
The Corona Mirai-based malware botnet is spreading by means of a 5-year-old distant code execution (RCE) zero-day in AVTECH IP cameras, which have been discontinued for years and won’t obtain a patch.
The flaw, found by Akamai’s Aline Eliovich, is tracked as CVE-2024-7029 and is a high-severity (CVSS v4 rating: 8.7) concern within the “brightness” operate of the cameras, permitting unauthenticated attackers to inject instructions over the community utilizing specifically crafted requests.
Particularly, the easy-to-exploit flaw lies within the “brightness” argument within the “motion=” parameter of the AVTECH cameras’ firmware, supposed to permit distant changes to the brightness of a digital camera.
The flaw impacts all AVTECH AVM1203 IP cameras operating on firmware variations as much as Fullmg-1023-1007-1011-1009.
As a result of impacted fashions not being supported by the Taiwanese vendor, having reached their finish of life (EoL) in 2019, no patch is on the market to handle CVE-2024-7029, and no fixes are anticipated to be launched.
The U.S. Cybersecurity and Infrastructure Safety Company launched an advisory at first of the month to warn about CVE-2024-7029 and the provision of public exploits, warning that the cameras are nonetheless utilized in business services, monetary companies, healthcare and public well being, and transportation methods.
Proof of idea (PoC) exploits for the actual flaw have been obtainable since no less than 2019, however a CVE was solely assigned this month, and no lively exploitation had been noticed beforehand.
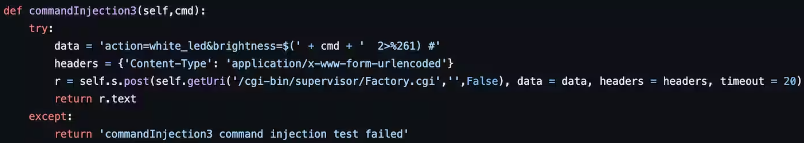
Supply: Akamai
Exploitation underway
Corona is a Mirai-based variant that has been round since no less than 2020, exploiting numerous vulnerabilities in IoT gadgets to propagate.
Akamai’s SIRT staff reviews that beginning on March 18, 2024, Corona started leveraging CVE-2024-7029 in assaults within the wild, concentrating on AVM1203 cameras nonetheless in service regardless of them having reached EoL 5 years in the past.
The primary lively marketing campaign we noticed started on March 18, 2024, however evaluation confirmed exercise for this variant as early as December 2023. The proof of idea (PoC) for CVE-2024-7029 has been publicly obtainable since no less than February 2019, however it by no means had a correct CVE task till August 2024.
The Corona assaults, as these have been captured in Akamai’s honeypots, exploit CVE-2024-7029 to obtain and execute a JavaScript file, which, in flip, hundreds the first botnet payload onto the gadget.
As soon as nested on the gadget, the malware connects to its command and management (C2) servers and awaits directions on executing distributed denial of service (DDoS) assaults.
Different flaws focused by Corona, based on Akamai’s evaluation, are:
- CVE-2017-17215: A vulnerability in Huawei routers that permits distant attackers to execute arbitrary instructions on the affected gadgets by means of the exploitation of improper validation within the UPnP service.
- CVE-2014-8361: A distant code execution (RCE) vulnerability in Realtek SDK, which is usually present in client routers. This flaw will be exploited by means of the HTTP service operating on these routers.
- Hadoop YARN RCE: Vulnerabilities throughout the Hadoop YARN (But One other Useful resource Negotiator) useful resource administration system, which will be exploited to permit distant code execution on Hadoop clusters.
Customers of AVTECH AVM1203 IP cameras are really helpful to take them offline instantly and substitute them with newer and actively supported fashions.
As IP cameras are generally uncovered to the web, making them engaging targets for menace actors, they need to all the time run the most recent firmware model to make sure identified bugs are mounted. If a tool turns into discontinued, it needs to be changed with newer fashions to proceed receiving safety updates.
Moreover, default credentials needs to be modified to sturdy and distinctive passwords and they need to be separated from crucial or manufacturing networks.
