A safety flaw present in Android-based kiosk tablets at luxurious lodges has uncovered a grave vulnerability, doubtlessly permitting attackers to regulate air con, lighting, and different room features remotely.
The investigation, highlighted by safety researchers at LAC Co., Ltd., reveals how these vulnerabilities may compromise visitor privateness and lodge safety.
These gadgets, now commonplace in upscale lodges, provide comfort, controlling facilities like AC, lighting, and room service orders.


Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Risk Intelligence Lookup - Attempt for Free
Vulnerabilities in Android Kiosk Mode Tablets
- USB Debugging Exploitation
The researchers found that USB debugging was activated on the pill beneath sure situations. By rebooting the gadget and shortly connecting it through USB, they bypassed safety settings to allow debugging and accessing delicate gadget knowledge. This might enable attackers to put in malicious functions and even eavesdrop via cameras and microphones.
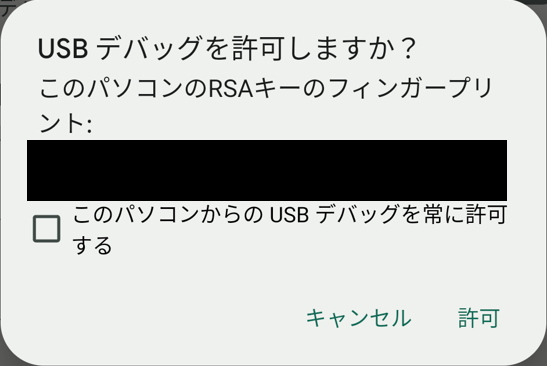

- Short-term Settings Change on Reboot
Between the time the Android working system launched and the kiosk app loaded, attackers may entry system settings, activate debugging, or configure different essential choices.


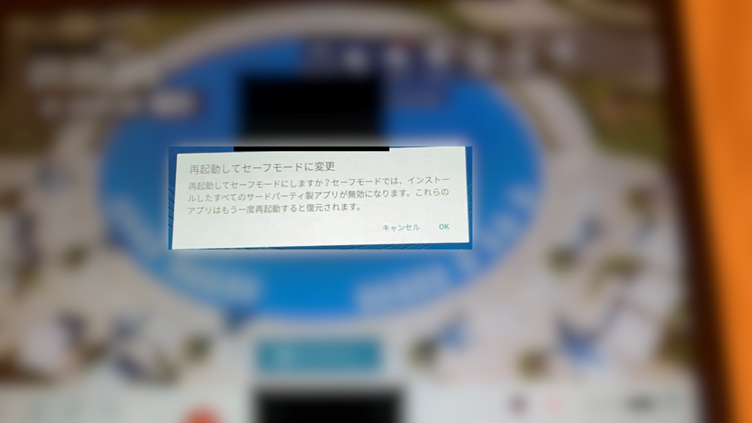
- Protected Mode Exploit
By booting the pill in Protected Mode, the restrictive kiosk app was disabled, exposing the house display screen and permitting attackers to freely navigate the gadget, modify settings, and exploit its options.

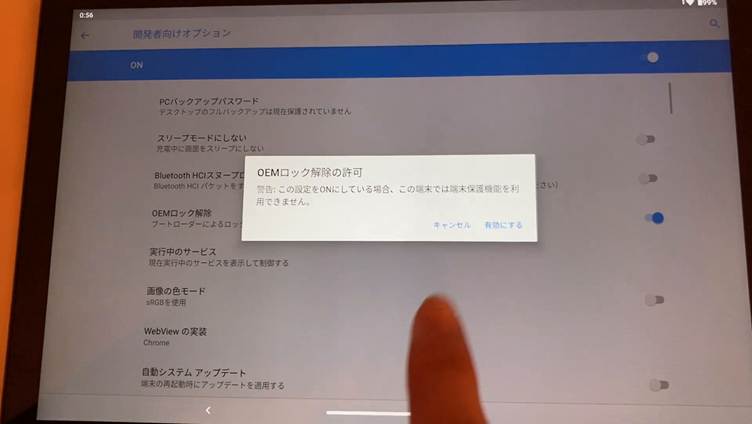
- Potential for Root Entry
By unlocking the bootloader — a course of surprisingly allowed on these tablets — attackers may achieve root privileges, enabling them to completely management the gadget, set up adware, or additional compromise system integrity.

