
A brand new Linux backdoor known as ‘WolfsBane’ has been found, believed to be a port of Home windows malware utilized by the Chinese language ‘Gelsemium’ hacking group.
ESET safety researchers who analyzed WolfsBane report that WolfsBane is an entire malware software that includes a dropper, launcher, and backdoor, whereas it additionally makes use of a modified open-source rootkit to evade detection.
The researchers additionally found ‘FireWood,’ one other Linux malware that seems linked to the ‘Mission Wooden‘ Home windows malware.
Nevertheless, FireWood is extra doubtless a shared software utilized by a number of Chinese language APT teams moderately than an unique/non-public software created by Gelsemium.
ESET says the 2 malware households, each showing on VirusTotal during the last yr, are a part of a broader pattern the place APT teams more and more goal Linux platforms as a result of Home windows safety getting stronger.
“The pattern of APT teams specializing in Linux malware is changing into extra noticeable. We imagine this shift is because of enhancements in Home windows electronic mail and endpoint safety, such because the widespread use of endpoint detection and response (EDR) instruments and Microsoft’s choice to disable Visible Primary for Functions (VBA) macros by default. Consequently, menace actors are exploring new assault avenues, with a rising concentrate on exploiting vulnerabilities in internet-facing programs, most of which run on Linux.”
❖ ESET
WolfsBane’s stealthy howl
WolfsBane is launched to targets through a dropper named ‘cron,’ which drops the launcher part disguised as a KDE desktop part.
Relying on the privileges it runs with, it disables SELinux, creates system service recordsdata, or modifies consumer configuration recordsdata to determine persistence.
The launcher masses the privateness malware part, ‘udevd,’ which masses three encrypted libraries containing its core performance and command and management (C2) communication configuration.
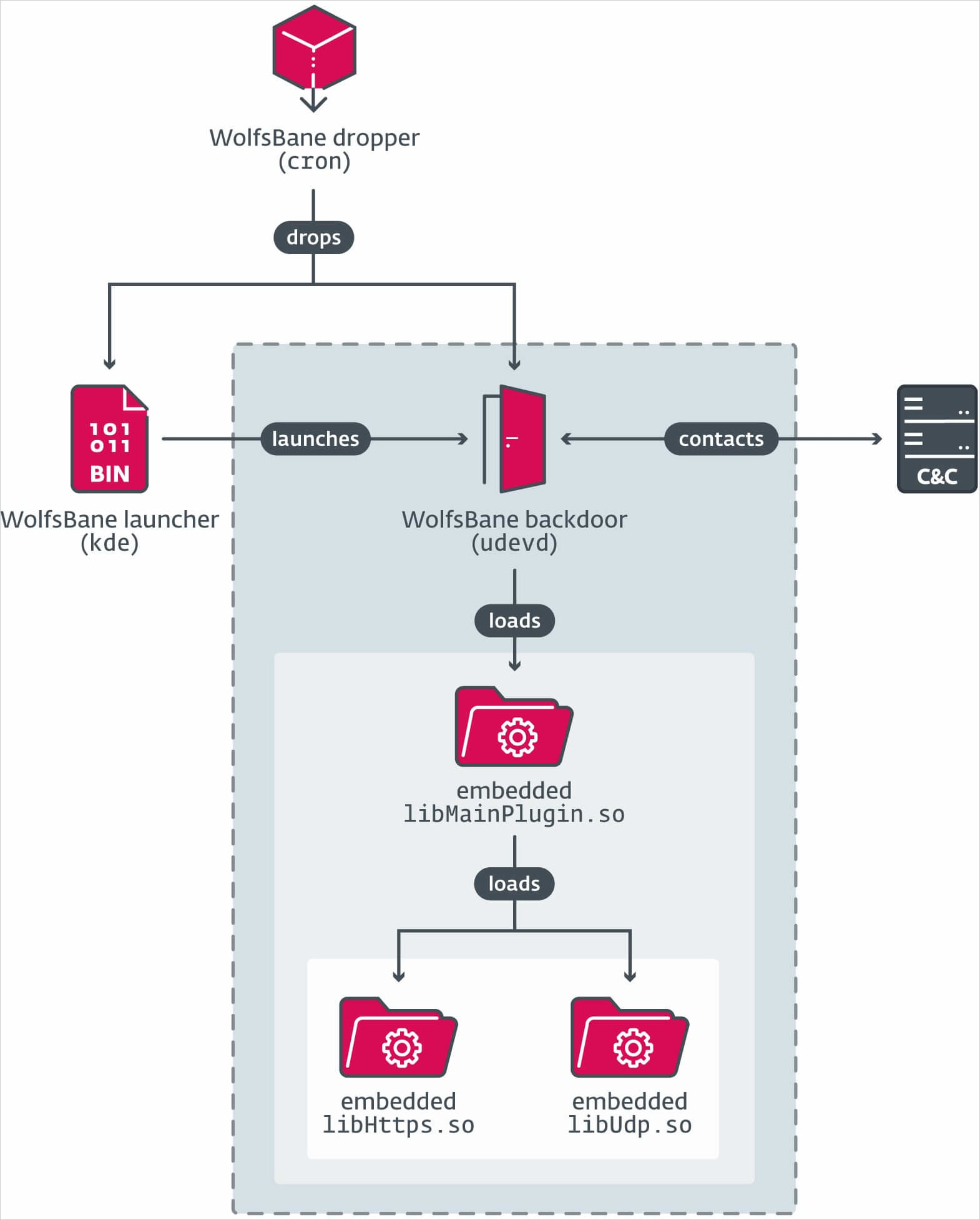
Supply: ESET
Lastly, a modified model of the BEURK userland rootkit is loaded through ‘/and so forth/ld.so.preload’ for system-wide hooking to assist conceal processes, recordsdata, and community site visitors associated to WolfsBane’s actions.
“The WolfsBane Hider rootkit hooks many fundamental customary C library capabilities resembling open, stat, readdir, and entry,” explains ESET.
“Whereas these hooked capabilities invoke the unique ones, they filter out any outcomes associated to the WolfsBane malware.”
WolfsBane’s important operation is to execute instructions obtained from the C2 server utilizing predefined command-function mappings, which is similar mechanism because the one utilized in its Home windows counterpart.
These instructions embody file operations, knowledge exfiltration, and system manipulation, giving Gelsemium complete management over compromised programs.
Supply: ESET
Although solely loosely linked to Gelsemium, FireWood is one other Linux backdoor that would allow versatile, long-term espionage campaigns.
Its command execution capabilities allow operators to carry out file operations, shell command execution, library loading/unloading, and knowledge exfiltration.
ESET recognized a file named ‘usbdev.ko,’ which is suspected of working as a kernel-level rootkit, offering FireWood with the flexibility to cover processes.
The malware units its persistence on the host by creating an autostart file (gnome-control.desktop) in ‘.config/autostart/,’ whereas it could additionally embody instructions on this file to execute them robotically on system startup.
A complete record of indicators of compromise related to the 2 new Linux malware households and Gelsemium’s newest campaigns can be found on this GitHub repository.
