
Cloudflare’s ‘pages.dev’ and ‘staff.dev’ domains, used for deploying internet pages and facilitating serverless computing, are being more and more abused by cybercriminals for phishing and different malicious actions.
In accordance with cybersecurity agency Fortra, the abuse of those domains has risen between 100% and 250% in comparison with 2023.
The researchers consider using these domains is aimed toward bettering the legitimacy and effectiveness of those malicious campaigns, making the most of Cloudflare’s trusted branding, service reliability, low utilization prices, and reverse proxying choices that complicate detection.
Cloudflare Pages abuse
Cloudflare Pages is a platform designed for front-end builders to construct, deploy, and host quick, scalable web sites immediately on Cloudflare’s international Content material Supply Community (CDN).
It options static web site internet hosting, helps a spread of contemporary internet app deployment frameworks, and affords SSL/TLS encryption by default, making certain HTTPS connections with out requiring further configuration.
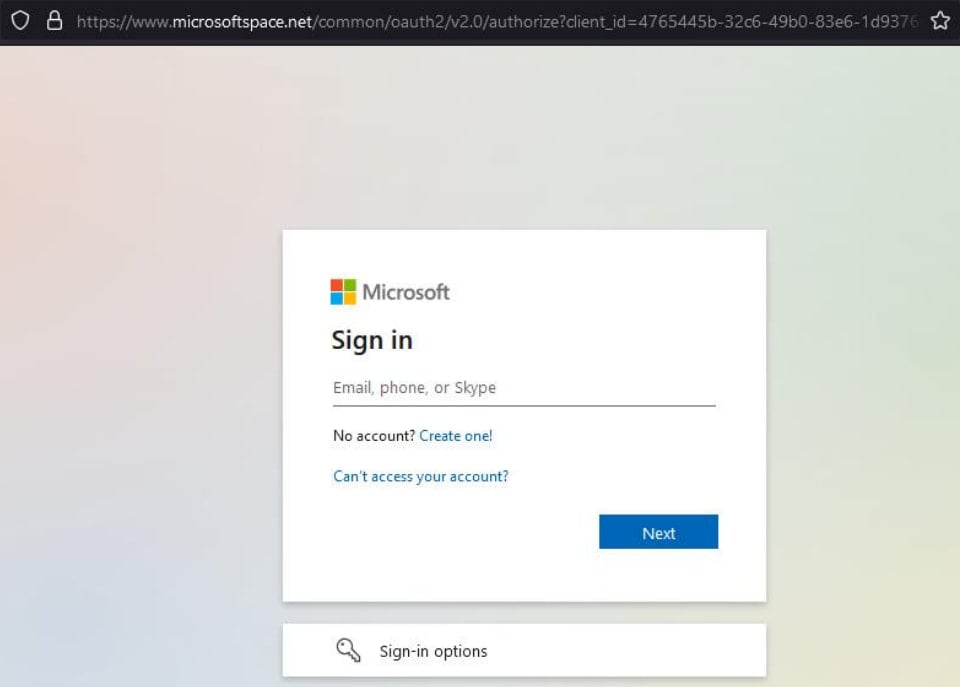
Fortra experiences that Cloudflare Pages has change into a software for cybercriminals who abuse it by internet hosting middleman phishing pages that redirect victims to malicious websites resembling pretend Microsoft Office365 login pages.
Supply: Fortra
Victims are led there by way of hyperlinks embedded in fraudulent PDFs or on phishing electronic mail our bodies, which aren’t flagged by safety merchandise due to Cloudflare’s status.
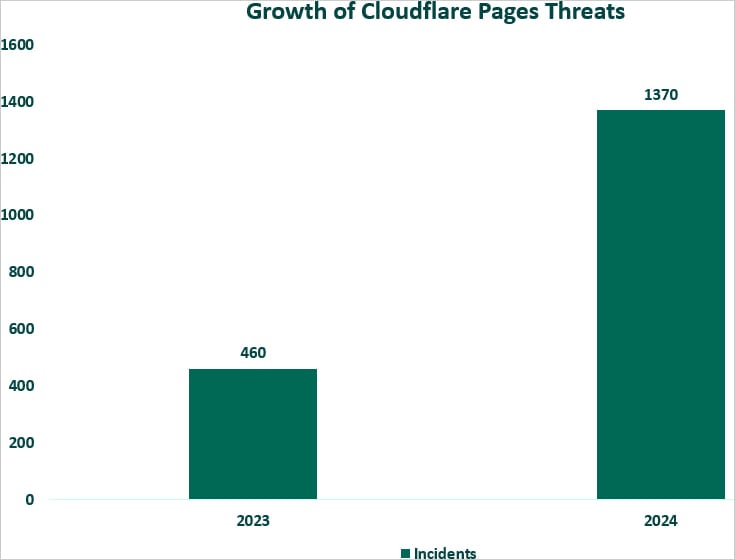
“Fortra’s SEA crew has noticed a 198% improve in phishing assaults on Cloudflare Pages, rising from 460 incidents in 2023 to 1,370 incidents as of mid-October 2024,” experiences Fortra.
