A brand new wave of cyberattacks attributed to the Ghostwriter Superior Persistent Risk (APT) group has been detected, concentrating on authorities and navy entities in Ukraine and opposition teams in Belarus.
The marketing campaign, lively since late 2024, employs weaponized Excel (XLS) recordsdata embedded with malicious macros to ship malware payloads, underscoring the evolving sophistication of state-sponsored cyber-espionage operations.

Ghostwriter, also referred to as UNC1151 or UAC-0057, has been linked to Belarusian authorities pursuits and has a historical past of mixing disinformation campaigns with hacking.
The newest assaults use Excel paperwork disguised as reputable recordsdata, equivalent to stories on political prisoners or anti-corruption initiatives.
These paperwork lure victims into enabling macros, triggering the execution of obfuscated Visible Fundamental for Purposes (VBA) scripts.
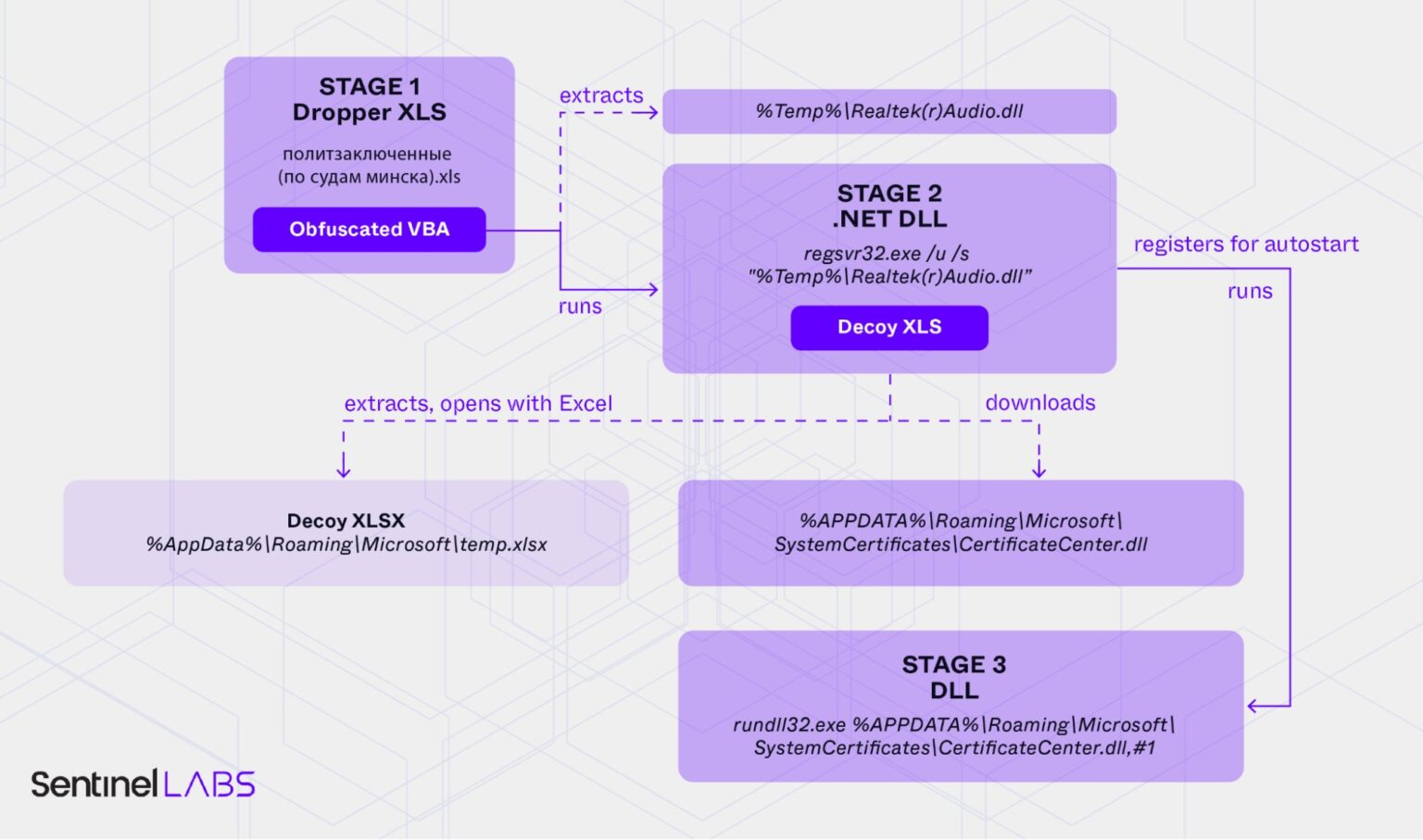
Upon activation, the scripts deploy a downloader malware variant referred to as PicassoLoader, which has been tailored for this marketing campaign.


