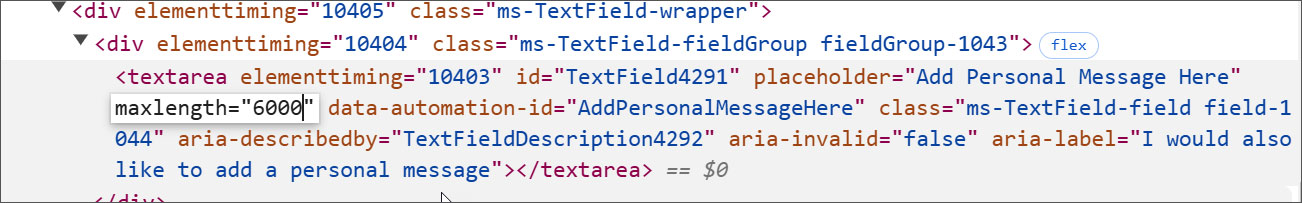
Supply: BleepingComputer
As Microsoft doesn’t carry out server-side checks for the character size, your entire extortion message is now despatched together with the advisory.
The scammers are probably utilizing an automatic course of to submit these “Share” requests, making it even simpler to ship with out a server-side verify for the size of the private message.
BleepingComputer contacted Microsoft about these scams and was instructed they’re investigating the malicious exercise.
“Thanks for bringing this to our consideration. We take safety and privateness very critically,” Microsoft instructed BleepingComputer.
“We’re investigating these experiences and can take motion to assist preserve our prospects protected.”
Right now, Microsoft has not added server-side checks to forestall messages over 1,000 characters, BleepingComputer’s exams confirmed.
Whereas this method has allowed the sextortion emails to bypass mail filters, anybody who receives them should perceive that they’re simply scams and delete them.
Fortunately, sextortion scams have change into so considerable over the previous six years that most individuals notice that they’re scams and delete these kinds of emails.
Nonetheless, for these not acquainted, these emails might be distressing and scary.
Subsequently, it is very important stress that these emails are scams, they don’t seem to be telling the reality, and you shouldn’t go to any hyperlinks in these emails or ship any cash to the listed cryptocurrency addresses.

