The malicious Southeast Asian APT group generally known as OceanLotus (APT32) has been implicated in a complicated assault that compromises the privateness of cybersecurity professionals.
A latest investigation by the ThreatBook Analysis and Response Workforce revealed {that a} well-liked privilege escalation instrument utilized by cybersecurity specialists had been backdoored, resulting in important information breaches and identification leaks.
Methodology of the Assault
The assault, which was first recognized in November 2024, concerned the discharge of a Cobalt Strike exploit plugin embedded with a Trojan onto GitHub.
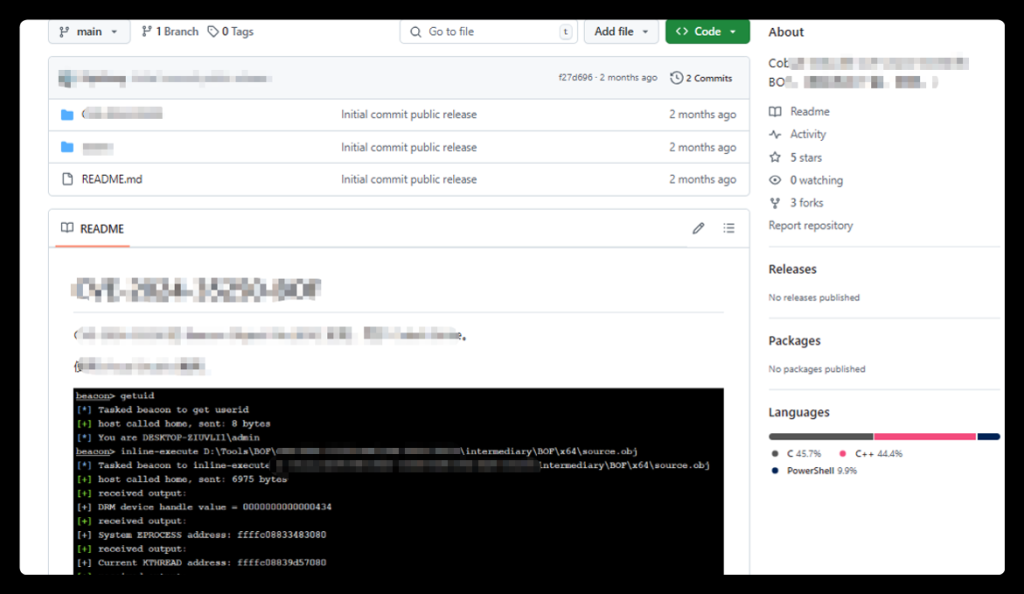

The attackers employed a novel tactic by incorporating a malicious .suo file inside a Visible Studio mission. When unsuspecting customers compile the mission, the Trojan executes mechanically, successfully compromising their techniques.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Strive for Free
The poisoned account, set as much as resemble a respectable safety researcher from a distinguished Chinese language FinTech firm, is linked to the malicious repository at GitHub.
Timeline and Execution
The OceanLotus group focused Chinese language cybersecurity researchers, with the assault commencing between mid-September and early October 2024.

On October 10, the rogue account registered on GitHub, strategically forking varied respectable safety instruments to decrease the victims’ guard.
Inside days, two malevolent initiatives have been revealed, containing Chinese language-language descriptions and aimed particularly at attractive native cybersecurity professionals.
Regardless of the attacker’s subsequent deletion of those initiatives, the poisoned code had already been built-in into different researchers’ repositories, making detection more and more tough.
The code is designed to execute malicious instructions seamlessly whereas self-destructing to keep away from detection.
ThreatBook’s intensive evaluation revealed that the assault was not solely subtle however indicative of OceanLotus’s evolving methods.
By using a mixture of dll hollowing and base64 encoding, the malware establishes command-and-control communication by way of the Notion platform, cleverly circumventing site visitors detection measures.
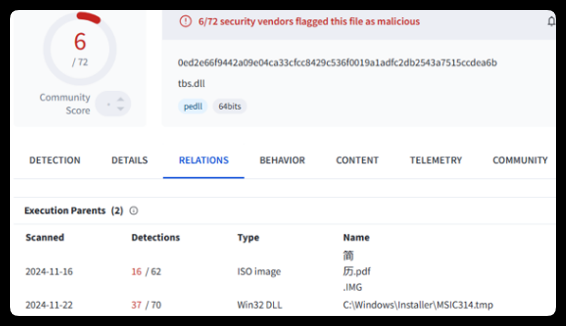

The analysis staff supplied quite a few Indicators of Compromise (IOCs) derived from their analyses, enabling cybersecurity entities to reinforce their defenses in opposition to such focused threats.
ThreatBook’s suite of safety instruments—together with the Menace Detection Platform (TDP) and Cloud Sandbox—has been instrumental in figuring out and mitigating the consequences of this assault.
The OceanLotus group’s use of GitHub for conducting such focused cyber operations raises pressing consciousness concerning software program provide chain vulnerabilities.
Because the cybersecurity panorama turns into more and more complicated, professionals should preserve vigilance and make the most of sturdy safety practices to guard delicate info.
Cybersecurity professionals should stay knowledgeable and proactive in safeguarding their instruments and identities in opposition to such pernicious threats.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates!
