For greater than 15 years, Google Protected Looking has been defending customers from phishing, malware, undesirable software program and extra, by figuring out and warning customers about probably abusive websites on greater than 5 billion units around the globe. As attackers develop extra subtle, we have seen the necessity for protections that may adapt as rapidly because the threats they defend towards. That’s why we’re excited to announce a brand new model of Protected Looking that may present real-time, privacy-preserving URL safety for individuals utilizing the Commonplace safety mode of Protected Looking in Chrome.
Present panorama
Chrome mechanically protects you by flagging probably harmful websites and information, hand in hand with Protected Looking which discovers hundreds of unsafe websites each day and provides them to its lists of dangerous websites and information.
To this point, for privateness and efficiency causes, Chrome has first checked websites you go to towards a locally-stored listing of recognized unsafe websites which is up to date each 30 to 60 minutes – that is accomplished utilizing hash-based checks.
Hash-based test overview
However unsafe websites have tailored — right now, the vast majority of them exist for lower than 10 minutes, that means that by the point the locally-stored listing of recognized unsafe websites is up to date, many have slipped by means of and had the possibility to do harm if customers occurred to go to them throughout this window of alternative. Additional, Protected Looking’s listing of dangerous web sites continues to develop at a speedy tempo. Not all units have the assets essential to keep up this rising listing, nor are they at all times in a position to obtain and apply updates to the listing on the frequency essential to profit from full safety.
Protected Looking’s Enhanced safety mode already stays forward of such threats with applied sciences equivalent to real-time listing checks and AI-based classification of malicious URLs and net pages. We constructed this mode as an opt-in to provide customers the selection of sharing extra security-related knowledge to be able to get stronger safety. This mode has proven that checking lists in actual time brings vital worth, so we determined to deliver that to the default Commonplace safety mode by means of a brand new API – one that does not share the URLs of websites you go to with Google.
Introducing real-time, privacy-preserving Protected Looking
The way it works
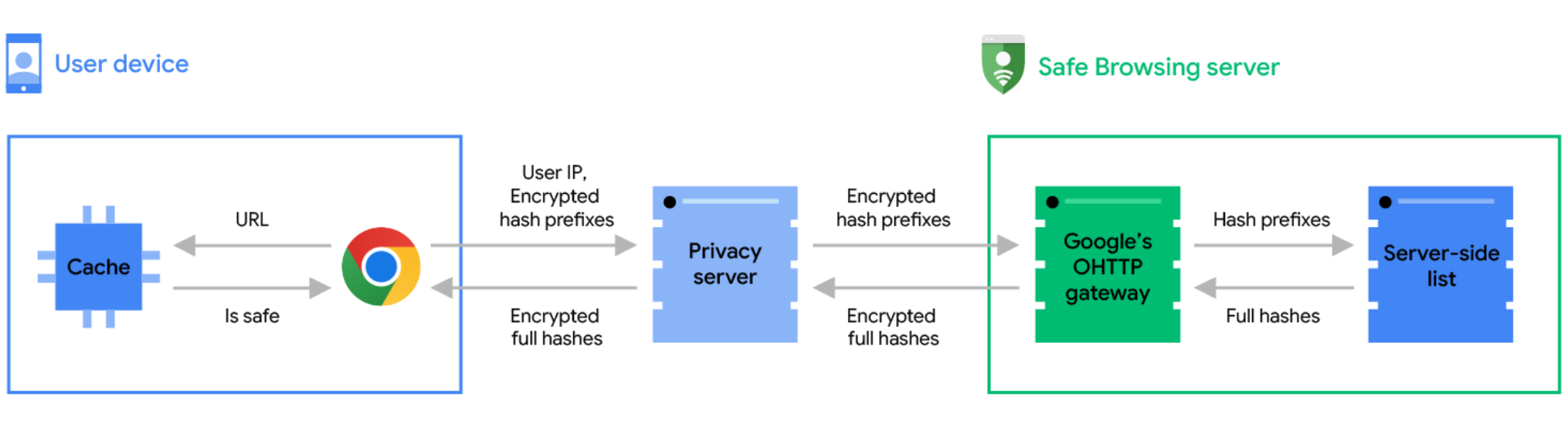
With a view to transition to real-time safety, checks now must be carried out towards an inventory that’s maintained on the Protected Looking server. The server-side listing can embrace unsafe websites as quickly as they’re found, so it is ready to seize websites that swap rapidly. It could actually additionally develop as massive as wanted as a result of the Protected Looking server isn’t constrained in the identical means that consumer units are.
Behind the scenes, this is what is going on in Chrome:
- Once you go to a website, Chrome first checks its cache to see if the handle (URL) of the location is already recognized to be secure (see the “Staying speedy and dependable” part for particulars).
- If the visited URL isn’t within the cache, it could be unsafe, so a real-time test is critical.
- Chrome obfuscates the URL by following the URL hashing steering to transform the URL into 32-byte full hashes.
- Chrome truncates the complete hashes into 4-byte lengthy hash prefixes.
- Chrome encrypts the hash prefixes and sends them to a privateness server (see the “Preserving your knowledge non-public” part for particulars).
