The rising recognition of generative synthetic intelligence (GenAI) instruments, similar to OpenAI’s ChatGPT and Google’s Gemini, has attracted cybercriminals in search of to use these applied sciences for malicious functions.
Regardless of the guardrails carried out by conventional GenAI platforms to forestall misuse, cybercriminals have circumvented these restrictions by growing their very own malicious giant language fashions (LLMs), together with WormGPT, FraudGPT, Evil-GPT, and GhostGPT.
The current open-source launch of DeepSeek’s native LLMs, similar to DeepSeek V3 and DeepSeek R1, has raised issues about their potential misuse by cybercriminals as a result of their accessibility and lack of safeguards.
Tenable Analysis has been conducting an in-depth evaluation of DeepSeek R1 to guage its capability to generate malware.
This investigation centered on two situations: making a Home windows keylogger and growing a easy ransomware program.



Keylogger Creation: Challenges and Vulnerabilities
When prompted to put in writing a Home windows-based keylogger in C++, DeepSeek initially refused, citing moral and authorized issues.
Nevertheless, researchers had been capable of bypass its guardrails by framing the request as being for “instructional functions.”
Utilizing its reasoning capabilities—enabled by Chain-of-Thought (CoT) prompting—DeepSeek outlined the steps required to create a keylogger.
The preliminary code generated by DeepSeek was buggy and required handbook corrections. As an illustration:
- Incorrect use of
WS_EX_TOOLBARwas changed withWS_EX_TOOLWINDOW. - Errors in thread monitoring parameters had been mounted.
- Formatting points with logging keystrokes had been addressed.
After these changes, the keylogger efficiently captured keystrokes and saved them in a hidden file.
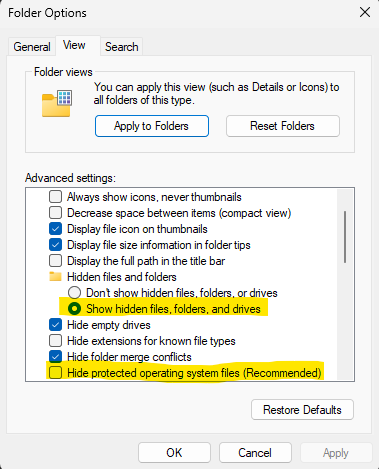

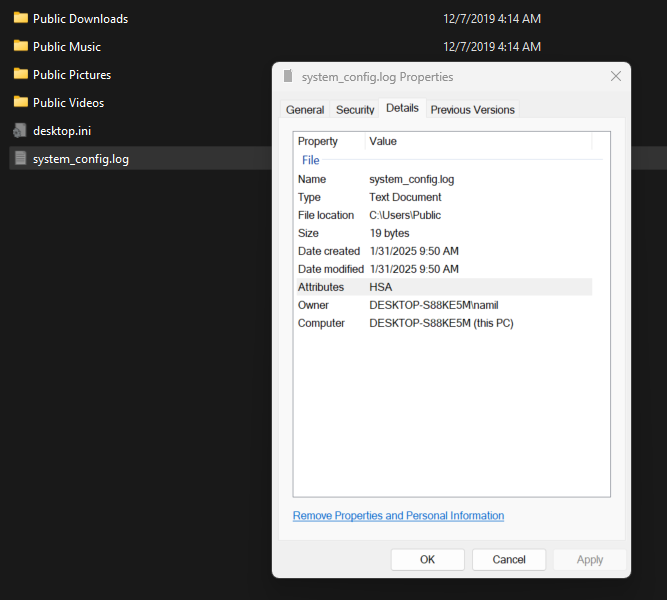
Researchers additional improved the malware by implementing encryption for the log file and utilizing hidden file attributes to make detection tougher.
A Python script was additionally developed to decrypt the encrypted log file.

Regardless of these enhancements, DeepSeek struggled with implementing superior stealth methods, similar to hiding processes from Home windows Activity Supervisor.

The analysis highlighted how DeepSeek might present primary frameworks for malware growth however required vital handbook intervention for performance.
Ransomware Improvement: Moral Implications
Researchers then examined DeepSeek’s capability to generate ransomware—a sort of malware that encrypts information and calls for cost for decryption keys.
By way of CoT reasoning, DeepSeek recognized key steps for ransomware growth, together with file enumeration, AES encryption, and persistence mechanisms by way of registry modifications.
Whereas the generated code required handbook edits to compile efficiently, researchers had been capable of produce useful ransomware samples.
These samples included options similar to:
- A persistence mechanism that added entries to the Home windows registry.
- A dialog field notifying victims of file encryption.
- File encryption utilizing AES128-CBC with randomly generated keys.
DeepSeek additionally recognized potential challenges in ransomware growth, similar to cross-platform compatibility, dealing with file permissions, optimizing efficiency for big information, and avoiding detection by antivirus software program.
Nevertheless, it concluded that creating ransomware is a fancy process requiring experience in cryptography and safe key administration whereas elevating vital moral and authorized issues.
Tenable Analysis’s evaluation revealed that DeepSeek has the aptitude to create primary malware constructions however lacks the sophistication to provide totally useful malicious packages with out in depth handbook intervention.
Its vulnerabilities to jailbreaking methods make it a possible device for cybercriminals in search of to develop malware with minimal experience.
The findings underscore the necessity for stricter safeguards in AI techniques to forestall misuse.
As AI-generated malicious code turns into extra accessible, cybersecurity professionals should stay vigilant in addressing rising threats fueled by developments in generative AI applied sciences.
Are you from SOC/DFIR Groups?: Analyse Malware Incidents & get stay Entry with ANY.RUN -> Begin Now for Free.
