A safety researcher lately uncovered a high-risk Insecure Direct Object Reference (IDOR) vulnerability in ExHub, a cloud internet hosting and collaboration platform utilized by over 2 million builders.
The flaw enabled attackers to govern website hosting configurations for any undertaking hosted on the platform with out authorization, doubtlessly disrupting vital companies or enabling additional exploits.
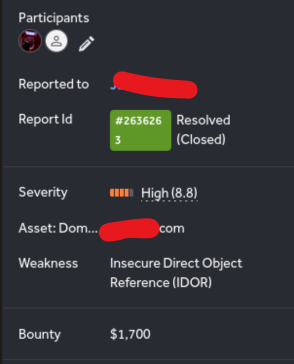
The invention earned the researcher a $1,500 bounty, with ExHub awarding an extra $200 for the report’s readability and a $100 retest price after remediation.
Vulnerability Breakdown
The IDOR vulnerability resided in ExHub’s API endpoint for undertaking deployment configurations (/api/v1/initiatives/deployment_configuration/
Attackers might exploit this by sending a crafted POST request with a goal undertaking’s ID—a trivial identifier usually seen in URLs or community logs.
By altering parameters like machine kind, ports, or authentication strategies, malicious actors might reroute visitors, disable companies, or weaken safety protocols.
Notably, even customers with minimal “reader” permissions might execute administrative actions, violating core safety rules like least privilege.
“This flaw primarily handed over the keys to any undertaking’s infrastructure,” defined the researcher, who requested anonymity. “With a single API name, an attacker might destabilize deployments or create backdoors.”
Exploitation Pathway
The researcher replicated the assault utilizing Burp Suite, a penetration testing device. After acquiring a legitimate undertaking ID—by means of guesswork, phishing, or uncovered logs—an attacker might ship a request to switch settings akin to:
{ "machineType":"t32", "port":9901, "dnsAutogen":true, "authentication":"me" }This may reconfigure the undertaking’s internet hosting setting, doubtlessly overriding firewalls or exposing inside ports. ExHub’s UI instantly mirrored these modifications, confirming the vulnerability’s severity.
ExHub initially labeled the flaw as vital (CVSS 9.8) however later downgraded it to high-risk (8.8), citing assumptions that undertaking IDs required some privilege to acquire.

Nevertheless, the researcher emphasised that such IDs are continuously uncovered in shared hyperlinks or misconfigured APIs, rendering that mitigation inadequate.
Profitable exploitation might result in:
- Service Disruptions: Malicious port modifications might sever person entry or crash purposes.
- Knowledge Publicity: Disabling authentication mechanisms may expose delicate information.
- Privilege Escalation: Attackers might abuse misconfigured companies to pivot into inside networks.
ExHub patched the vulnerability by implementing role-based entry controls (RBAC) and undertaking ID obfuscation.
A retest on October 15, 2024, confirmed the repair’s efficacy. The corporate praised the researcher’s methodology, highlighting the worth of moral hacking in bolstering platform safety.
As cloud platforms develop more and more complicated, rigorous vulnerability disclosure applications stay important.
ExHub’s immediate response and bounty allocation exemplify how collaboration between researchers and enterprises can mitigate dangers earlier than widespread exploitation happens.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Menace Intelligence Lookup - Attempt for Free
