A sweeping evaluation of the Widespread Crawl dataset—a cornerstone of coaching knowledge for giant language fashions (LLMs) like DeepSeek—has uncovered 11,908 dwell API keys, passwords, and credentials embedded in publicly accessible internet pages.
The leaked secrets and techniques, which authenticate efficiently with providers starting from AWS to Slack and Mailchimp, spotlight systemic dangers in AI improvement pipelines as fashions inadvertently study insecure coding practices from uncovered knowledge.
Researchers at Truffle Safety traced the foundation trigger to widespread credential hardcoding throughout 2.76 million internet pages archived within the December 2024 Widespread Crawl snapshot, elevating pressing questions on safeguards for AI-generated code.
The Anatomy of the DeepSeek Coaching Knowledge Publicity
The Widespread Crawl dataset, a 400-terabyte repository of internet content material scraped from 2.67 billion pages, serves as foundational coaching materials for DeepSeek and different main LLMs.
When Truffle Safety scanned this corpus utilizing its open-source TruffleHog device, it found not solely 1000’s of legitimate credentials however troubling reuse patterns.

As an illustration, a single WalkScore API key appeared 57,029 occasions throughout 1,871 subdomains, whereas one webpage contained 17 distinctive Slack webhooks hardcoded into front-end JavaScript.
Mailchimp API keys dominated the leak, with 1,500 distinctive keys enabling potential phishing campaigns and knowledge theft.
Infrastructure at Scale: Scanning 90,000 Internet Archives
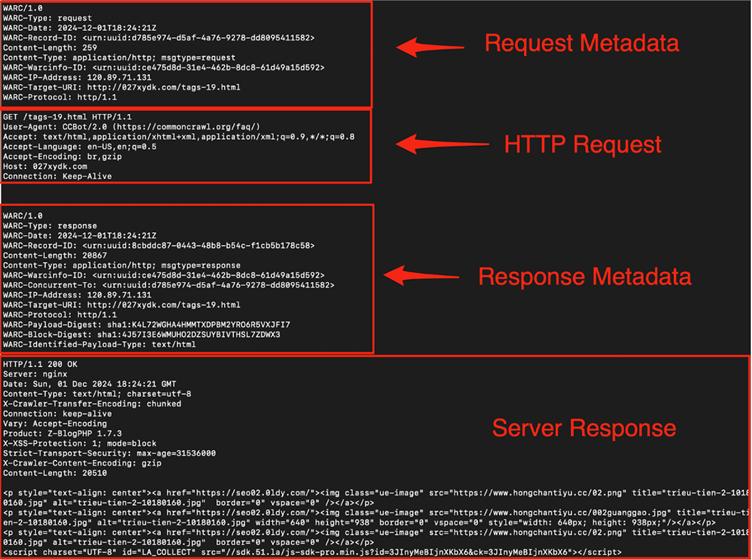
To course of Widespread Crawl’s 90,000 WARC (Internet ARChive) recordsdata, Truffle Safety deployed a distributed system throughout 20 high-performance servers.
Every node downloaded 4GB compressed recordsdata, cut up them into particular person internet information, and ran TruffleHog to detect and confirm dwell secrets and techniques.
To quantify real-world dangers, the crew prioritized verified credentials—keys that actively authenticated with their respective providers.

Notably, 63% of secrets and techniques had been reused throughout a number of websites, amplifying breach potential.
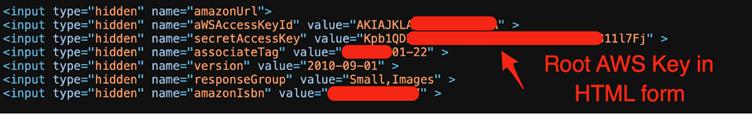
This technical feat revealed startling instances like an AWS root key embedded in front-end HTML for S3 Primary Authentication—a apply with no practical profit however grave safety implications.
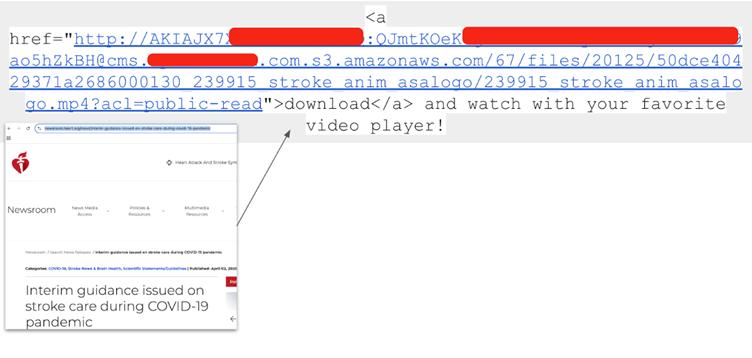
Researchers additionally recognized software program companies recycling API keys throughout shopper websites, inadvertently exposing buyer lists.
Why LLMs Like DeepSeek Amplify the Risk
Whereas Widespread Crawl’s knowledge displays broader web safety failures, integrating these examples into LLM coaching units creates a suggestions loop.
Fashions can not distinguish between dwell keys and placeholder examples throughout coaching, normalizing insecure patterns like credential hardcoding.

This difficulty gained consideration final month when researchers noticed LLMs repeatedly instructing builders to embed secrets and techniques straight into code—a apply traceable to flawed coaching examples.
The Verification Hole in AI-Generated Code
Truffle Safety’s findings underscore a vital blind spot: even when 99% of detected secrets and techniques had been invalid, their sheer quantity of coaching knowledge skews LLM outputs towards insecure suggestions.
As an illustration, a mannequin uncovered to 1000’s of front-end Mailchimp API keys could prioritize comfort over safety, ignoring backend surroundings variables.

This drawback persists throughout all main LLM coaching datasets derived from public code repositories and internet content material.
Trade Responses and Mitigation Methods
In response, Truffle Safety advocates for multilayered safeguards. Builders utilizing AI coding assistants can implement Copilot Directions or Cursor Guidelines to inject safety guardrails into LLM prompts.
For instance, a rule specifying “By no means recommend hardcoded credentials” steers fashions towards safe alternate options.
On an trade degree, researchers suggest strategies like Constitutional AI to embed moral constraints straight into mannequin conduct, decreasing dangerous outputs.
Nevertheless, this requires collaboration between AI builders and cybersecurity specialists to audit coaching knowledge and implement strong redaction pipelines.
This incident underscores the necessity for proactive measures:
- Increase secret scanning to public datasets like Widespread Crawl and GitHub.
- Reevaluate AI coaching pipelines to filter or anonymize delicate knowledge.
- Improve developer training on safe credential administration.
As LLMs like DeepSeek develop into integral to software program improvement, securing their coaching ecosystems isn’t elective—it’s existential.
The 12,000 leaked keys are merely a symptom of a deeper ailment: our collective failure to sanitize the information shaping tomorrow’s AI.
Gather Risk Intelligence on the Newest Malware and Phishing Assaults with ANY.RUN TI Lookup -> Strive without cost
