
Russian-based RomCom cybercrime group chained two zero-day vulnerabilities in latest assaults focusing on Firefox and Tor Browser customers throughout Europe and North America.
The primary flaw (CVE-2024-9680) is a use-after-free bug in Firefox’s animation timeline characteristic that enables code execution within the internet browser’s sandbox. Mozilla patched this vulnerability on October 9, 2024, sooner or later after ESET reported it.
The second zero-day exploited on this marketing campaign is a privilege escalation flaw (CVE-2024-49039) within the Home windows Activity Scheduler service, permitting attackers to execute code outdoors the Firefox sandbox. Microsoft addressed this safety vulnerability earlier this month, on November 12.
RomCom abused the 2 vulnerabilities as a zero-day chain exploit, which helped them acquire distant code execution with out requiring person interplay. Their targets solely needed to go to an attacker-controlled and maliciously crafted web site that downloaded and executed the RomCom backdoor on their system.
Primarily based on the title of one of many JavaScript exploits used within the assaults (main-tor.js), the menace actors additionally focused Tor Browser customers (variations 12 and 13, in line with ESET’s evaluation).
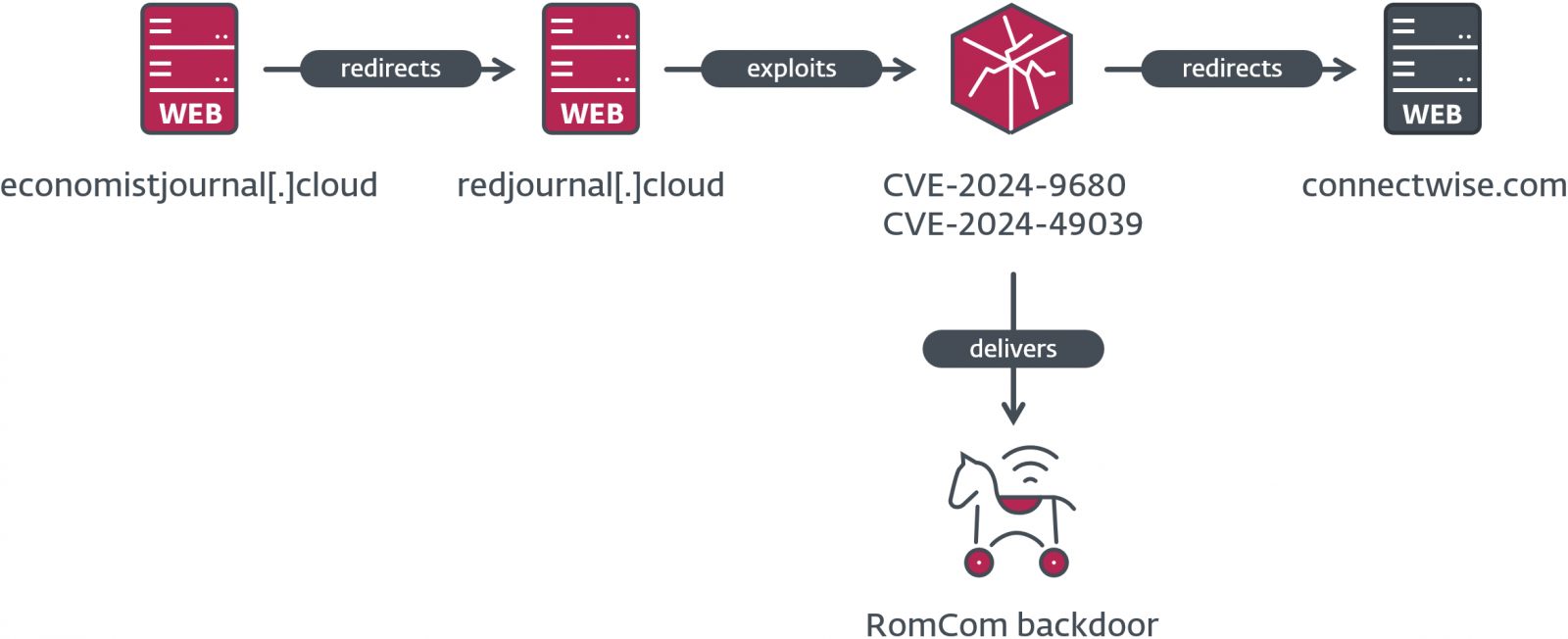
“The compromise chain consists of a faux web site that redirects the potential sufferer to the server internet hosting the exploit, and may the exploit succeed, shellcode is executed that downloads and executes the RomCom backdoor,” mentioned ESET researcher Damien Schaeffer.
“Whereas we do not know the way the hyperlink to the faux web site is distributed, nonetheless, if the web page is reached utilizing a weak browser, a payload is dropped and executed on the sufferer’s laptop with no person interplay required.”
As soon as deployed on a sufferer’s system, this malware enabled the attackers to run instructions and deploy extra payloads.
“Chaining collectively two zero-day vulnerabilities armed RomCom with an exploit that requires no person interplay. This stage of sophistication reveals the menace actor’s will and means to acquire or develop stealthy capabilities,” ESET added.
