
The Pidgin messaging app eliminated the ScreenShareOTR plugin from its official third-party plugin listing after it was found that it was used to put in keyloggers, data stealers, and malware generally used to realize preliminary entry to company networks.
The plugin was promoted as a screen-sharing instrument for safe Off-The-Document (OTR) protocol and was out there for each Home windows and Linux variations of Pidgin.
In keeping with ESET, the malicious plugin was configured to contaminate unsuspecting customers with DarkGate malware, a strong malware risk actors use to breach networks since QBot’s dismantling by the authorities.
Sneaky Pidgin plugin
Pidgin is an open-source, cross-platform immediate messaging shopper that helps a number of networks and messaging protocols.
Though not as standard as within the mid-2000s when multi-protocol purchasers had been in excessive demand, it stays a well-liked alternative amongst these looking for to consolidate their messaging accounts right into a single app and has a devoted consumer base of tech-savvy people, open-source fanatics, and customers who want to connect with legacy IM techniques.
Pidgin operates a plugin system that permits customers to increase this system’s performance, allow area of interest options, and unlock new customization choices.
Customers can obtain them from the challenge’s official third-party plugins listing, presently internet hosting 211 addons.
In keeping with an announcement on the challenge’s web site final week, a malicious plugin named ‘ss-otr’ had slipped into the listing on July 6, 2024, and was solely pulled on August 16 following a consumer report about it being a keylogger and screenshot capturing instrument.
We quietly pulled the plugin from the listing instantly and began investigating. On August twenty second Johnny Xmas was capable of verify {that a} keylogger was current.” – Pidgin
A pink flag is that ss-otr solely offered binaries for obtain and never any supply code, however because of the lack of sturdy reviewing mechanisms in Pidgin’s third-party plugin repository, no one questioned its safety.
Plugin results in DarkGate malware
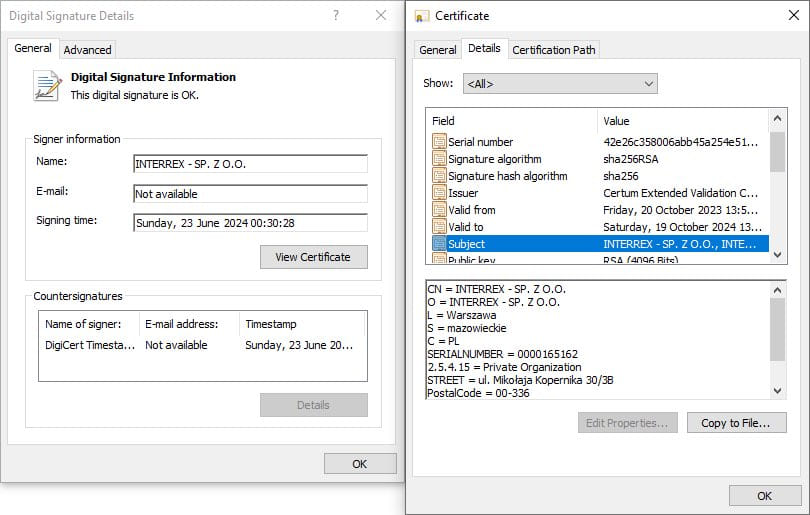
ESET reviews the plugin installer is signed with a legitimate digital certificates issued to INTERREX – SP. Z O.O., a official Polish firm.
Supply: ESET
The plugin provides the marketed performance of display sharing but additionally accommodates malicious code, permitting it to obtain extra binaries from the attacker’s server at jabberplugins[.]web.
The downloaded payloads are both PowerShell scripts or the DarkGate malware, which can be signed by an Interrex certificates.
An identical mechanism is applied for the Linux model of the Pidgin shopper, so each platforms are coated.
ESET says that the identical malicious server, which has been taken down now, hosted extra plugins named OMEMO, Pidgin Paranoia, Grasp Password, Window Merge, and HTTP File Add.
These plugins had been nearly actually additionally delivering DarkGate, indicating that ScreenShareOTR was only one small a part of a broader-scale marketing campaign.
Supply: ESET
Pidgin has not offered obtain stats for ss-otr, so the variety of victims is unknown.
Those that put in it are advisable to take away it instantly and carry out a full system scan with an antivirus instrument, as DarkGate could also be lurking on their system.
To forestall comparable incidents from taking place sooner or later, Pidgin introduced that, any more, it is going to solely settle for third-party plugins which have an OSI Permitted Open Supply License, permitting scrutiny into their code and inside performance.
