
Risk actors began to make use of progressive internet functions to impersonate banking apps and steal credentials from Android and iOS customers.
Progressive internet apps (PWA) are cross-platform functions that may be put in instantly from the browser and supply a native-like expertise by options like push notifications, entry to gadget {hardware}, and background knowledge syncing.
Utilizing such a apps in phishing campaigns permits evading detection, bypass app set up restrictions, and acquire entry to dangerous permissions on the gadget with out having to serve the consumer a regular immediate that might increase suspicion.
The approach was first noticed within the wild in July 2023 in Poland, whereas a subsequent marketing campaign that launched in November of the identical yr focused Czech customers.
Cybersecurity firm ESET reviews that it’s presently monitoring two distinct campaigns counting on this method, one focusing on the Hungarian monetary establishment OTP Financial institution and the opposite focusing on TBC Financial institution in Georgia.
Nonetheless, the 2 campaigns seem like operated by totally different menace actors. One makes use of a definite command and management (C2) infrastructure to obtain stolen credentials, whereas the opposite group logs stolen knowledge through Telegram.
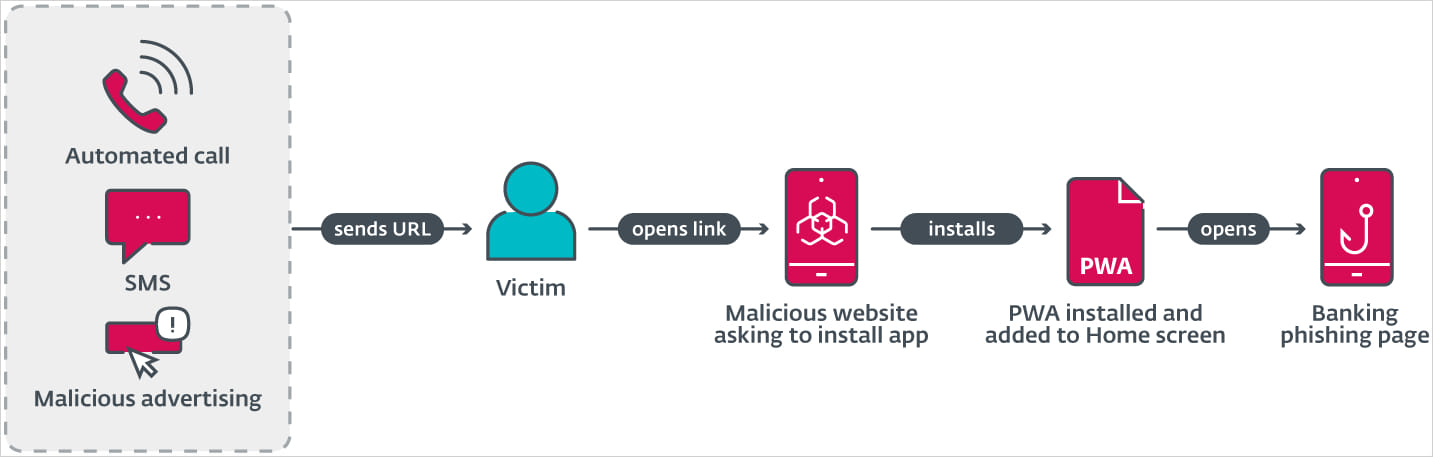
An infection chain
ESET says that the campaigns depend on a broad vary of strategies to succeed in their audience, together with automated calls, SMS messages (smishing), and well-crafted malvertising on Fb advert campaigns.
Within the first two instances, the cybercriminals trick the consumer with a pretend message about their banking app being outdated and the want to put in the most recent model for safety causes, offering a URL to obtain the phishing PWA.
Supply: ESET
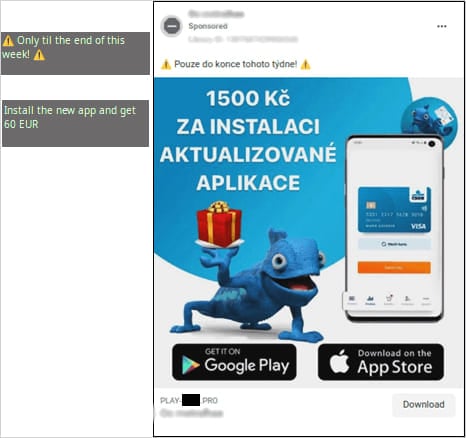
Within the case of malicious commercials on social media, the menace actors use the impersonated financial institution’s official mascot to induce a way of legitimacy and promote limited-time affords like financial rewards for putting in a supposedly essential app replace.