- The privateness server removes potential consumer identifiers and forwards the encrypted hash prefixes to the Protected Looking server by way of a TLS connection that mixes requests with many different Chrome customers.
- The Protected Looking server decrypts the hash prefixes and matches them towards the server-side database, returning full hashes of all unsafe URLs that match one of many hash prefixes despatched by Chrome.
- After receiving the unsafe full hashes, Chrome checks them towards the complete hashes of the visited URL.
- If any match is discovered, Chrome will present a warning.
Preserving your knowledge non-public
With a view to protect consumer privateness, we’ve partnered with Fastly, an edge cloud platform that gives content material supply, edge compute, safety, and observability providers, to function an Oblivious HTTP (OHTTP) privateness server between Chrome and Protected Looking – you may study extra about Fastly’s dedication to consumer privateness on their Buyer Belief web page. With OHTTP, Protected Looking doesn’t see your IP handle, and your Protected Looking checks are blended amongst these despatched by different Chrome customers. This implies Protected Looking can not correlate the URL checks you ship as you browse the online.
Earlier than hash prefixes go away your system, Chrome encrypts them utilizing a public key from Protected Looking. These encrypted hash prefixes are then despatched to the privateness server. For the reason that privateness server doesn’t know the non-public key, it can not decrypt the hash prefixes, which presents privateness from the privateness server itself.
The privateness server then removes potential consumer identifiers equivalent to your IP handle and forwards the encrypted hash prefixes to the Protected Looking server. The privateness server is operated independently by Fastly, that means that Google doesn’t have entry to potential consumer identifiers (together with IP handle and Person Agent) from the unique request. As soon as the Protected Looking server receives the encrypted hash prefixes from the privateness server, it decrypts the hash prefixes with its non-public key after which continues to test the server-side listing.
In the end, Protected Looking sees the hash prefixes of your URL however not your IP handle, and the privateness server sees your IP handle however not the hash prefixes. No single celebration has entry to each your id and the hash prefixes. As such, your looking exercise stays non-public.
Actual-time test overview
Staying speedy and dependable
In contrast with the hash-based test, the real-time test requires sending a request to a server, which provides further latency. We now have employed a number of strategies to ensure your looking expertise continues to be clean and responsive.
First, earlier than performing the real-time test, Chrome checks towards a world and native cache in your system to keep away from pointless delay.
- The worldwide cache is an inventory of hashes of known-safe URLs that’s served by Protected Looking. Chrome fetches it within the background. If any full hash of the URL is discovered within the world cache, Chrome will take into account it much less dangerous and carry out a hash-based test as a substitute.
- The native cache, however, is an inventory of full hashes which might be saved from earlier Protected Looking checks. If there’s a match within the native cache, and the cache has not but expired, Chrome won’t ship a real-time request to the Protected Looking server.
Each caches are saved in reminiscence, so it’s a lot quicker to test them than sending a real-time request over the community.
As well as, Chrome follows a fallback mechanism in case of unsuccessful or gradual requests. If the real-time request fails consecutively, Chrome will enter a back-off mode and downgrade the checks to hash-based checks for a sure interval.
We’re additionally within the means of introducing an asynchronous mechanism, which can permit the location to load whereas the real-time test is in progress. This may enhance the consumer expertise, because the real-time test received’t block web page load.
What real-time, privacy-preserving URL safety means for you
Chrome customers
With the newest launch of Chrome for desktop, Android, and iOS, we’re upgrading the Commonplace safety mode of Protected Looking so it would now test websites utilizing Protected Looking’s real-time safety protocol, with out sharing your looking historical past with Google. You needn’t take any motion to profit from this improved performance.
In order for you extra safety, we nonetheless encourage you to activate the Enhanced safety mode of Protected Looking. You would possibly marvel why you want enhanced safety whenever you’ll be getting real-time URL safety in Commonplace safety – it’s because in Commonplace safety mode, the real-time function can solely defend you from websites that Protected Looking has already confirmed to be unsafe. However, Enhanced safety mode is ready to use further data along with superior machine studying fashions to guard you from websites that Protected Looking might not but have confirmed to be unsafe, for instance as a result of the location was solely very lately created or is cloaking its true conduct to Protected Looking’s detection programs.
Enhanced safety additionally continues to supply safety past real-time URL checks, for instance by offering deep scans for suspicious information and additional safety from suspicious Chrome extensions.
Enterprises
The actual-time function of the Commonplace safety mode of Protected Looking is on by default for Chrome. If wanted, it could be configured utilizing the coverage SafeBrowsingProxiedRealTimeChecksAllowed. It’s also value noting that to ensure that this function to work in Chrome, enterprises might have to explicitly permit visitors to the Fastly privateness server. If the server isn’t reachable, Chrome will downgrade the checks to hash-based checks.
Builders
Whereas Chrome is the primary floor the place these protections can be found, we plan to make them accessible to eligible builders for non-commercial use circumstances by way of the Protected Looking API. Utilizing the API, builders and privateness server operators can accomplice to higher defend their merchandise’ customers from fast-moving malicious actors in a privacy-preserving method. To study extra, preserve a watch out for our upcoming developer documentation to be revealed on the Google for Builders website.