
Palo Alto Networks is warning that hackers are exploiting the CVE-2024-3393 denial of service vulnerability to disable firewall protections by forcing it to reboot.
Leveraging the safety challenge repeatedly, nonetheless, causes the machine to enter upkeep mode and handbook intervention is required to revive it to regular operations.
“A Denial of Service vulnerability within the DNS Safety characteristic of Palo Alto Networks PAN-OS software program permits an unauthenticated attacker to ship a malicious packet by means of the info aircraft of the firewall that reboots the firewall,” reads the advisory.
DoS bug is actively exploited
Palo Alto Networks says that exploiting the vulnerability is feasible by an unauthenticated attacker that sends a specifically crafted, malicious packet to an affected machine.
The problem solely impacts units the place ‘DNS Safety’ logging is enabled, whereas the product variations affected by CVE-2024-3393 are proven under.
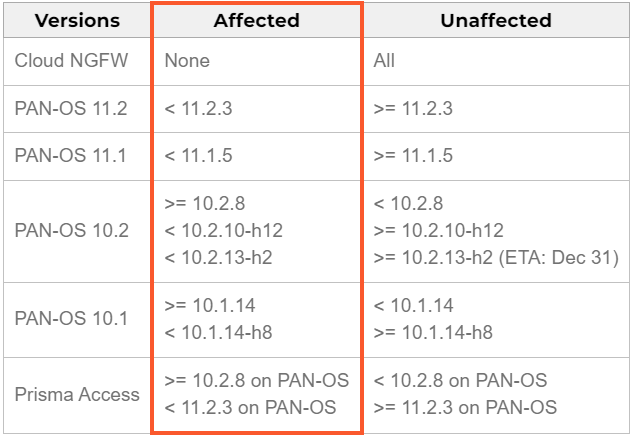
The seller confirmed that the flaw is actively exploited, noting that prospects skilled outages when their firewall blocked malicious DNS packets from attackers leveraging the difficulty.
The corporate has addressed the flaw in PAN-OS 10.1.14-h8, PAN-OS 10.2.10-h12, PAN-OS 11.1.5, PAN-OS 11.2.3, and subsequent releases.
Nonetheless, it is famous that PAN-OS 11.0, which is impacted by CVE-2024-3393, is not going to obtain a patch as a result of that model has reached its end-of-life (EOL) date on November 17.
Palo Alto Networks has additionally revealed workarounds and steps to mitigate the issue for many who can’t instantly replace:
For unmanaged NGFWs, NGFWs managed by Panorama, or Prisma Entry Managed by Panorama:
- Navigate to: Objects → Safety Profiles → Anti-spyware → DNS Insurance policies → DNS Safety for every Anti-spyware profile.
- Change the Log Severity to “none” for all configured DNS Safety classes.
- Commit the adjustments and revert the Log Severity settings after making use of the fixes.
For NGFWs managed by Strata Cloud Supervisor (SCM):
- Choice 1: Disable DNS Safety logging straight on every NGFW utilizing the steps above.
- Choice 2: Disable DNS Safety logging throughout all NGFWs within the tenant by opening a help case.
For Prisma Entry managed by Strata Cloud Supervisor (SCM):
- Open a help case to disable DNS Safety logging throughout all NGFWs in your tenant.
- If wanted, request to expedite the Prisma Entry tenant improve within the help case.
