SAP has issued Safety Observe 3536965 to deal with a number of high-severity vulnerabilities in the Adobe Doc Providers of SAP NetWeaver AS for JAVA.
These vulnerabilities, recognized as CVE-2024-47578, CVE-2024-47579, and CVE-2024-47580, permit attackers to manipulate or add malicious PDF information, doubtlessly compromising inner methods and exposing delicate information.
Particulars of the Vulnerabilities
CVE-2024-47578: Server-Aspect Request Forgery (SSRF)
This flaw permits attackers with administrative privileges to ship specifically crafted requests from a weak net utility.
Exploiting this vulnerability, attackers can entry inner methods behind firewalls, learn or modify delicate information, and even disrupt system availability. Companies may face operational downtime on account of this extreme disruption.
Leveraging 2024 MITRE ATT&CK Outcomes for SME & MSP Cybersecurity Leaders – Attend Free Webinar
CVE-2024-47579: Unauthorized File Manipulation
This vulnerability allows attackers, with administrative rights, to take advantage of an uncovered net service, importing or downloading customized PDF font information.
By abusing this performance, attackers can embed server information into font information and entry delicate information with out impacting system availability or performance.
CVE-2024-47580: PDF File Vulnerability
Right here, attackers can create PDFs containing embedded attachments referencing inner server information.
When these PDFs are downloaded, they supply unauthorized entry to delicate server information, leaving the system’s integrity intact however exposing confidential information.
These vulnerabilities pose extreme threats, together with unauthorized entry to delicate enterprise information, mental property, and personal info.
Exploitation of the SSRF vulnerability may permit attackers to pivot inside inner networks, amplifying the potential injury. Such breaches not solely danger regulatory non-compliance but in addition trigger reputational hurt and monetary losses.
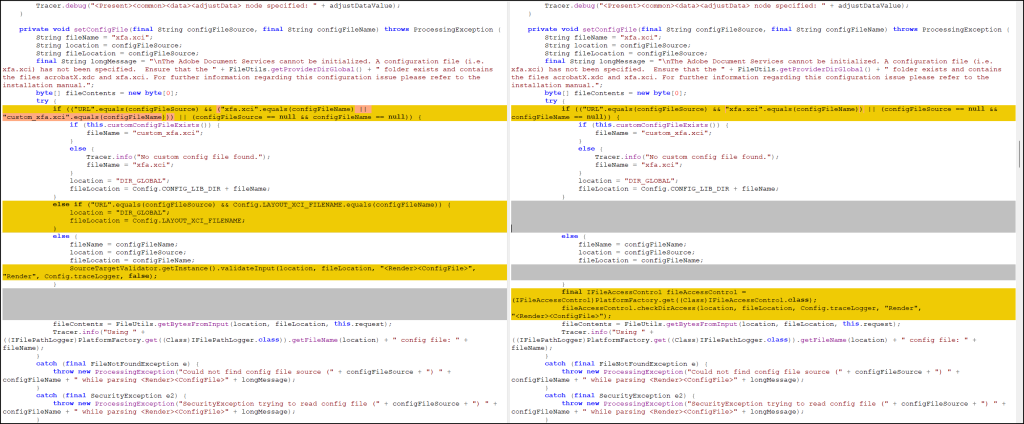

Based on the Redray report, SAP recommends making use of Safety Observe 3536965 to patch these vulnerabilities in all affected SAP NetWeaver AS for JAVA environments. Key steps for mitigation embrace:
- Patch Deployment
Set up the patch directly in all impacted methods. Guarantee Adobe Doc Providers is up to date to the really useful patch stage. - Testing & Monitoring
After making use of the patch, completely take a look at the system to substantiate the vulnerabilities have been resolved. Common monitoring of utility logs is essential for detecting potential prior exploitation. - Entry Controls
Implement the precept of least privilege to limit administrative entry. Allow multi-factor authentication (MFA) for all privileged accounts. - Community Segmentation
Isolate SAP NetWeaver AS for JAVA environments from different community segments, and modify firewall settings to restrict pointless site visitors to and from Adobe Doc Providers. - Common Safety Audits
Conduct vulnerability scans and penetration testing to proactively determine and handle safety gaps.
Enterprises ought to automate patch administration to attenuate publicity time to vulnerabilities and encourage safety consciousness amongst workers.
Usually reviewing SAP Safety Notes and sustaining an incident response plan can additional improve organizational resilience towards cyberattacks.
The invention of CVE-2024-47578, CVE-2024-47579, and CVE-2024-47580 highlights the pressing want for proactive safety measures.
Making use of SAP’s really useful patches and implementing sturdy defenses will assist organizations mitigate dangers and preserve operational stability.
Examine Actual-World Malicious Hyperlinks,Malware & Phishing Assaults With ANY.RUN - Attempt for Free