“With a median of roughly 137 incidents per thirty days, the overall quantity of assaults is predicted to surpass 1,600 by year-end, representing a projected year-over-year improve of 257%.”
Supply: Fortra
Fortra additionally notes that the menace actors use the “bccfoldering” tactic to cover the dimensions of their electronic mail distribution campaigns.
“In contrast to the cc discipline, which shows the recipients, bccfoldering hides the recipients by including them solely to the e-mail envelope, not the headers,” explains Fortra.
“This makes the recipients undetectable except the server is configured to disclose them. This tactic is utilized by the adversary to hide the dimensions of the phishing marketing campaign, as hid recipients could make it troublesome to detect how giant the phishing marketing campaign is.”

Supply: Fortra
Cloudflare Employees abuse
Cloudflare Employees is a serverless computing platform that permits builders to jot down and deploy light-weight purposes and scripts immediately on Cloudflare’s edge community.
Their authentic makes use of embody API deployment, content material optimization, customized firewall and CAPTCHA implementation, job automation, and the creation of microservices.
Fortra has seen a surge within the abuse of Employees, too, together with for finishing up Distributed Denial of Service (DDoS) assaults, deploying phishing websites, injecting dangerous scripts onto the goal’s browser, and brute-forcing account passwords.
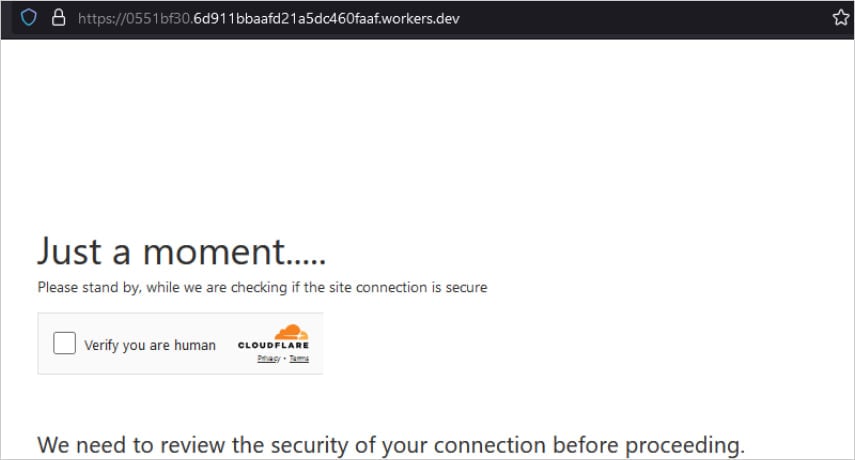
In a single case highlighted by the researchers, Cloudflare Employees is abused for internet hosting a human verification step in a phishing course of so as to add legitimacy.
Supply: Fortra
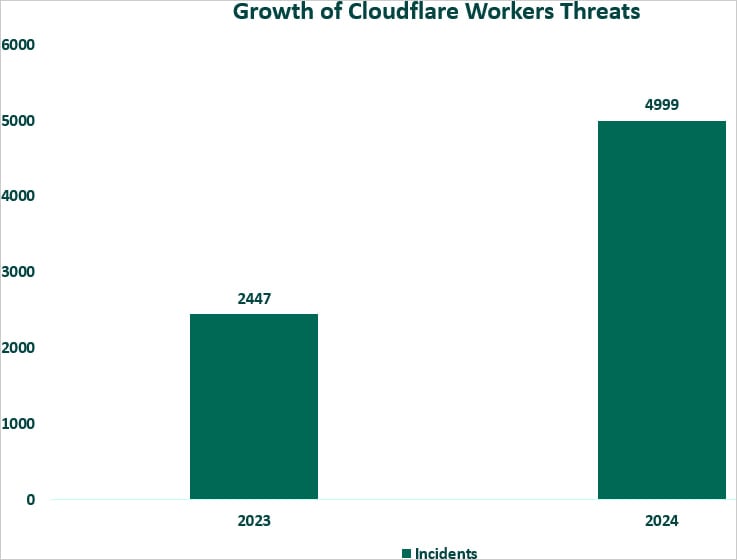
“We’ve got witnessed a 104% surge in phishing assaults on this platform [Cloudflare Workers], climbing from 2,447 incidents in 2023 to 4,999 incidents year-to-date,” reads the Fortra report.
“At the moment averaging 499 incidents per thirty days, the overall quantity is predicted to succeed in virtually 6,000 by year-end, reflecting a projected 145% improve in comparison with the earlier 12 months.”
Supply: Fortra
Customers can defend towards phishing that abuses authentic companies by verifying the authenticity of the URLs they’re on when requested to enter delicate data.
Lastly, activating additional account safety steps resembling two-factor authentication will help forestall takeovers even when the credentials are compromised.