Supply: ESET
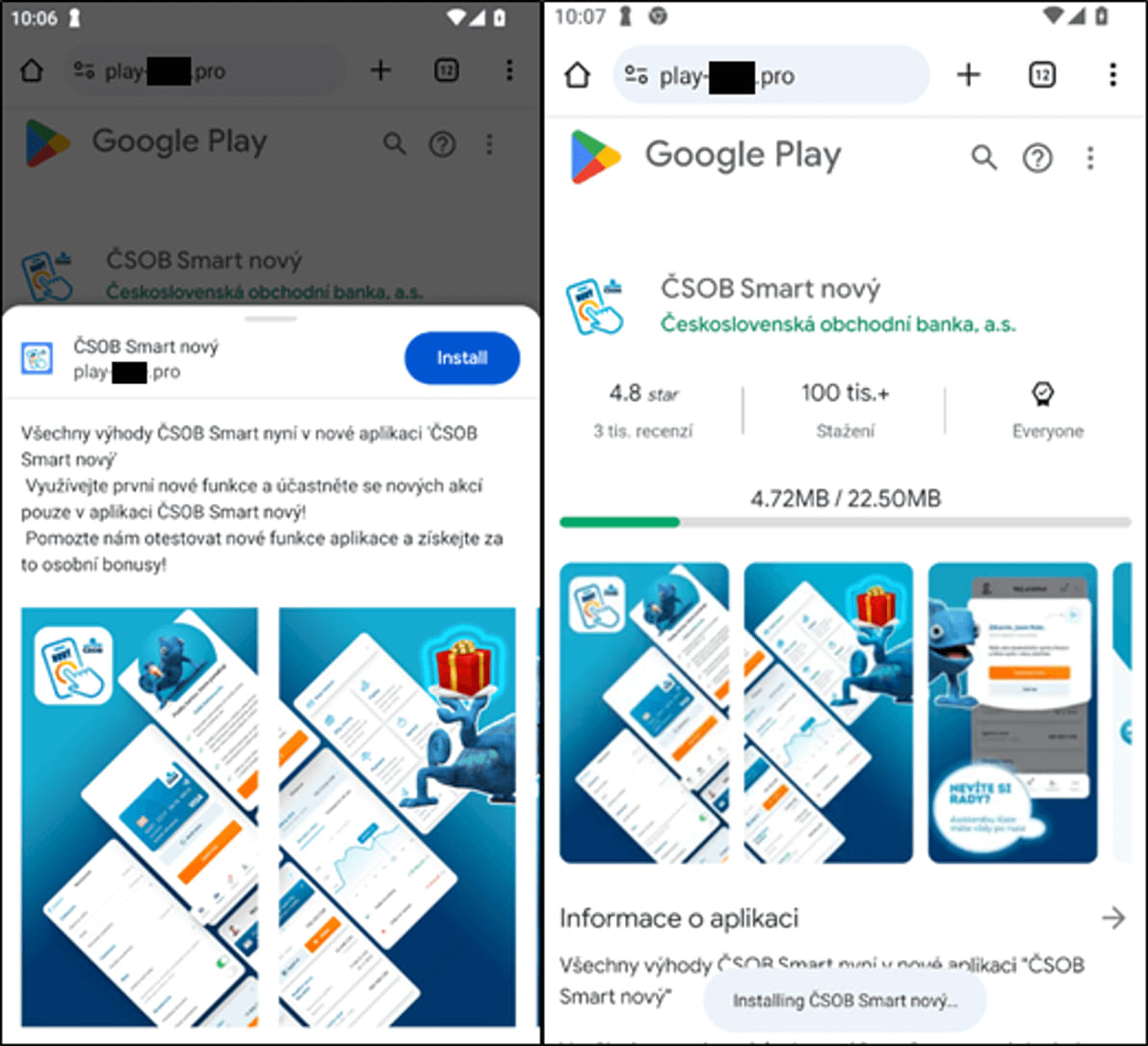
Relying on the gadget (verified through the Consumer-Agent HTTP header), clicking on the advert takes the sufferer to a bogus Google Play or App Retailer web page.
Supply: ESET
Clicking on the ‘Set up’ button prompts the consumer to put in a malicious PWA posing as a banking app. In some instances on Android, the malicious app is put in within the type of a WebAPK – a local APK generated by Chrome browser.
