A big-scale brute pressure password assault utilizing virtually 2.8 million IP addresses is underway, making an attempt to guess the credentials for a variety of networking gadgets, together with these from Palo Alto Networks, Ivanti, and SonicWall.
A brute pressure assault is when risk actors try and repeatedly log into an account or system utilizing many usernames and passwords till the proper mixture is discovered. As soon as they’ve entry to the proper credentials, the risk actors can then use them to hijack a tool or acquire entry to a community.
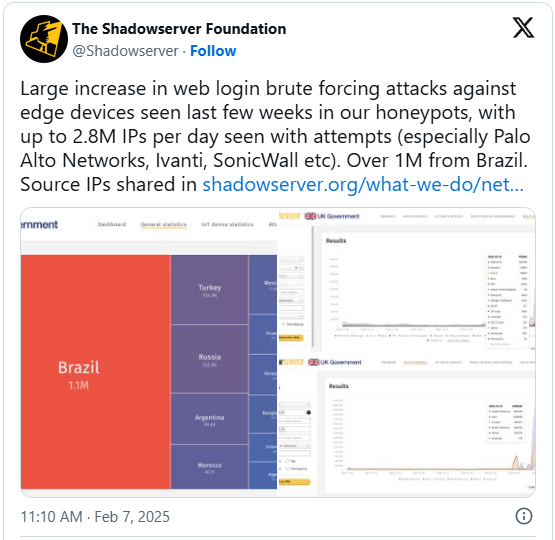
In response to the risk monitoring platform The Shadowserver Basis, a brute pressure assault has been ongoing since final month, using virtually 2.8 million supply IP addresses every day to carry out these assaults.
Most of those (1.1 million) are from Brazil, adopted by Turkey, Russia, Argentina, Morocco, and Mexico, however there’s typically a really massive variety of nations of origin collaborating within the exercise.
These are edge safety gadgets like firewalls, VPNs, gateways, and different safety home equipment, usually uncovered to the web to facilitate distant entry.
The gadgets conducting these assaults are largely MikroTik, Huawei, Cisco, Boa, and ZTE routers and IoTs, that are generally compromised by massive malware botnets.
In an announcement to BleepingComputer, The Shadowserver Basis confirmed that the exercise has been ongoing for some time however just lately elevated to a a lot bigger scale.
ShadowServer additionally stated that the attacking IP addresses are unfold throughout many networks and Autonomous Methods and are seemingly a botnet or some operation related to residential proxy networks.
Residential proxies are IP addresses assigned to shopper prospects of Web Service Suppliers (ISPs), making them extremely wanted to be used in cybercrime, scraping, geo-restriction bypasses, advert verification, sneaker/ticket scalping, and extra.
These proxies route web site visitors by means of residential networks, making it seem that the person is a daily residence person fairly than a bot, knowledge scraper, or hacker.
Gateway gadgets corresponding to these focused by this exercise could possibly be used as proxy exit nodes in residential proxying operations, routing malicious site visitors by means of a corporation’s enterprise community.
These nodes are thought of “high-quality” as organizations have an excellent status, and the assaults are tougher to detect and cease.
Steps to guard edge gadgets from brute-forcing assaults embody altering the default admin password to a robust and distinctive one, imposing multi-factor authentication (MFA), utilizing an allowlist of trusted IPs, and disabling net admin interfaces if they are not wanted.
In the end, making use of the most recent firmware and safety updates on these gadgets is essential in eliminating vulnerabilities that risk actors can leverage to achieve preliminary entry.
Final April, Cisco warned a few large-scale credential brute-forcing marketing campaign focusing on Cisco, CheckPoint, Fortinet, SonicWall, and Ubiquiti gadgets worldwide.
In December, Citrix additionally warned about password spray assaults focusing on Citrix Netscaler gadgets worlwide.