
GitHub is being abused to distribute the Lumma Stealer information-stealing malware as pretend fixes posted in mission feedback.
The marketing campaign was first reported by a contributor to the teloxide rust library, who famous on Reddit that they acquired 5 totally different feedback of their GitHub points that pretended to be fixes however have been as an alternative pushing malware.
Additional assessment by BleepingComputer discovered 1000’s of comparable feedback posted to a variety of initiatives on GitHub, all providing pretend fixes to different folks’s questions.
The answer tells folks to obtain a password-protected archive from mediafire.com or via a bit.ly URL and run the executable inside it. Within the present marketing campaign, the password has been “changeme” in all of the feedback we’ve seen.
Reverse engineer Nicholas Sherlock advised BleepingComputer that over 29,000 feedback pushing this malware had been posted over a 3-day interval.
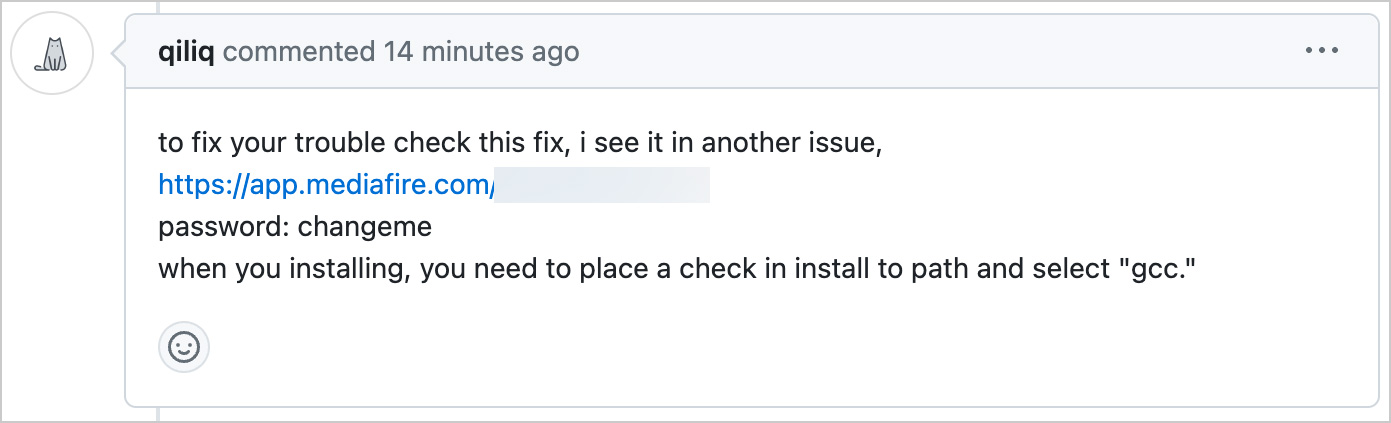
Supply: Andrey Brusnik
Clicking on the hyperlink brings guests to a obtain web page for a file referred to as ‘repair.zip,’ which accommodates just a few DLL information and an executable named x86_64-w64-ranlib.exe.
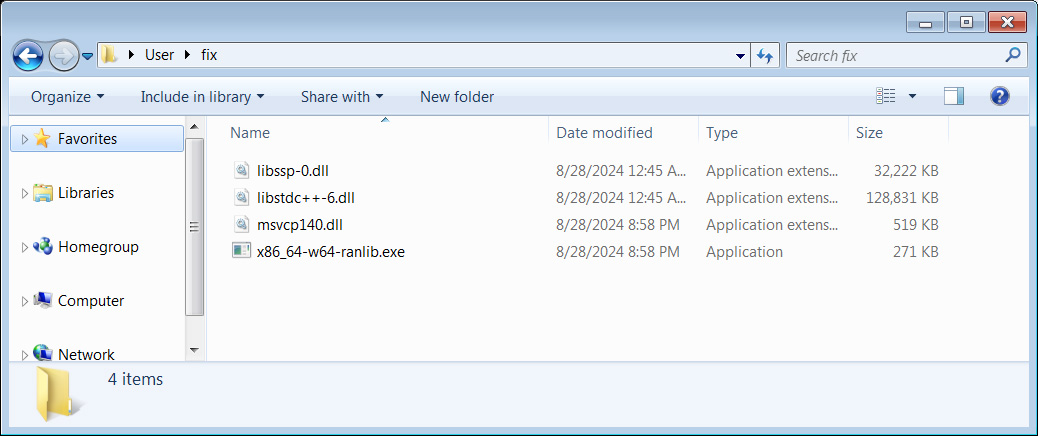
Supply: BleepingComputer
Operating the executable on Any.Run signifies it’s the Lumma Stealer information-stealing malware.
Lumma Stealer is a sophisticated information stealer that, when executed, makes an attempt to steal cookies, credentials, passwords, bank cards, and searching historical past from Google Chrome, Microsoft Edge, Mozilla Firefox, and different Chromium browsers.
The malware may steal cryptocurrency wallets, non-public keys, and textual content information with names like seed.txt, cross.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, phrases, pockets.txt, *.txt, and *.pdf, as these are prone to include non-public crypto keys and passwords.
This knowledge is collected into an archive and despatched again to the attacker, the place they’ll use the data in additional assaults or promote it on cybercrime marketplaces.
Whereas GitHub Employees has been deleting these feedback as they’re detected, folks have already reported falling for the assault.
For many who ran the malware, you have to change the passwords at all of your accounts utilizing a singular password for every website and migrate cryptocurrency to a brand new pockets.
Final month, Verify Level Analysis disclosed an identical marketing campaign by the Stargazer Goblin menace actors, who created a malware Distribution-as-a-Service (DaaS) from over 3,000 pretend accounts on GitHub to push information-stealing malware.
It’s unclear if this is similar marketing campaign or a brand new one carried out by totally different menace actors.
