
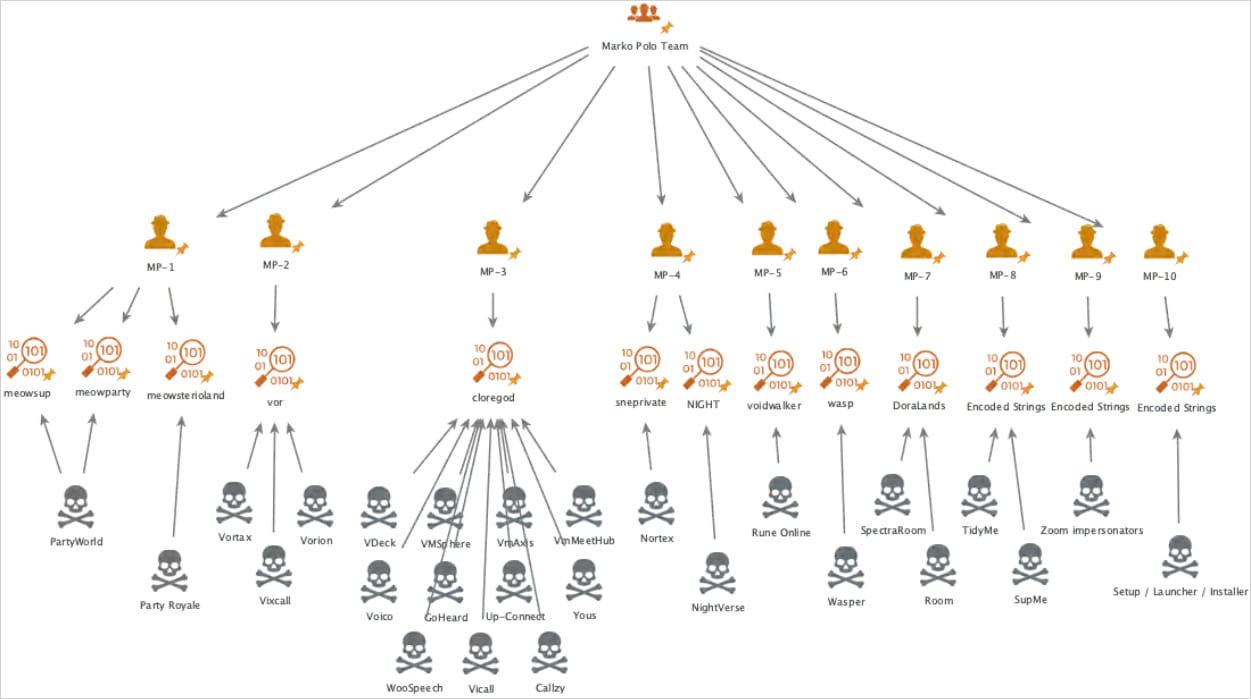
An enormous infostealer malware operation encompassing thirty campaigns concentrating on a broad spectrum of demographics and system platforms has been uncovered, attributed to a cybercriminal group named “Marko Polo.”
The risk actors use a wide range of distribution channels, together with malvertising, spearphishing, and model impersonation in on-line gaming, cryptocurrency, and software program, to unfold 50 malware payloads, together with AMOS, Stealc, and Rhadamanthys.
In keeping with Recorded Future’s Insikt Group, which has been monitoring the Marko Polo operation, the malware marketing campaign has impacted 1000’s, with potential monetary losses within the hundreds of thousands.
“Based mostly on the widespread nature of the Marko Polo marketing campaign, Insikt Group suspects that seemingly tens of 1000’s of units have been compromised globally — exposing delicate private and company information,” warns Recorded Future’s Insikt Group.
“This poses important dangers to each shopper privateness and enterprise continuity. Nearly definitely producing hundreds of thousands of {dollars} in illicit income, this operation additionally highlights the damaging financial results of such cybercriminal actions.”