Technical Particulars of the Assault
The malicious XLS recordsdata are usually delivered by way of phishing emails containing hyperlinks to Google Drive-hosted archives.
As soon as downloaded and opened, the embedded macros execute instructions to drop a DLL file into the system’s short-term listing.
In response to SentinelOne Report, the DLL is then loaded utilizing Home windows’ regsvr32.exe, initiating additional phases of the an infection chain.
The malware employs superior obfuscation strategies utilizing instruments like ConfuserEx and Macropack to evade detection by safety software program.
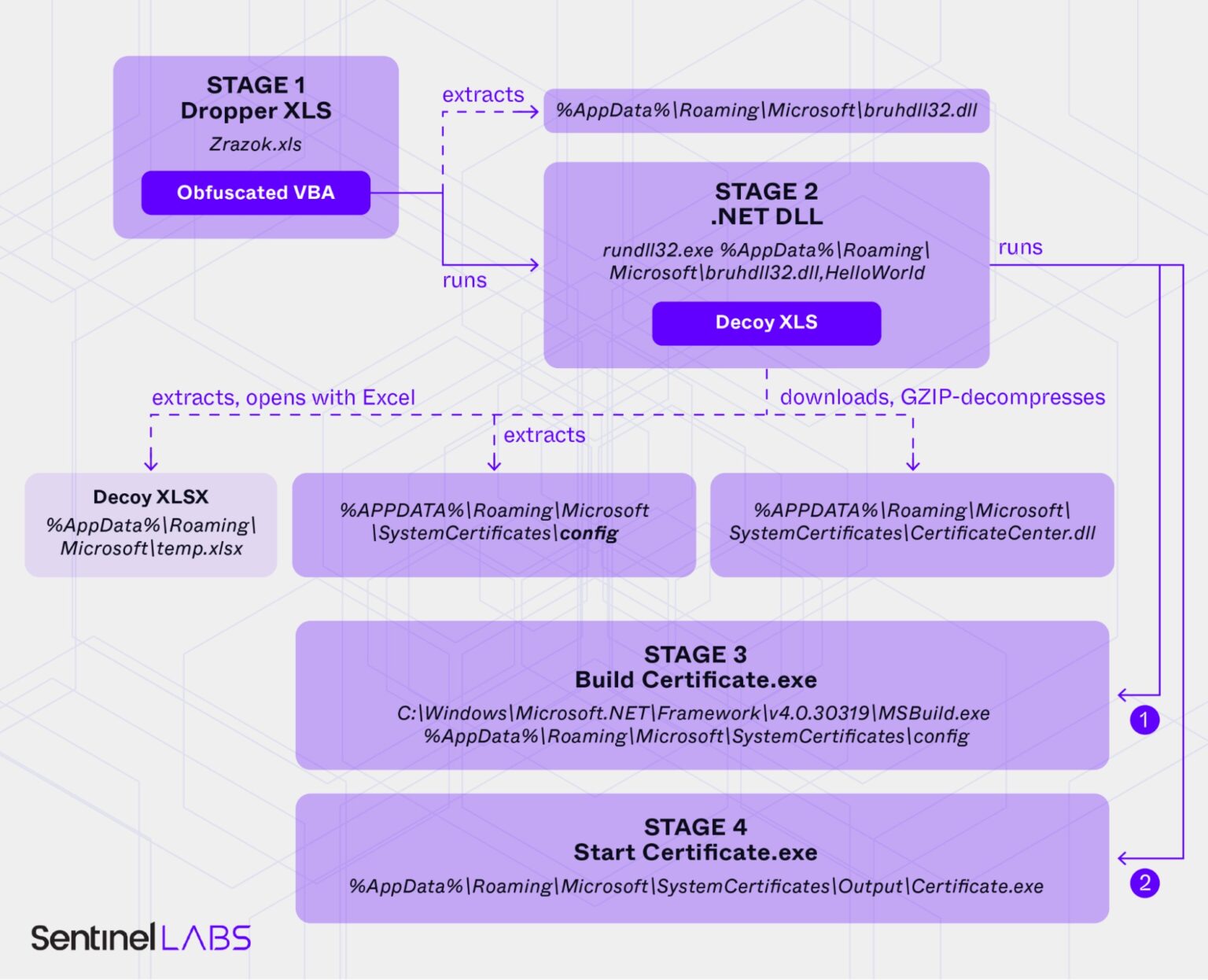

One notable tactic includes creating decoy Excel recordsdata that seem reputable, equivalent to lists of legal costs or authorities initiatives.
These decoys are exhibited to victims whereas the malware operates within the background, downloading further payloads from command-and-control (C2) servers hosted on domains mimicking reputable web sites.
For instance, attackers have reused publicly out there JPEG photographs from genuine blogs however altered their URLs to level to malicious servers.
The payload supply is very focused, with attackers verifying consumer profiles equivalent to IP addresses and user-agent strings earlier than delivering the ultimate stage malware.
This selective strategy ensures that solely meant victims obtain the dangerous payloads, lowering the probability of detection by researchers or automated defenses.
Broader Implications and Attribution
The Ghostwriter marketing campaign aligns with Belarusian geopolitical pursuits, notably in undermining Ukrainian governmental stability and suppressing home opposition.
The usage of PicassoLoader a malware toolkit solely related to Ghostwriter—additional solidifies attribution to this APT group.
The marketing campaign’s timing coincides with crucial occasions, together with Belarus’ presidential election in January 2025 and ongoing tensions in Ukraine.
This operation highlights the persistent risk posed by state-aligned actors leveraging superior strategies to infiltrate high-value targets.
Organizations in affected areas are urged to bolster their cybersecurity defenses by disabling macros in Workplace paperwork and implementing sturdy e-mail filtering options.
Whereas Belarus formally denies involvement in such actions, Ghostwriter’s continued operations reveal a coordinated effort to conduct cyber-espionage in help of its strategic aims.
Safety researchers emphasize vigilance towards comparable assaults as geopolitical conflicts more and more spill into our on-line world.
Acquire Risk Intelligence on the Newest Malware and Phishing Assaults with ANY.RUN TI Lookup -> Strive totally free
