A crucial vulnerability in Home windows File Explorer has been found, permitting attackers to seize NTLM hashes and probably exploit them for community spoofing assaults.
The vulnerability, recognized as CVE-2025-24071, includes the automated processing of specifically crafted .library-ms information inside compressed archives like RAR or ZIP.
When these information, containing paths to attacker-controlled SMB servers, are extracted, Home windows Explorer initiates an implicit NTLM authentication handshake, leaking delicate credentials with out requiring person interplay, as per a report by CTI monster.
CVE-2025-24071: Overview of the Vulnerability
CVE-2025-24071 is a major problem in Home windows File Explorer that exploits the automated processing of .library-ms information.
These XML-based information outline search and library areas and are trusted by Home windows Explorer.
When a .library-ms file containing an SMB path is extracted from a compressed archive, Home windows Explorer makes an attempt to resolve this path routinely to assemble metadata and index file data.
This course of triggers an NTLM authentication handshake with the attacker-controlled SMB server, leaking the sufferer’s NTLMv2 hash with none express person interplay.


The vulnerability is especially harmful as a result of it doesn’t require the person to open or execute the extracted file; merely extracting it from the archive is sufficient to set off the NTLM hash leak.
This makes it a strong software for attackers looking for to compromise community safety via pass-the-hash assaults or offline NTLM hash cracking.
Technical Rationalization
- Automated File Processing: Upon extraction from a compressed archive, Home windows Explorer and the SearchProtocolHost.exe service routinely course of the .library-ms file. This includes opening the file, studying its contents to extract metadata, and querying file data. These operations happen with none express person interplay and might be noticed utilizing instruments like Procmon.
- SMB Communication: The extraction course of triggers SMB communication makes an attempt. Utilizing Wireshark with an SMB filter, researchers can seize the SMB2 Negotiate Protocol Request and the SMB2 Session Setup Request, which clearly present the initiation of an NTLM authentication handshake between the sufferer’s system and the attacker-controlled SMB server.
Proof of Idea (PoC)
A Proof of Idea (PoC) for CVE-2025-24071 has been launched on GitHub.
It demonstrates how attackers can exploit this vulnerability to seize NTLM hashes by making a specifically crafted .library-ms file and embedding it inside a RAR or ZIP archive.
The PoC might be executed utilizing Python, requiring minimal enter such because the goal file identify and the attacker’s IP handle.
python poc.py
# Enter file identify: your_file_name
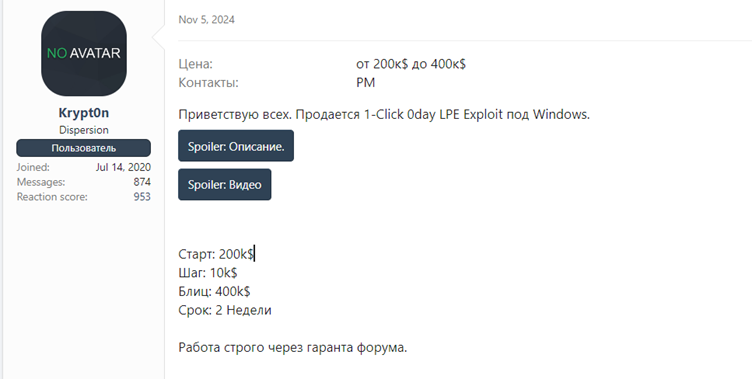
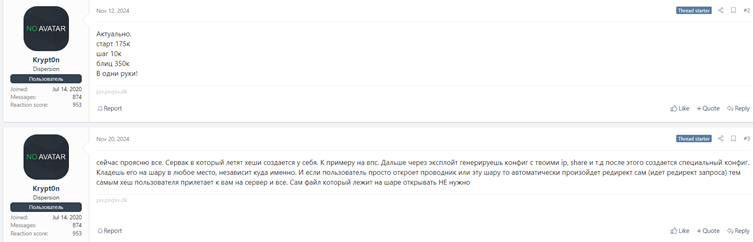
# Enter IP: attacker_IPCVE-2025-24071 is reportedly being exploited within the wild. Based on data from boards like xss.is, risk actors are using this vulnerability for credential theft.
The risk actor often called “Krypt0n” is linked to its exploitation and has developed malware often called “EncryptHub Stealer.”
The vulnerability’s potential for exploitation is underscored by its provide on the market on darkish net boards, additional emphasizing the urgency of patching affected programs.
Mitigation and Patch
Microsoft addressed CVE-2025-24071 in its March Patch Tuesday replace. Customers are suggested to make sure their Home windows programs are up to date with the most recent safety patches to forestall exploitation.
Because the vulnerability is actively being exploited, quick motion is essential to guard towards potential community spoofing assaults.
The invention and exploitation of CVE-2025-24071 spotlight the continued challenges in securing Home windows programs towards subtle threats.
By understanding how vulnerabilities like this one are exploited and taking proactive steps to patch and defend programs, customers can considerably cut back the chance of falling sufferer to such assaults.
Are you from SOC/DFIR Groups? – Analyse Malware Incidents & get dwell Entry with ANY.RUN -> Begin Now for Free.
