
A brand new malicious marketing campaign is utilizing a official however outdated and susceptible Avast Anti-Rootkit driver to evade detection and take management of the goal system by disabling safety elements.
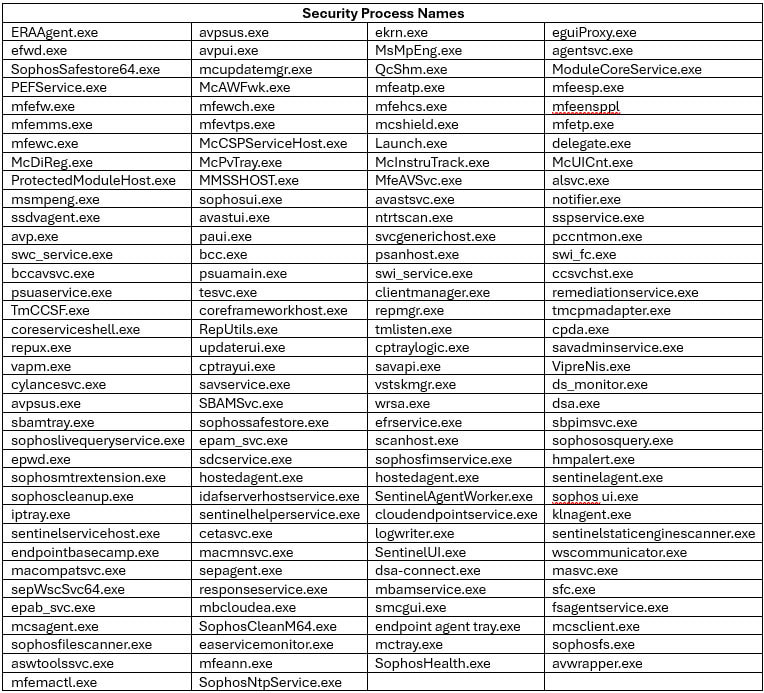
The malware that drops the motive force is a variant of an AV Killer of no explicit household. It comes with a hardcoded listing of 142 names for safety processes from varied distributors.
For the reason that driver can function at kernel degree, it offers entry to vital components of the working system and permits the malware to terminate processes.
Safety researchers at cybersecurity firm Trellix not too long ago found a brand new assault that leverages the bring-your-own-vulnerable-driver (BYOVD) strategy with an outdated model of the anti-rootkit driver to cease safety merchandise on a focused system.
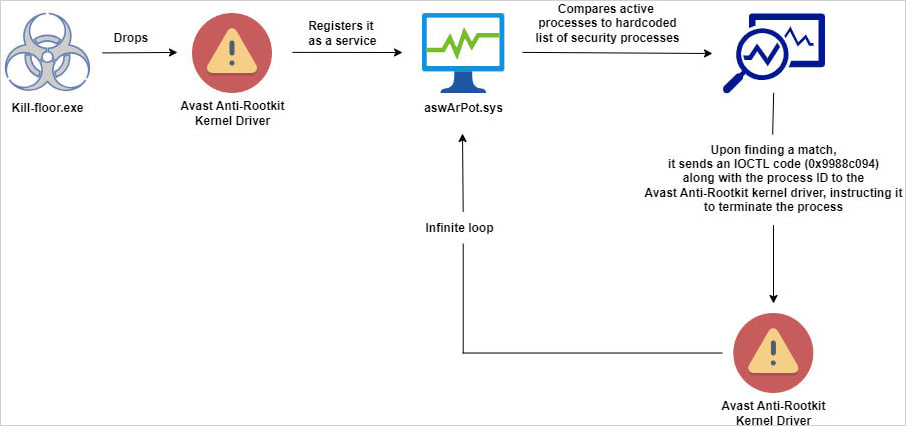
They clarify {that a} piece a bit of malware with the file title kill-floor.exe drops the susceptible driver with the file title ntfs.bin within the default Home windows consumer folder. Subsequent, the malware creates the service ‘aswArPot.sys’ utilizing the Service Management (sc.exe) and registers the motive force.
Supply: Trellix
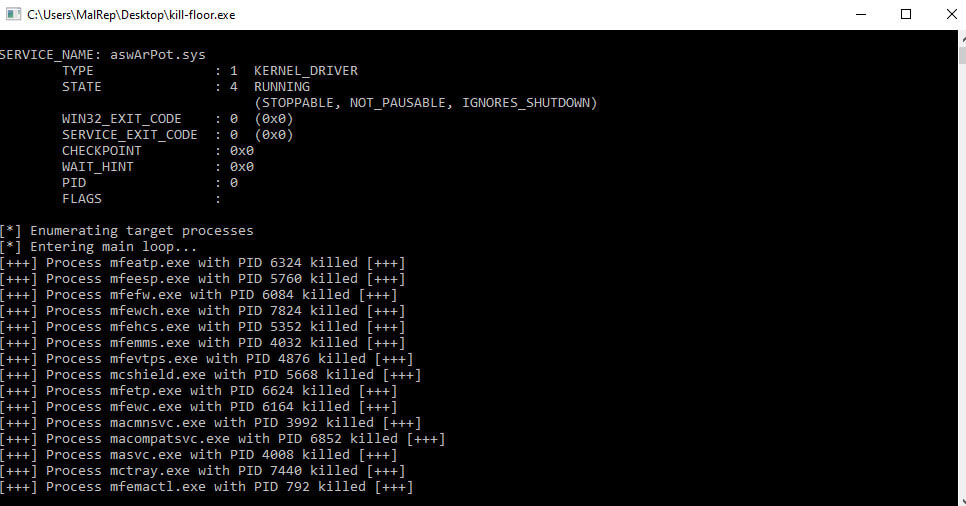
The malware then makes use of a hardcoded listing of 142 processes related to safety instruments and checks it in opposition to a number of snapshots of energetic processes on the system.
Trellix researcher Trishaan Kalra says that when it finds a match, “the malware creates a deal with to reference the put in Avast driver.”
It then leverages the ‘DeviceIoControl’ API to situation the required IOCTL instructions to terminate it.
Supply: Trellix
As seen within the screenshot above, the malware targets processes from varied safety options, together with these from McAfee, Symantec (Broadcom), Sophos, Avast, Pattern Micro, Microsoft Defender, SentinelOne, ESET, and BlackBerry.
With defenses deactivated, the malware can carry out malicious actions with out triggering alerts to the consumer or getting blocked.
Supply: Trellix
It’s value noting that the motive force and related procedures had been noticed in early 2022 by researchers at Pattern Micro whereas investigating an AvosLocker ransomware assault.
In December 2021, the Stroz Friedberg’s Incident Response Providers workforce discovered that Cuba ransomware utilized in assaults a script that abused a operate in Avast’s Anti-Rootkit kernel driver to kill safety options on sufferer’s techniques.
Across the similar time, researchers at SentinelLabs found found two high-severity flaws (CVE-2022-26522 and CVE-2022-26523) that had been current since 2016, which might be exploited “to escalate privileges enabling them to disable safety merchandise.”
The 2 points had been reported to Avast in December 2021 and the corporate addressed them silently with safety updates.
Defending in opposition to assaults that depend on susceptible drivers is feasible by utilizing guidelines that may establish and block elements primarily based on their signatures or hashes, equivalent to this one that Trellix recommends.
Microsoft additionally has options, such because the susceptible driver blocklist coverage file, which is up to date with each main Home windows launch. Beginning Home windows 11 2022, the listing is energetic by default on all units. The most recent model of the listing is feasible by way of App Management for Enterprise.