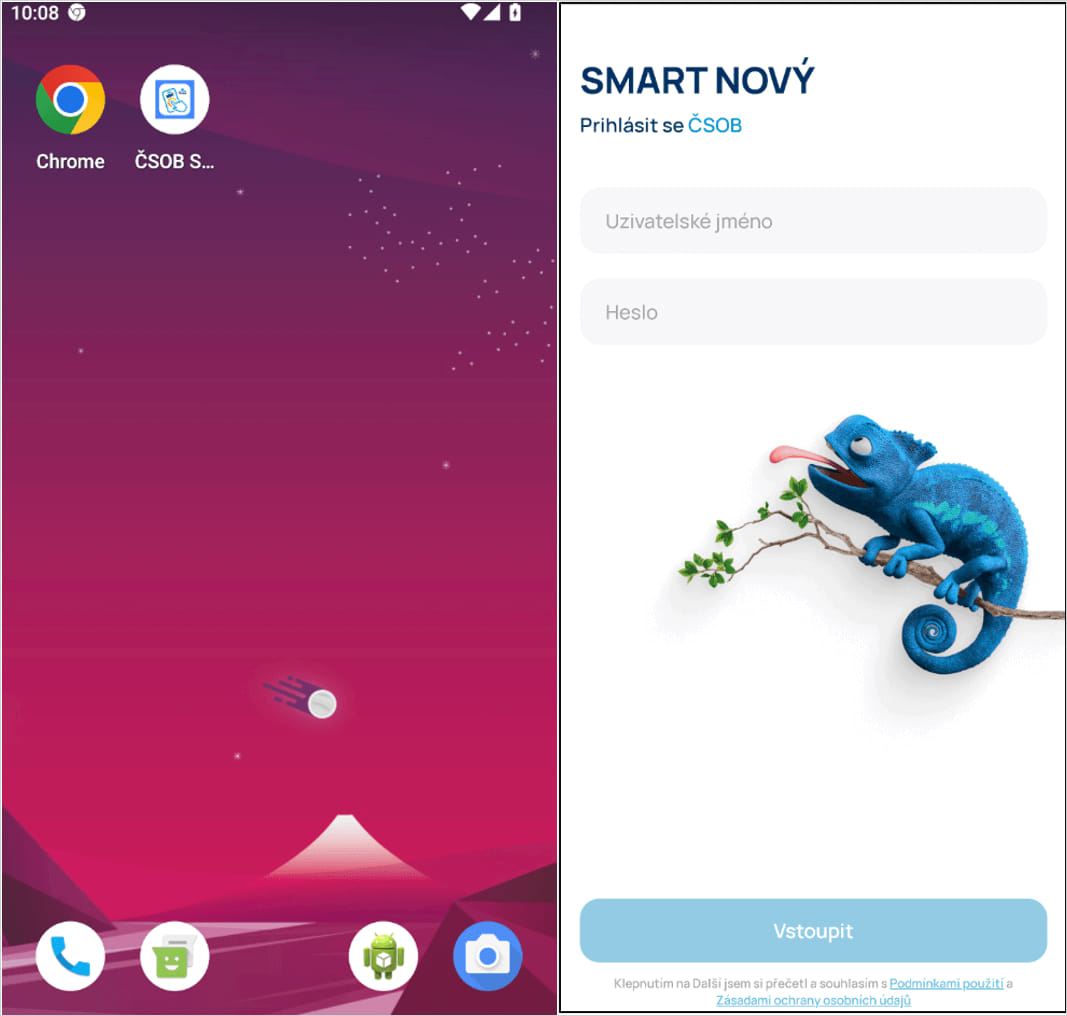
The phishing app makes use of the official banking app’s identifiers (e.g. brand legitimate-looking login display screen) and even declares Google Play Retailer because the software program supply of the app.
Supply: ESET
The attraction of utilizing PWAs on cellular
PWAs are designed to work throughout a number of platforms, so attackers can goal a broader viewers by a single phishing marketing campaign and payload.
The important thing profit, although, lies in bypassing Google’s and Apple’s set up restrictions for apps outdoors the official app shops, in addition to “set up from unknown sources” warning prompts that might alert victims to potential dangers.
PWAs can carefully mimic the feel and appear of native apps, particularly within the case of WebAPKs, the place the browser brand on the icon and the browser interface inside the app are hidden, so distinguishing it from professional functions is sort of not possible.

Supply: ESET
These internet apps can get entry to numerous gadget methods by browser APIs, similar to geolocation, digicam, and microphone, with out requesting them from the cellular OS’s permissions display screen.
In the end, PWAs could be up to date or modified by the attacker with out consumer interplay, permitting the phishing marketing campaign to be dynamically adjusted for larger success.
Abuse of PWAs for phishing is a harmful rising pattern that might acquire new proportions as extra cybercriminals understand the potential and advantages.
A number of months again, we reported about new phishing kits focusing on Home windows accounts utilizing PWAs. The kits have been created by safety researcher mr.d0x particularly to show how these apps may very well be used to steal credentials by creating convincing company login types.
BleepingComputer has contacted each Google and Apple to ask in the event that they plan to implement any defenses in opposition to PWAs/WebAPKs, and we’ll replace this submit with their responses as soon as we hear again.
