
Hackers have used new GodLoader malware exploiting the capabilities of the broadly used Godot recreation engine to evade detection and infect over 17,000 techniques in simply three months.
As Test Level Analysis discovered whereas investigating the assaults, risk actors can use this malware loader to focus on players throughout all main platforms, together with Home windows, macOS, Linux, Android, and iOS.
It is also used to leverage Godot’s flexibility and its GDScript scripting language capabilities to execute arbitrary code and bypass detection techniques utilizing the sport engine .pck recordsdata, which package deal recreation property, to embed dangerous scripts.
As soon as loaded, the maliciously crafted recordsdata set off malicious code on the victims’ gadgets, enabling attackers to steal credentials or obtain extra payloads, together with the XMRig crypto miner. This miner malware’s configuration was hosted on a personal Pastebin file uploaded in Could, which was visited 206,913 occasions all through the marketing campaign.
“Since at the very least June 29, 2024, cybercriminals have been benefiting from Godot Engine to execute crafted GDScript code which triggers malicious instructions and delivers malware. This system has remained undetected by most antivirus instruments on VirusTotal, presumably infecting greater than 17,000 machines in just some months,” in keeping with Test Level.
“Godot has a vibrant and rising group of builders who worth its open-source nature and highly effective capabilities. Over 2,700 builders contributed to the Godot gaming engine,” whereas “on platforms like Discord, YouTube, and different social media platforms, the Godot engine has round 80,000 followers who keep up to date on the newest information.”
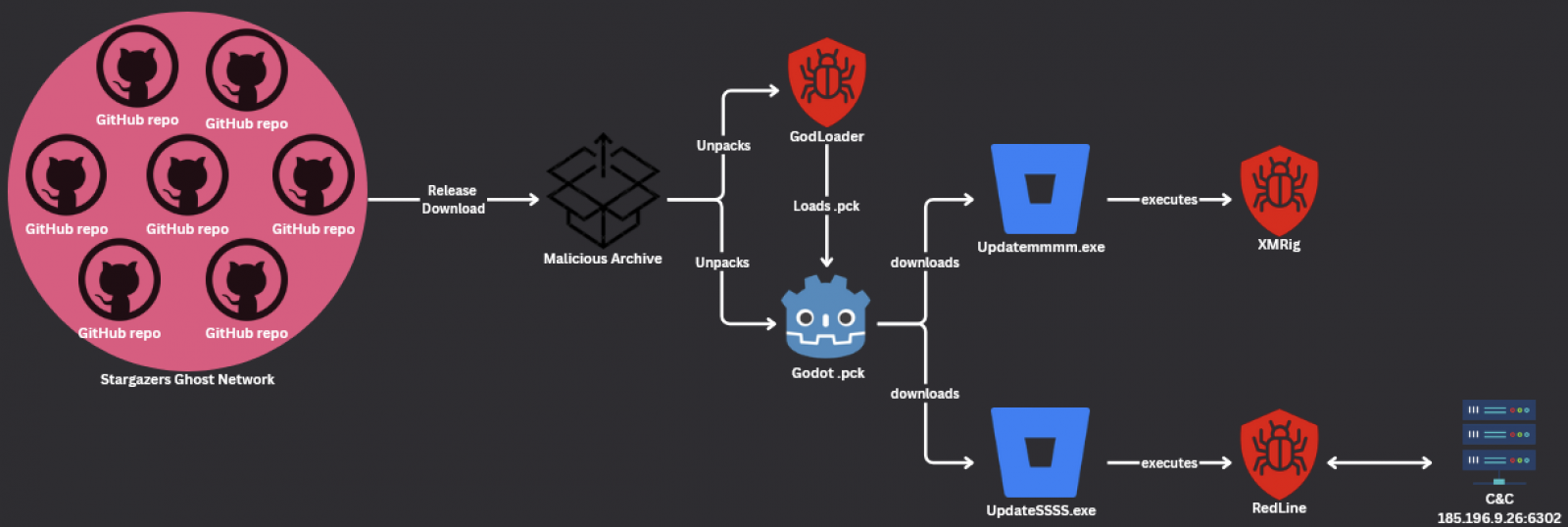
The attackers delivered the GodLoader malware by way of the Stargazers Ghost Community, a malware Distribution-as-a-Service (DaaS) that masks its actions utilizing seemingly authentic GitHub repositories.
Between September and October 2024, they used over 200 repositories managed by over 225 Stargazer Ghost accounts to deploy the malware to targets’ techniques, exploiting potential victims’ belief in open-source platforms and seemingly authentic software program repositories.
All through the marketing campaign, Test Level detected 4 separate assault waves towards builders and players between September 12 and October 3, attractive them to obtain contaminated instruments and video games.
Whereas the safety researchers solely found GodLoader samples concentrating on Home windows techniques, additionally they developed GDScript proof-of-concept exploit code exhibiting how simply the malware may be tailored to assault Linux and macOS techniques.
Stargazer Goblin, the risk actor behind the Stargazers Ghost Community DaaS platform utilized in these assaults, was first noticed by Test Level selling this malware distribution service on the darkish internet in June 2023. Nonetheless, it has seemingly been energetic since at the very least August 2022, incomes over $100,000 since this service was launched.
The Stargazers Ghost Community makes use of over 3,000 GitHub “ghost” accounts to create networks of tons of of repositories that can be utilized to ship malware (primarily info stealers like RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer) and star, fork, and subscribe to those malicious repos to push them to GitHub’s trending part and enhance their obvious legitimacy.
