Hackers are believed to be exploiting not too long ago fastened SimpleHelp Distant Monitoring and Administration (RMM) software program vulnerabilities to achieve preliminary entry to focus on networks.
The failings, tracked as CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728, permit menace actors to obtain and add information on units and escalate privileges to administrative ranges.
The vulnerabilities have been found and disclosed by Horizon3 researchers two weeks in the past. SimpleHelp launched fixes between January 8 and 13 in product variations 5.5.8, 5.4.10, and 5.3.9.
Arctic Wolf now reviews about an ongoing marketing campaign focusing on SimpleHelp servers that began roughly per week after Horizon3’s public disclosure of the issues.
The safety firm is not 100% sure that the assaults leverage these flaws however connects its observations to Horizon3’s report with medium confidence.
“Whereas it isn’t confirmed that the not too long ago disclosed vulnerabilities are liable for the noticed marketing campaign, Arctic Wolf strongly recommends upgrading to the newest out there fastened variations of the SimpleHelp server software program the place doable,” reads the report.
“In conditions the place the SimpleHelp shopper was beforehand put in on units for third-party assist classes however is not actively getting used for day-to-day operations, Arctic Wolf recommends uninstalling the software program to cut back the potential assault floor.”
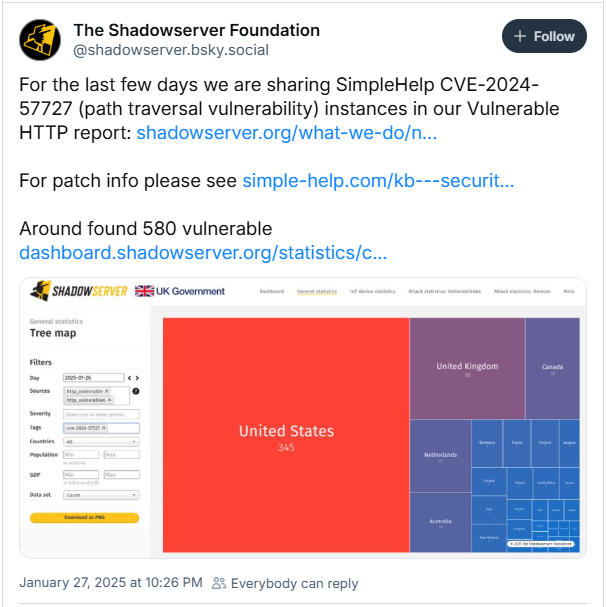
Risk monitoring platform Shadowserver Basis reported they see 580 susceptible situations uncovered on-line, most (345) situated in the USA.
Assaults within the wild
Artic Wolf reviews that the SimpleHelp ‘Distant Entry.exe’ course of was already working within the background earlier than the assault, indicating that SimpleHelp was beforehand put in for distant assist classes on the units.
The primary signal of compromise was the SimpleHelp shopper on the goal machine speaking with an unapproved SimpleHelp server.
That is doable by both the attacker exploiting flaws in SimpleHelp to achieve management of the shopper or utilizing stolen credentials to hijack the connection.
As soon as inside, the attackers ran cmd.exe instructions like ‘web’ and ‘nltest’ to collect intelligence concerning the system, together with a listing of consumer accounts, teams, shared assets, and area controllers, and take a look at Lively Listing’s connectivity.
These are widespread steps earlier than performing privilege escalation and lateral motion. Nonetheless, Arctic Wolf says the malicious session was reduce off earlier than it may very well be decided what the menace actor would do subsequent.
SimpleHelp customers are really helpful to improve to the newest model that addresses the CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 flaws.
Extra details about learn how to apply the safety updates and confirm the patch is obtainable in SimpleHelp’s bulletin.
If SimpleHelp shoppers have been put in previously to accommodate distant assist classes however are now not wanted, it could be finest that they be uninstalled from the programs to get rid of the assault floor.