
New variants of the Eagerbee malware framework are being deployed towards authorities organizations and web service suppliers (ISPs) within the Center East.
Beforehand, the malware was seen in assaults performed by Chinese language state-backed risk actors who Sophos tracked as ‘Crimson Palace.’
In response to a brand new report by Kaspersky researchers, there is a potential connection to a risk group they name ‘CoughingDown,’ primarily based on code similarities and IP handle overlaps.
“Due to the constant creation of providers on the identical day through the identical webshell to execute the EAGERBEE backdoor and the CoughingDown Core Module, and the C2 area overlap between the EAGERBEE backdoor and the CoughingDown Core Module, we assess with medium confidence that the EAGERBEE backdoor is expounded to the CoughingDown risk group” explains Kaspersky
The Eagerbee malware framework
Kaspersky could not decide the preliminary entry vector within the Center East assaults however studies that, in earlier instances, two East Asian organizations have been breached through the exploitation of the Microsoft Alternate ProxyLogon flaw (CVE-2021-26855).
The assault includes the deployment of an injector (tsvipsrv.dll) dropped within the system32 listing to load the payload file (ntusers0.dat).
Upon system begin, Home windows executes the injector, which then abuses the ‘Themes’ service, in addition to SessionEnv, IKEEXT, and MSDTC, to jot down the backdoor payload in reminiscence utilizing DLL hijacking.
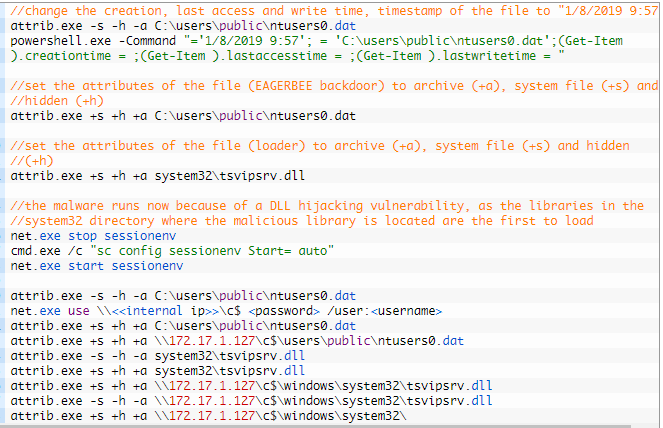
Supply: Kaspersky
The backdoor might be configured to execute at particular occasions, however Kaspersky says it was set to run 24/7 within the noticed assaults.
Eagerbee seems on the contaminated system as ‘dllloader1x64.dll’ and instantly begins amassing primary info like OS particulars and community addresses.
Upon initialization, it establishes a TCP/SSL channel with the command-and-control (C2) server from the place it will possibly obtain further plugins that reach its performance.
The plugins are injected into reminiscence by a plugin orchestrator (ssss.dll), which manages their execution.
The 5 plugins documented by Kaspersky are the next:
- File Supervisor Plugin: Handles file system operations, together with itemizing, renaming, transferring, copying, and deleting recordsdata or directories. It will probably alter file permissions, inject further payloads into reminiscence, and execute command strains. It additionally retrieves detailed file and folder constructions and manages quantity labels and timestamps.
- Course of Supervisor Plugin: Manages system processes by itemizing operating processes, launching new ones, and terminating present ones. It will probably execute command strains or modules within the safety context of particular consumer accounts.
- Distant Entry Supervisor Plugin: Facilitates distant entry by enabling RDP classes, sustaining concurrent RDP connections, and offering command shell entry. It additionally downloads recordsdata from specified URLs and injects command shells into authentic processes for stealth.
- Service Supervisor Plugin: Controls system providers by creating, beginning, stopping, deleting, or enumerating them. It will probably handle each standalone and shared service processes whereas amassing service standing particulars.
- Community Supervisor Plugin: Screens and lists lively community connections, gathering particulars like state, native/distant addresses and ports, and related course of IDs for each IPv4 and IPv6 protocols.
Total, Eagerbee is a stealthy and protracted risk that has intensive capabilities on compromised techniques.
The identical backdoor-loading chain was additionally found in Japan, so the assaults are world.
Organizations ought to patch ProxyLogon on all Alternate servers and use the symptoms of compromise listed in Kaspersky’s report back to catch the risk early.
