
A software for red-team operations known as EDRSilencer has been noticed in malicious incidents making an attempt to determine safety instruments and mute their alerts to administration consoles.
Researchers at cybersecurity firm Development Micro say that attackers are attempting to combine EDRSilencer in assaults to evade detection.
“Our inside telemetry confirmed risk actors making an attempt to combine EDRSilencer of their assaults, repurposing it as a way of evading detection.” – Development Micro.
“Muting” EDR merchandise
Endpoint Detection and Response (EDR) instruments are safety options that monitor and defend gadgets from cyber threats.
They use superior analytics and continuously up to date intelligence to determine threats, each identified and new, and reply mechanically whereas sending an in depth report back to defenders concerning the origin, influence, and unfold of the risk.
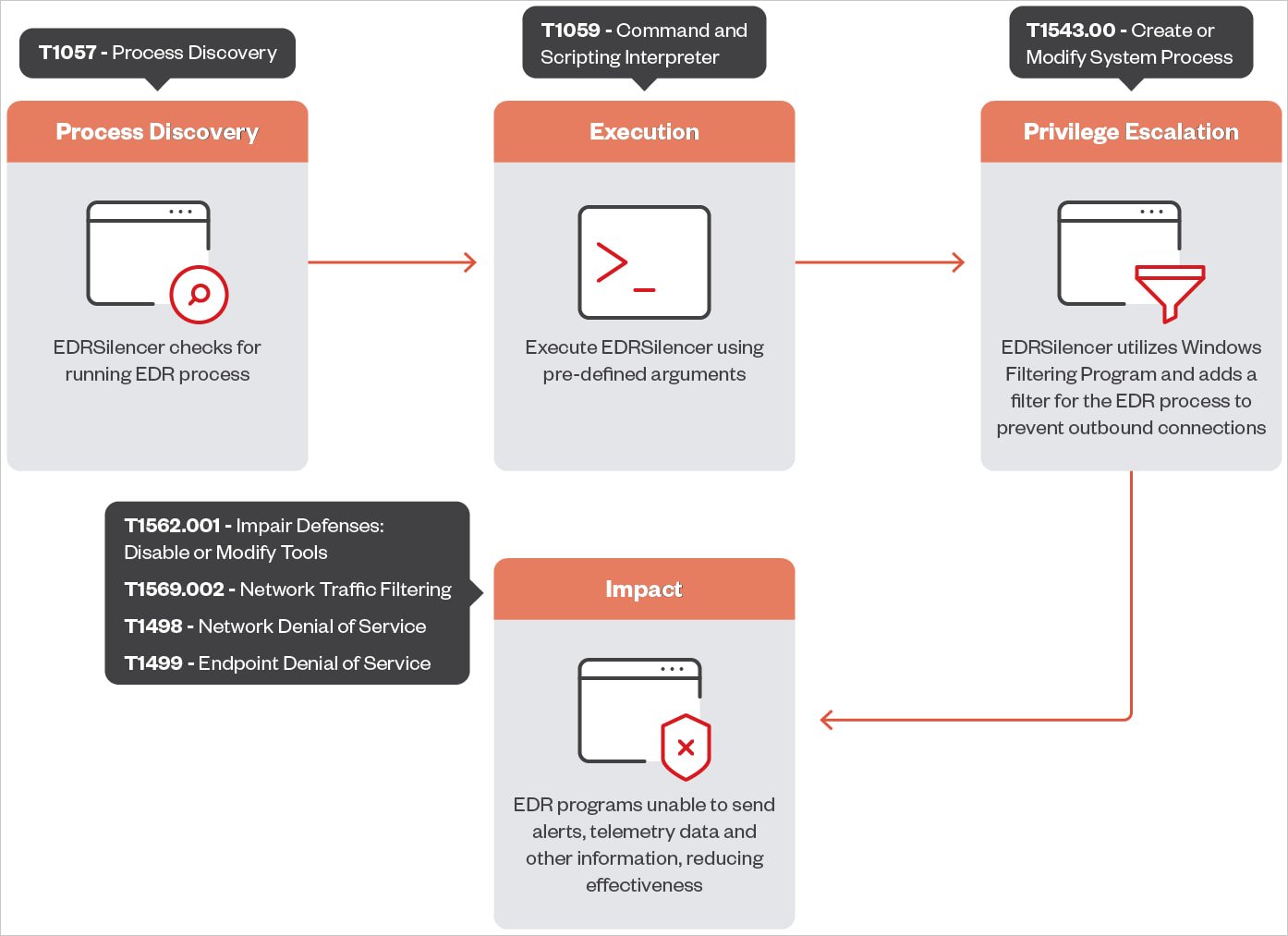
EDRSilencer is an open-source software impressed by MdSec NightHawk FireBlock, a proprietary pen-testing software, which detects working EDR processes and makes use of Home windows Filtering Platform (WFP) to watch, block, or modify community site visitors on IPv4 and IPv6 communication protocol.
WFP is often utilized in safety merchandise equivalent to firewalls, antivirus, and different safety options, and filters set within the platform are persistent.
With customized guidelines in place, an attacker can disrupt the fixed information alternate between an EDR software and its administration server, stopping the supply of alerts and detailed telemetry reviews.
In its newest model, EDRSilencer detects and blocks 16 fashionable EDR instruments, together with:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Safe Endpoint (previously AMP)
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
.jpg)
Supply: Development Micro
TrendMicro’s exams with EDRSilencer confirmed that a few of the impacted EDR instruments should still have the ability to ship reviews resulting from a number of of their executables not being included within the pink workforce software’s hardcoded record.
Nevertheless, EDRSilencer provides attackers the choice so as to add filters for particular processes by offering file paths, so it’s potential to increase the record of focused processes to cowl varied safety instruments.
“After figuring out and blocking further processes not included within the hardcoded record, the EDR instruments did not ship logs, confirming the software’s effectiveness,” Development Micro explains within the report.
“This enables malware or different malicious actions to stay undetected, rising the potential for profitable assaults with out detection or intervention,” the researchers say.
Supply: Development Micro
TrendMicro’s resolution to EDRSilencer is to detect the software as malware, stopping it earlier than it permits the attackers to disable safety instruments.
Moreover, researchers advocate implementing multi-layered safety controls to isolate essential techniques and create redundancy, use safety options that present behavioral evaluation and anomaly detection, search for indicators of compromise on the community, and apply the precept of the least privilege.