Supply: Recorded Future
Setting high-value traps
Insikt Group reviews that Marko Polo primarily depends on spearphishing through direct messages on social media platforms to achieve high-value targets corresponding to cryptocurrency influencers, players, software program builders, and different individuals prone to deal with invaluable information or belongings.
Victims are lured into downloading malicious software program by interacting with what they’re tricked into believing are respectable job alternatives or venture collaborations.
A number of the manufacturers which might be impersonated embrace Fortnite (gaming), Occasion Icon (gaming), RuneScape (gaming), Rise On-line World (gaming), Zoom (productiveness), and PeerMe (cryptocurrency).
Marko Polo additionally makes use of its personal made-up manufacturers not associated to current tasks, like Vortax/Vorion and VDeck (assembly software program), Wasper and PDFUnity (collaboration platforms), SpectraRoom (crypto communications), and NightVerse (web3 recreation).
In some circumstances, the victims are led to a web site for faux digital assembly, messaging, and recreation functions, that are used to put in malware. Different campaigns distribute the malware via executables (.exe or .dmg) in torrent recordsdata.
Supply: Recorded Future
Hitting each Home windows and macOS
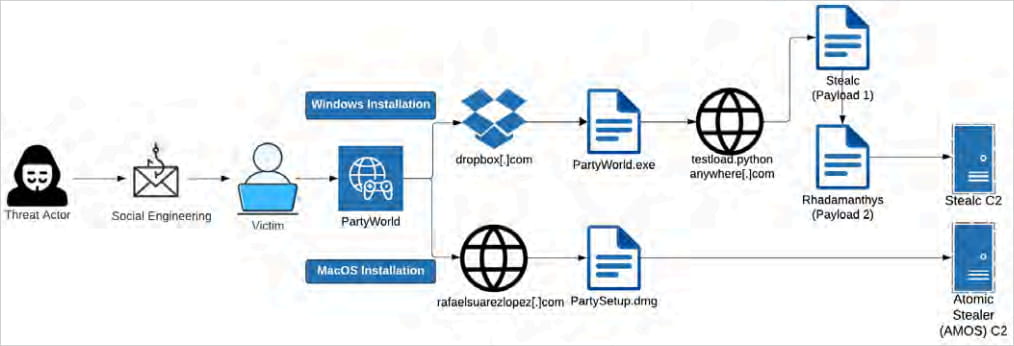
Marko Polo’s toolkit is numerous, exhibiting the risk group’s functionality to hold out multi-platform and multi-vector assaults.
On Home windows, HijackLoader is used for delivering Stealc, a general-purpose light-weight info-stealer designed to gather information from browsers and crypto pockets apps, or Rhadamanthys, a extra specialised stealer that targets a broad vary of functions and information varieties.
In a current replace, Rhadamanthys added a clipper plugin able to diverting cryptocurrency funds to the attackers’ wallets, the flexibility to get better deleted Google Account cookies, and Home windows Defender evasion.
When the goal makes use of macOS, Marko Polo deploys Atomic (‘AMOS’). This stealer launched in mid-2023, rented to cybercriminals for $1,000/month, permitting them to grab varied information saved in internet browsers.
AMOS may brute-force MetaMask seeds and steal Apple Keychain passwords to pay money for WiFi passwords, saved logins, bank card information, and different encrypted data saved on macOS.
Supply: Recorded Future
Malicious campaigns involving information-stealing malware have seen huge development through the years, with risk actors concentrating on victims via zero-day vulnerabilities, faux VPNs, fixes to GitHub points, and even solutions on StackOverflow.
These credentials are then used to breach company networks, conduct information theft campaigns like we noticed with the huge SnowFlake account breaches, and trigger chaos by corrupting community routing data.
To mitigate the danger of downloading and operating infostealer malware in your system, don’t comply with hyperlinks shared by strangers and solely obtain software program from the official venture web sites.
The malware utilized by Marko Polo is detected by most modern antivirus software program, so scanning downloaded recordsdata earlier than executing them ought to disrupt the an infection course of earlier than it begins.