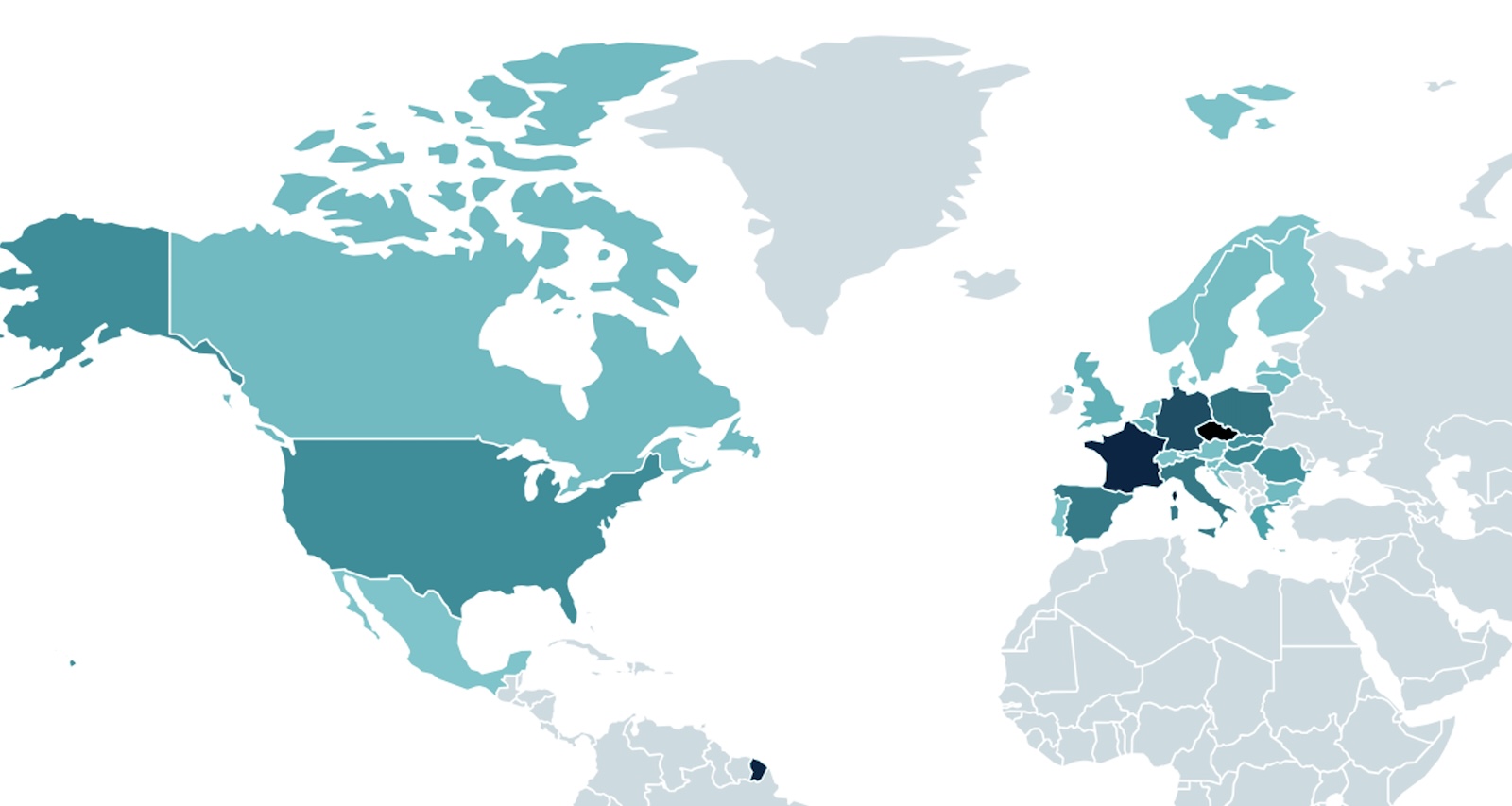
Moreover, the variety of profitable exploitation makes an attempt in these assaults that ended with the RomCom backdoor being deployed on victims’ gadgets led ESET to imagine this was a widespread marketing campaign.
“The variety of potential targets runs from a single sufferer per nation to as many as 250, in line with ESET telemetry,” ESET mentioned.
This is not the primary time RomCom has exploited a zero-day in its assaults. In July 2023, its operators exploited a zero-day (CVE-2023-36884) in a number of Home windows and Workplace merchandise to assault organizations attending the NATO Summit in Vilnius, Lithuania.
RomCom (additionally tracked as Storm-0978, Tropical Scorpius, or UNC2596) has been linked to financially motivated campaigns and orchestrated ransomware and extortion assaults alongside credential theft (possible aimed toward supporting intelligence operations).
The menace group was additionally linked to the Industrial Spy ransomware operation, which has since switched to Underground ransomware.
In keeping with ESET, RomCom is now additionally focusing on organizations in Ukraine, Europe, and North America for espionage assaults throughout varied industries, together with authorities, protection, power, prescription drugs, and insurance coverage.
