
China’s Salt Storm hackers are nonetheless actively focusing on telecoms worldwide and have breached extra U.S. telecommunications suppliers by way of unpatched Cisco IOS XE community gadgets.
Recorded Future’s Insikt Group menace analysis division states that the Chinese language hacking group (tracked Salt Storm and RedMike) has exploited the CVE-2023-20198 privilege escalation and CVE-2023-20273 Internet UI command injection vulnerabilities.
These ongoing assaults have already resulted in community breaches at a number of telecommunications suppliers, together with a U.S. web service supplier (ISP), a U.S.-based affiliate of a U.Okay. telecommunications supplier, a South African telecom supplier, an Italian ISP, and a big Thailand telecommunications supplier.
The menace researchers stated they’ve noticed compromised and reconfigured Cisco gadgets on their networks, speaking with Salt Storm-controlled servers by way of generic routing encapsulation (GRE) tunnels for persistent entry.
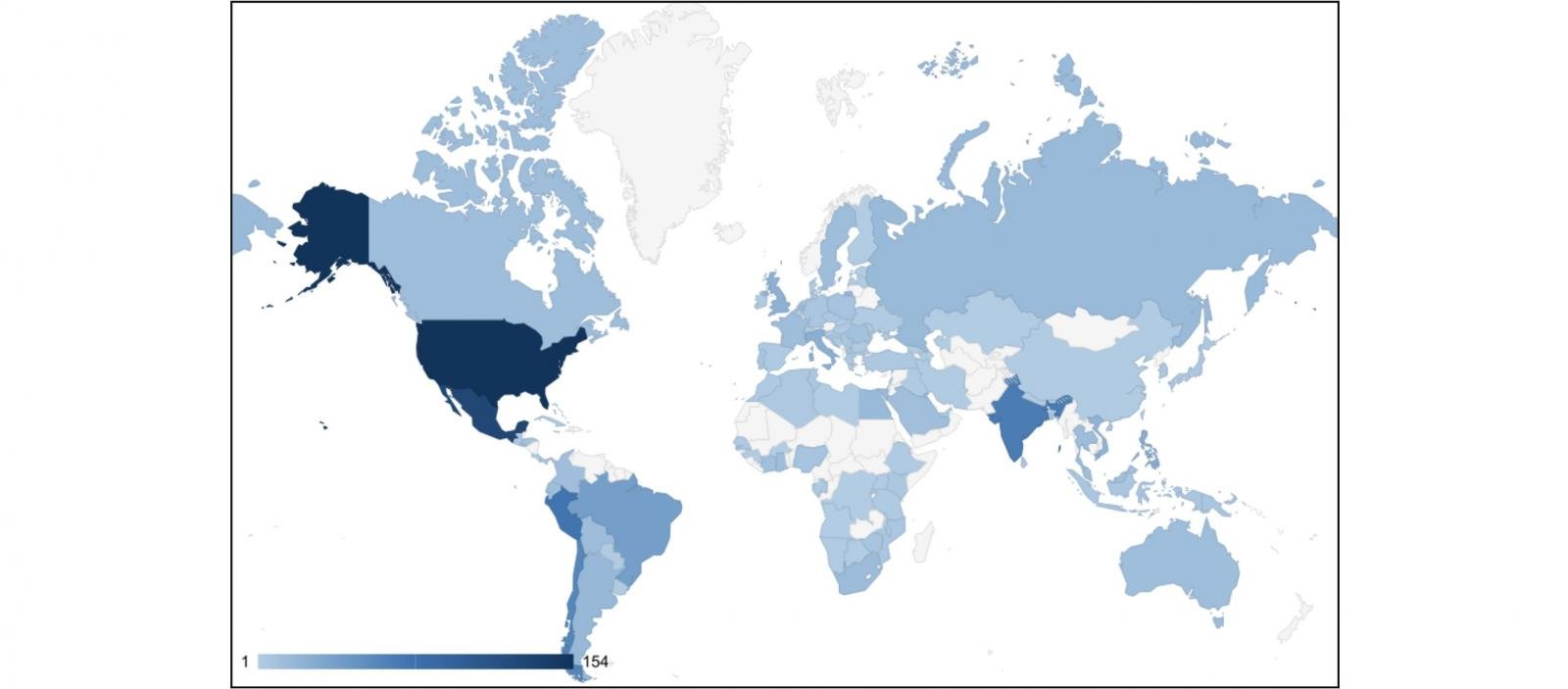
Between December 2024 and January 2025, Salt Storm focused over 1,000 Cisco community gadgets, greater than half from the U.S., South America, and India.
“Utilizing web scanning knowledge, Insikt Group recognized greater than 12,000 Cisco community gadgets with their net UIs uncovered to the web,” Insikt Group stated.
“Though over 1,000 Cisco gadgets had been focused, Insikt Group assesses that this exercise was possible focussed, on condition that this quantity solely represents 8% of the uncovered gadgets and that RedMike engaged in periodic reconnaissance exercise, choosing gadgets linked to telecommunications suppliers.”
Two years in the past, the 2 vulnerabilities had been exploited in zero-day assaults that compromised over 50,000 Cisco IOS XE gadgets, permitting the deployment of backdoor malware by way of rogue privileged accounts. Based on a November advisory from 5 Eyes, these safety flaws had been among the many high 4 most incessantly exploited in 2023.
Iniskt Group advises community admins working Web-exposed Cisco IOS XE community gadgets to use obtainable safety patches as quickly as potential and keep away from exposing administration interfaces or non-essential providers on to the Web.
These breaches are a part of a broader marketing campaign confirmed by the FBI and CISA in October. In these assaults, the Chinese language state hackers breached a number of U.S. telecom carriers (together with AT&T, Verizon, Lumen, Constitution Communications, Consolidated Communications, and Windstream) and telecom firms in dozens of different international locations.
Whereas that they had entry to the U.S. telecoms’ networks, they compromised the “personal communications” of a “restricted quantity” of U.S. authorities officers and accessed the U.S. regulation enforcement’s wiretapping platform.
The Salt Storm Chinese language cyber-espionage group (additionally tracked as FamousSparrow, Ghost Emperor, Earth Estries, and UNC2286) has been breaching telecom firms and authorities entities since not less than 2019.
