A brand new cyber marketing campaign by the superior persistent menace (APT) group Earth Koshchei has introduced rogue Distant Desktop Protocol (RDP) assaults to the forefront of cybersecurity issues.
Leveraging a mix of RDP relays, rogue RDP servers, and customized malicious configuration information, this marketing campaign has focused high-profile organizations, posing a severe menace to world cybersecurity.
The Rogue RDP Methodology
The rogue RDP method, initially described by Black Hills Data Safety in 2022, entails leveraging RDP relays and malicious RDP configuration information to compromise targets.
By presenting seemingly professional configuration information by way of spear-phishing emails, Earth Koshchei redirected victims’ machines to attacker-controlled RDP servers by means of 193 configured relays.
Free Webinar on Finest Practices for API vulnerability & Penetration Testing: Free Registration
Victims are unknowingly granted partial management of their techniques, enabling attackers to exfiltrate delicate information, alter system settings, and deploy malicious instruments.
Notably, this assault requires no malware set up, relying as a substitute on exploiting native RDP options, making it a stealthy “residing off the land” operation.
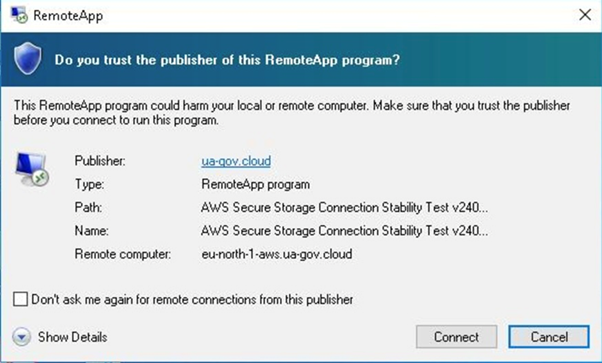

One malicious RDP configuration file redirected customers to a server named eu-south-2-aws[.]zero-trust[.]options—a hostname mimicking an Amazon Net Companies (AWS) server.
As soon as linked, the servers executed a deceptive utility referred to as AWS Safe Storage Connection Stability Check v24091285697854, granting attackers entry to native drives, clipboards, and peripheral units.
Earth Koshchei’s rogue RDP marketing campaign reached a peak on October 22, 2024, focusing on governments, army organizations, suppose tanks, and educational researchers.

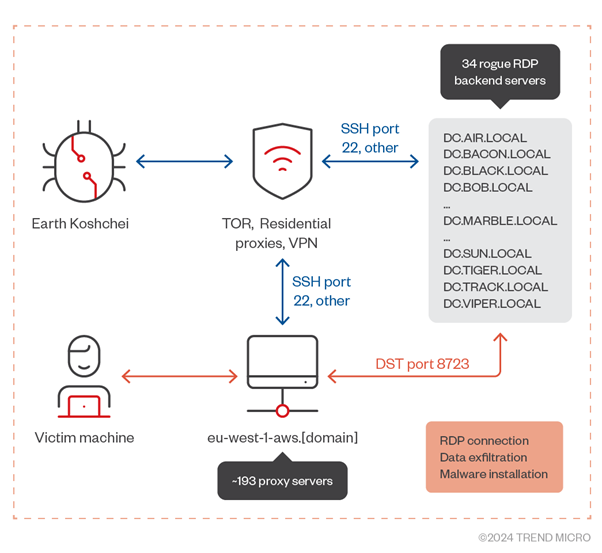
The assault leveraged over 193 proxy domains and 34 rogue RDP backend servers, lots of which mimicked professional organizations to deceive victims. Targets included Ukrainian establishments and entities linked to the Australian and Dutch governments.
Preparations for the marketing campaign started as early as August 7, 2024, with the registration of domains resembling professional organizations.
These domains have been used to masks malicious exercise and funnel site visitors to rogue servers. The marketing campaign culminated in an enormous spear-phishing e mail wave, however earlier smaller campaigns supplied a testbed for the methodology.

Between October 18 and 21, Earth Koshchei reportedly used their infrastructure for information exfiltration focusing on army entities and a cloud companies supplier.
Subtle Infrastructure and Anonymization
Earth Koshchei demonstrated a complicated operational setup, involving anonymization methods like digital non-public networks (VPNs), residential proxies, and TOR.
By routing operations by means of these companies, the attackers bypassed IP-based detection mechanisms, masking their actions below layers of professional site visitors.
The malicious emails have been despatched from 5 compromised professional mail servers, accessed by way of residential proxies and business VPNs. Roughly 90 distinctive IP addresses, together with TOR exit nodes, have been traced again to the e-mail campaigns.
Every of the 193 proxy domains acted as a conduit to hide 34 backend rogue RDP servers, which have been used to intercept and manipulate RDP classes.
Determine 3 within the evaluation illustrated how attackers maintained management over their infrastructure utilizing SSH, TOR, and peer-to-peer VPNs.
Microsoft and Amazon attributed the marketing campaign to Midnight Blizzard (APT29), which aligns with Development Micro’s monitoring of Earth Koshchei.
The group, allegedly linked to Russia’s Overseas Intelligence Service (SVR), has a historical past of focusing on Western governments, army organizations, and demanding industries for espionage functions.
Their versatile techniques, methods, and procedures (TTPs), together with brute power assaults, watering gap methods, and spear-phishing, have been honed over years of cyber operations.
The dimensions of this RDP marketing campaign—impacting over 200 high-profile targets in a single day—underscores the rising sophistication of cyber espionage techniques.
- Limit RDP Entry: Organizations should implement strict controls on RDP utilization, together with proscribing entry to trusted IP ranges and disabling unused RDP companies.
- Monitor Configuration Recordsdata: Any inbound RDP configuration information needs to be rigorously analyzed for malicious parameters.
- Improve Electronic mail Safety: Superior spear-phishing makes an attempt spotlight the essential want for sturdy e mail filtering, consumer coaching, and menace intelligence integration.
- Undertake Community Segmentation: Segmentation can mitigate danger by limiting attacker lateral motion in case of compromise.
- Deploy Risk Intelligence: Insights into adversary methods like anonymization layers will help to proactively block malicious exercise.
The Earth Koshchei marketing campaign exemplifies the dire penalties of lapses in cybersecurity, urging organizations to remain vigilant in opposition to quickly evolving APT strategies.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free

