
The Chinese language state-sponsored Salt Storm hacking group makes use of a customized utility known as JumbledPath to stealthily monitor community site visitors and doubtlessly seize delicate information in cyberattacks on U.S. telecommunication suppliers.
Salt Storm (aka Earth Estries, GhostEmperor, and UNC2286) is a classy hacking group lively since not less than 2019, primarily specializing in breaching authorities entities and telecommunications firms.
Not too long ago, the U.S. authorities have confirmed that Salt Storm was behind a number of profitable breaches of telecommunication service suppliers within the U.S., together with Verizon, AT&T, Lumen Applied sciences, and T-Cell.
It was later revealed that Salt Storm managed to faucet into the personal communications of some U.S. authorities officers and stole info associated to court-authorized wiretapping requests.
Final week, the Recorded Future’s Insikt Group reported that Salt Storm focused over 1,000 Cisco community units, greater than half from the U.S., South America, and India, between December 2024 and January 2025,
In the present day, Cisco Talos revealed extra particulars concerning the risk actor’s exercise after they breached main telecommunications firms within the U.S., which in some instances spanned over three years.
Salt Storm’s ways
Cisco says Salt Storm hackers infiltrated core networking infrastructure primarily by means of stolen credentials. Aside from a single case involving exploitation of the Cisco CVE-2018-0171 flaw, the cybersecurity firm has seen no different flaws, identified or zero-days, being exploited on this marketing campaign.
“No new Cisco vulnerabilities have been found throughout this marketing campaign,” states Cisco Talos in its report. “Whereas there have been some reviews that Salt Storm is abusing three different identified Cisco vulnerabilities, we have now not recognized any proof to substantiate these claims.”
Whereas Salt Storm primarily gained entry to focused networks utilizing stolen credentials, the precise methodology of acquiring the credentials stays unclear.
As soon as inside, they expanded their entry by extracting further credentials from community system configurations and intercepting authentication site visitors (SNMP, TACACS, and RADIUS).
In addition they exfiltrated system configurations over TFTP and FTP to facilitate lateral motion, which contained delicate authentication information, weakly encrypted passwords, and community mapping particulars.
The attackers demonstrated superior methods for persistent entry and evasion, together with steadily pivoting between totally different networking units to cover their traces and utilizing compromised edge units to pivot into accomplice telecom networks.
The risk actors have been additionally noticed modifying community configurations, enabling Visitor Shell entry to execute instructions, altering entry management lists (ACLs), and creating hidden accounts.
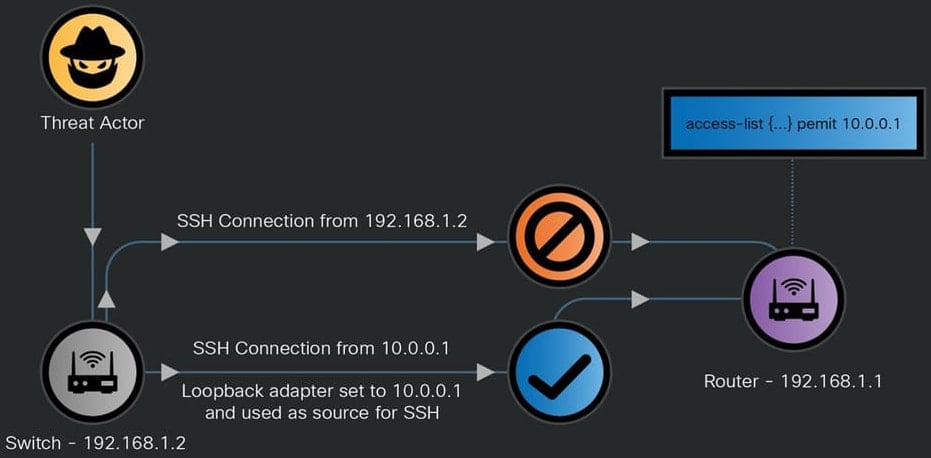
Supply: Cisco
The customized JumbledPath malware
A main element of the Salt Storm assaults was monitoring community exercise and stealing information utilizing packet-capturing instruments like Tcpdump, Tpacap, Embedded Packet Seize, and a customized device known as JumbledPath.
JumpedPath is a Go-based ELF binary constructed for x86_64 Linux-based techniques that allowed it to run on quite a lot of edge networking units from totally different producers, together with Cisco Nexus units.
JumbledPath allowed Salt Storm to provoke packet seize on a focused Cisco system through a jump-host, an middleman system that made the seize requests seem as in the event that they originate from a trusted system contained in the community whereas additionally obfuscating the attacker’s true location.
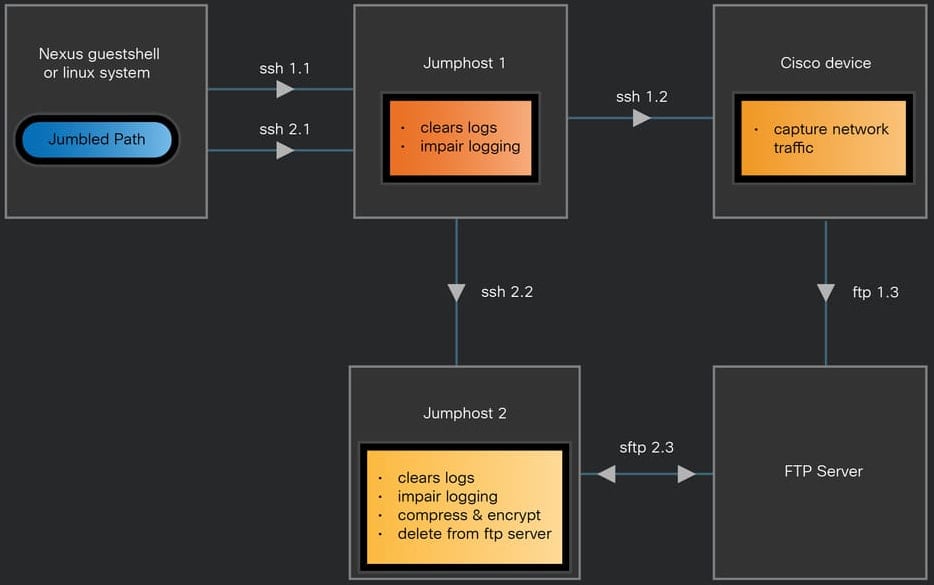
Supply: Cisco
The identical device may additionally disable logging and clear present logs to erase traces of its exercise and make forensic investigations harder.
Cisco lists a number of suggestions to detect Salt Storm exercise, akin to monitoring for unauthorized SSH exercise on non-standard ports, monitoring log anomalies, together with lacking or unusually giant ‘.bash_history’ information, and inspecting for surprising configuration adjustments.
Over the previous couple of years, Chinese language risk actors have more and more focused edge networking units to put in customized malware that permits them to watch community communications, steal credentials, or act as proxy servers for relayed assaults.
These assaults have focused well-known producers, together with Fortinet, Barracuda, SonicWall, Examine Level, D-Hyperlink, Cisco, Juniper, NetGear, and Sophos.
Whereas many of those assaults exploited zero-day vulnerabilities, different units have been breached by means of compromised credentials or older vulnerabilities. Due to this fact, admins should apply patches to edge networking units as quickly as they’re obtainable.