- Community-Primarily based Assaults
Visitor room tablets communicated with a central server controlling lighting and air con. Researchers discovered that authentication between tablets and this server was poorly applied. An attacker may pose as one other room’s gadget by manipulating particular parameters in community requests, gaining management over different rooms’ facilities and even spying on chat communications with the concierge.
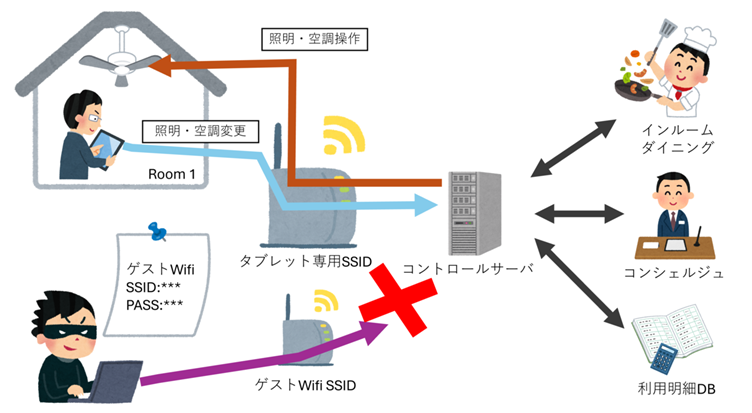

- Weak Wi-Fi Safety
The tablets used a stealth SSID for Wi-Fi communication, protected solely by a passphrase embedded within the app code. As soon as deciphered, this offered attackers with entry to your complete community, rendering much more rooms weak.
The investigation discovered an identical vulnerabilities in kiosk techniques utilized by a number of lodges nationwide, indicating that this was not an remoted challenge however a systemic flaw in how such Android kiosk tablets have been deployed and secured.
The results of those flaws are alarming:
- Distant Management of Visitor Room Features: Attackers may management AC, lights, and room service requests in different visitor rooms.
- Visitor Privateness Breach: By accessing cameras, microphones, or chat logs.
- Harm to Repute: Luxurious lodges may face extreme backlash for compromising visitor experiences and security.
The vulnerabilities have been responsibly disclosed to the affected lodges and the kiosk pill builders via the Data-technology Promotion Company (IPA).
All recognized points have since been patched, and operational techniques up to date. Listed below are the advisable fixes for builders:
- Disable USB Debugging Completely: Guarantee USB debugging is barely accessible throughout licensed upkeep.
- Prohibit System Settings Entry: Forestall modifications throughout reboot by making the kiosk app the default launcher.
- Improve Community Safety: Use WPA Enterprise authentication and shopper certificates to safe Wi-Fi communication.
- Implement Server-Aspect Authentication: Affiliate distinctive credentials with every pill to forestall unauthorized entry to server-controlled features.
- Obfuscate App Code: Cut back ease of research via code encryption and different safety practices.
This vulnerability underscores the essential want for sturdy safety in IoT (Web of Issues) gadgets deployed in delicate environments like lodges.
Builders should take into account not solely the options of their techniques but in addition the potential avenues attackers may exploit. Inns, in flip, should prioritize visitor security and privateness by rigorously testing and auditing third-party techniques.
The vulnerabilities present in Android kiosk tablets spotlight the fragile steadiness between comfort and safety in fashionable know-how.
Whereas these techniques provide unparalleled consolation and customization for friends, additionally they introduce new dangers. Guaranteeing these gadgets are hermetic in opposition to exploitation should be a prime precedence for builders and hoteliers alike.
Integrating Utility Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar

