Hackers are exploiting a vulnerability in Microsoft’s Azure App Proxy by manipulating the pre-authentication settings to realize unauthorized entry to personal networks.
The Azure App Proxy is designed to securely publish on-premises functions to the general public web with out requiring firewall port openings, leveraging Microsoft Entra ID for authentication,.
How Azure App Proxy Works
For organizations to make use of Azure App Proxy, a personal community connector should be put in on a system inside their personal community.
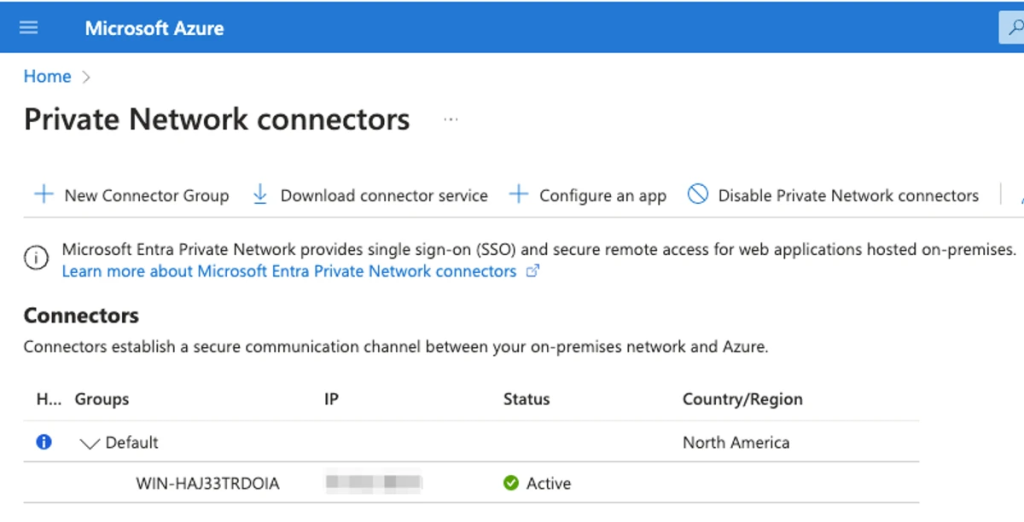

This connector establishes an outbound connection to Azure, permitting functions to be revealed by the proxy.
Based on the TrustedSec report, the pre-authentication setting is essential right here, because it determines how customers are authenticated earlier than accessing revealed functions.
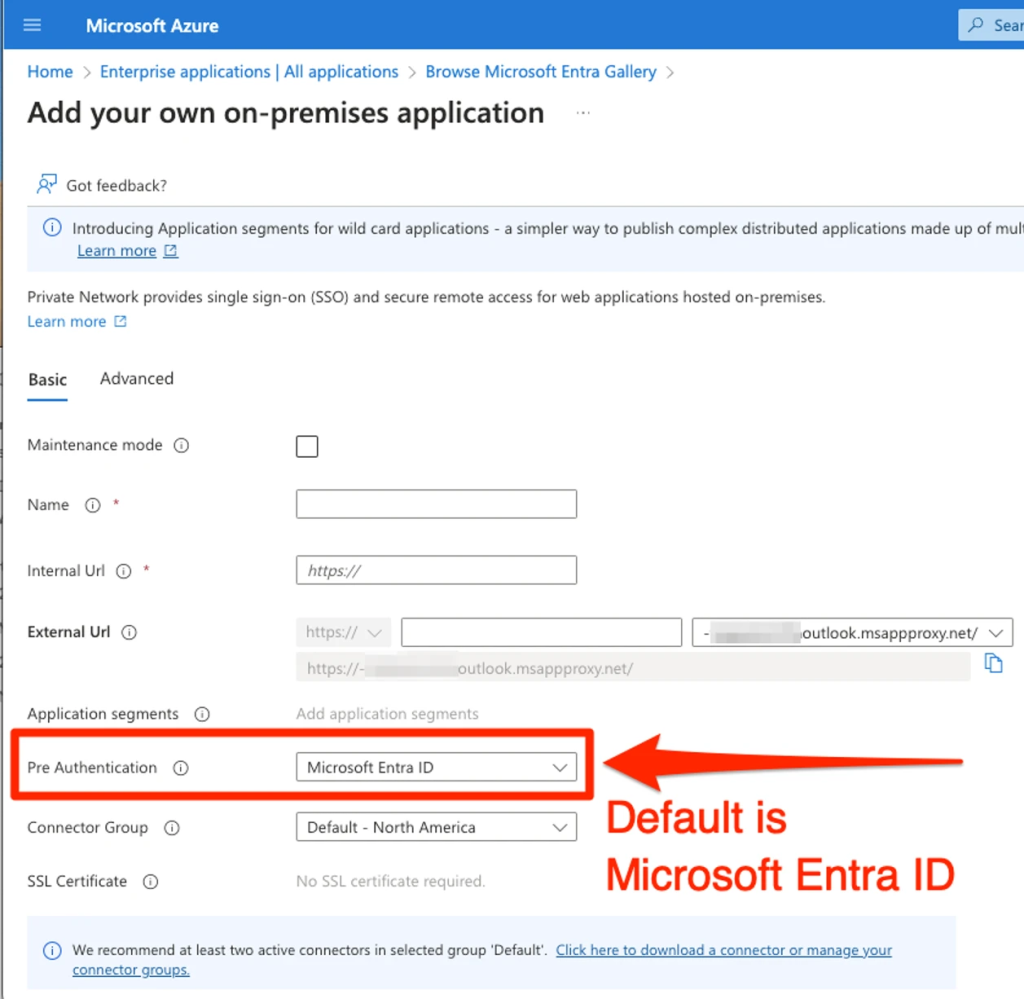

