
Hackers are concentrating on Home windows machines utilizing the ZIP file concatenation method to ship malicious payloads in compressed archives with out safety options detecting them.
The method exploits the completely different strategies ZIP parsers and archive managers deal with concatenated ZIP recordsdata.
This new pattern was noticed by Notion Level, who found a a concatentated ZIP archive hiding a trojan whereas analyzing a phishing assault that lured customers with a pretend transport discover.
The researchers discovered that the attachment was disguised as a RAR archive and the malware leveraged the AutoIt scripting language to automate malicious duties.
Supply: Notion Level
Hiding malware in “damaged” ZIPs
The primary stage of the assault is the preparation, the place the risk actors create two or extra separate ZIP archives and conceal the malicious payload in one in all them, leaving the remainder with innocuous content material.
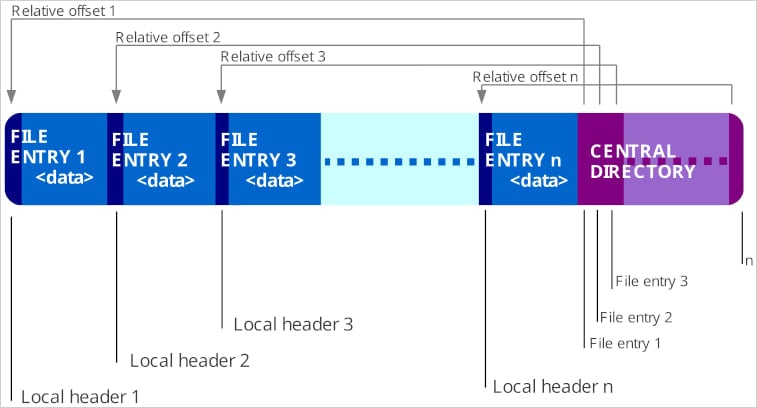
Subsequent, the separate recordsdata are concatenated into one by appending the binary information of 1 file to the opposite, merging their contents into one mixed ZIP archive.
Though the ultimate consequence seems as one file, it accommodates a number of ZIP constructions, every with its personal central listing and finish markers.
Supply: Notion Level
Exploiting ZIP app flaws
The following part of the assault depends on how ZIP parsers deal with concatenated archives. Notion Level examined 7zip, WinRAR, and Home windows File Explorer to completely different outcomes:
- 7zip solely reads the primary ZIP archive (which could possibly be benign) and should generate a warning about extra information, which customers could miss
- WinRAR reads and shows each ZIP constructions, revealing all recordsdata, together with the hidden malicious payload.
- Home windows File Explorer could fail to open the concatenated file or, if renamed with a .RAR extension, would possibly show solely the second ZIP archive.
Relying on the app’s conduct, the risk actors could fine-tune their assault, equivalent to hiding the malware within the first or the second ZIP archive of the concatenation.
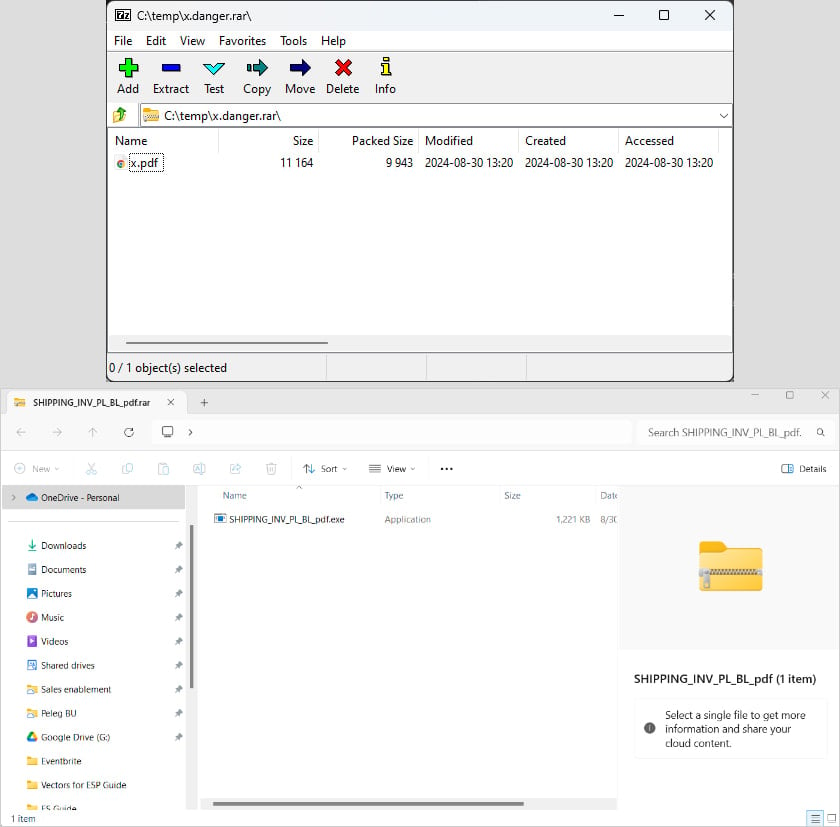
Attempting the malicious archive from the assault on 7Zip, Notion Level researchers noticed that solely a innocent PDF file was proven. Opening it with Home windows Explorer, although, revealed the malicious executable.
Supply: Notion Level
To defend in opposition to concatenated ZIP recordsdata, Notion Level means that customers and organizations use safety options that assist recursive unpacking.
Usually, emails attaching ZIPs or different archive file varieties must be handled with suspicion, and filters must be carried out in important environments to dam the associated file extensions.
