A safety researcher has detailed an previous hack in macOS that gave hackers full entry to a person’s iCloud, needing solely a calendar invite to succeed.
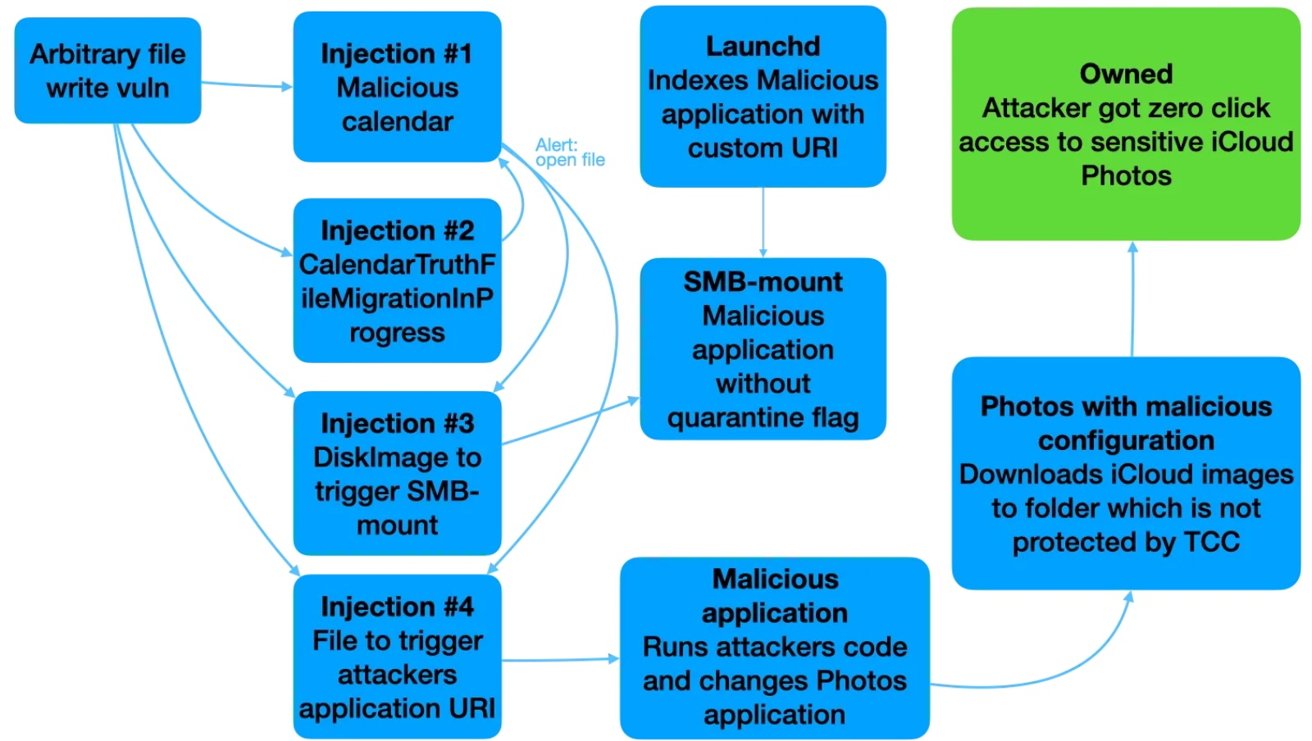
In 2022, safety researcher Mikko Kenttala found a zero-click vulnerability inside macOS Calendar that might enable attackers so as to add or delete information within the Calendar sandbox setting. The vulnerability allowed attackers to execute malicious code and entry delicate information saved on the sufferer’s gadget, together with iCloud Images.
The exploit begins with the attacker sending a calendar invite containing a malicious file attachment. The filename is not correctly sanitized, which permits the attacker to carry out a “listing traversal” assault, that means they’ll manipulate the file’s path and place it in unintended areas.
The vulnerability (CVE-2022-46723) lets attackers overwrite or delete information inside the Calendar app’s filesystem. For instance, if the attacker sends a file named “FILENAME=../../../malicious_file.txt,” will probably be positioned exterior its meant listing in a extra harmful location within the person’s filesystem.
Attackers may additional escalate the assault by utilizing the arbitrary file write vulnerability. They may inject malicious calendar information designed to execute code when macOS is upgraded, notably from Monterey to Ventura.
These information included occasions with alert functionalities that triggered when the system processed calendar information. Injected information would comprise code to routinely launch information like .dmg pictures and .url shortcuts, ultimately resulting in distant code execution (RCE).
Ultimately, the attacker may utterly take over the Mac with out the person’s data or interplay.
Fortuitously, the hack is not new. Apple patched it over a number of updates from October 2022 to September 2023. These fixes concerned tightening file permissions inside the Calendar app and including extra safety layers to stop the listing traversal exploit.
The right way to keep protected from zero-click assaults
To remain protected from zero-click vulnerabilities just like the one found in macOS Calendar, it is essential to comply with just a few protecting measures. At the beginning, at all times maintain your software program updated.
Apple continuously releases patches that handle safety flaws, and enabling computerized updates ensures you will get important fixes. Lastly, strengthen your gadget’s safety settings by proscribing apps’ entry to delicate information, resembling your calendar, images, and information.