Pre-Authentication Settings
Azure App Proxy gives two pre-authentication choices: Microsoft Entra ID and Passthrough.


Microsoft Entra ID is the default, offering sturdy authentication by redirecting customers to Microsoft’s authentication providers earlier than accessing the appliance.
This ensures that each one paths inside the utility are protected by Entra ID authentication.
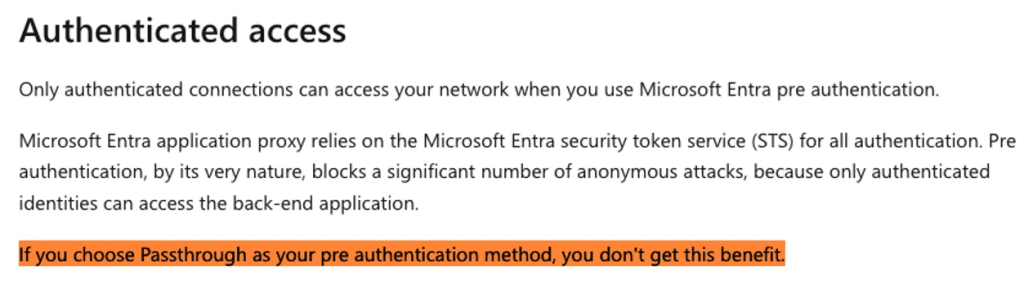
Alternatively, Passthrough doesn’t require authentication earlier than forwarding requests to the appliance.
Whereas this feature might sound helpful for publicly accessible functions, it leaves them susceptible to unauthorized entry.
Microsoft’s documentation warns that Passthrough doesn’t shield towards nameless assaults, just like exposing a server port on to the web.
Dangers and Exploits
In an illustration setup utilizing a Home windows Server 2022 VM internet hosting a fundamental HTTP web site, two functions have been configured with totally different pre-authentication settings:
- MSENTRAID-redactedoutlook.msappproxy.internet used Microsoft Entra ID for authentication, requiring customers to authenticate earlier than accessing the appliance.
- PASSTHROUGH-redactedoutlook.msappproxy.internet, as anticipated, didn’t require authentication, permitting direct entry to the appliance and its assets.
When utilizing the Passthrough possibility, not solely is the supposed public utility accessible, however so are different assets on the server. This could result in unintentional publicity of delicate personal community assets.

For example, if a gross sales quoting utility on the root of the positioning makes use of Entra ID for authentication, whereas a buyer portal at a unique path is meant to be publicly accessible, utilizing Passthrough may inadvertently make all the server accessible.
Compelled Shopping and Brute-Pressure Assaults
Hackers can simply exploit this vulnerability by participating in compelled searching for content material discovery.
Every request to the Passthrough URL reveals responses immediately from the VM, together with doubtlessly delicate functions or directories that weren’t supposed to be public.
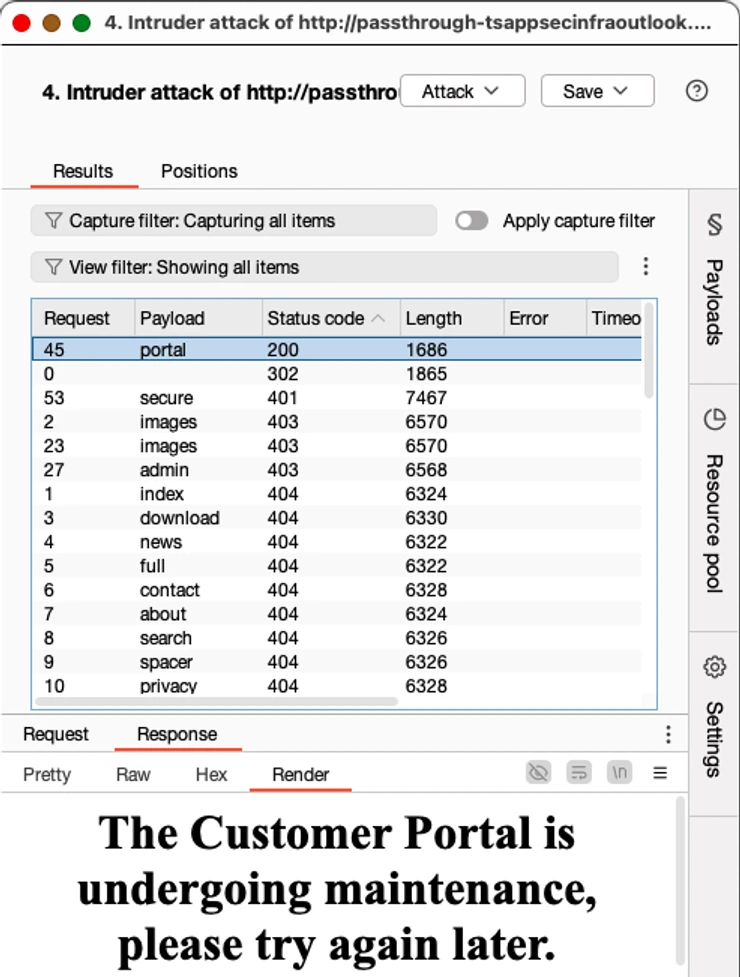

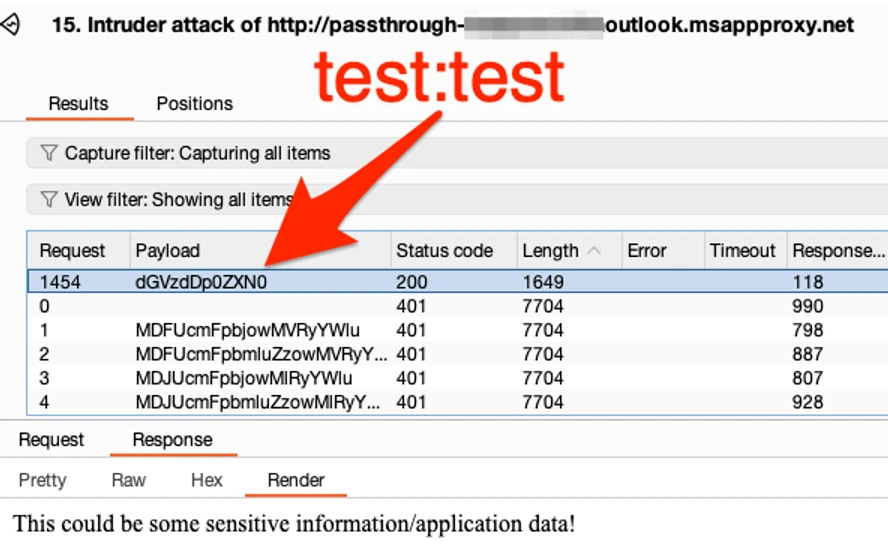
Within the situation the place a path prompts for HTTP Fundamental authentication, attackers can use instruments like Burp Suite’s Intruder to brute-force widespread default credentials comparable to admin:admin.
If weak credentials are used, unauthorized entry to information or functions can happen, offering an entry level for malicious actions.

Whereas the Azure App Proxy is a robust device for securing distant entry to functions, misconfiguring pre-authentication settings can have extreme penalties.
Organizations should rigorously consider their use of Passthrough, guaranteeing that they perceive the dangers concerned and take extra measures to safe functions and assets that aren’t supposed for public entry.
Common safety audits and powerful authentication practices are essential to mitigating these vulnerabilities and defending delicate personal community assets.
By adopting these practices, organizations can successfully use Azure App Proxy whereas safeguarding their personal community assets towards unauthorized entry.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Risk Intelligence Lookup - Strive for Free
