Current analysis by Development Micro has uncovered a major evolution within the Albabat ransomware, which now targets not solely Home windows but additionally Linux and macOS methods.
This enlargement highlights the rising sophistication of ransomware teams in exploiting a number of working methods to maximise their affect.
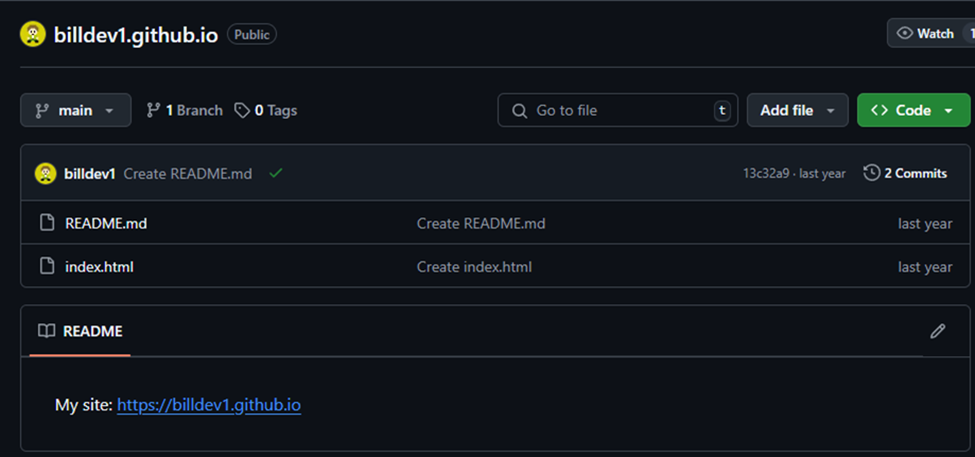
The Albabat group has been leveraging GitHub to streamline its operations, utilizing the platform to handle configuration recordsdata and important elements of the ransomware.


Increasing Targets and Operational Effectivity
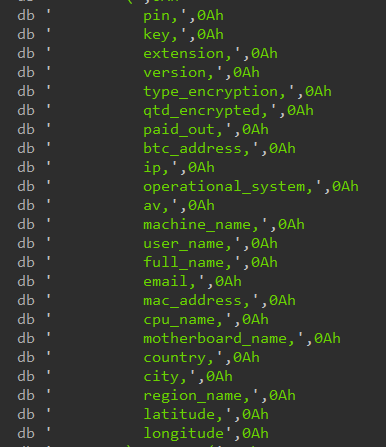
The most recent variations of Albabat ransomware, particularly variations 2.0.0 and a couple of.5, have been designed to assemble system and {hardware} data from Linux and macOS units, along with Home windows.


These variations retrieve their configuration knowledge by the GitHub REST API, using a “Consumer-Agent” string labeled “Superior App.”
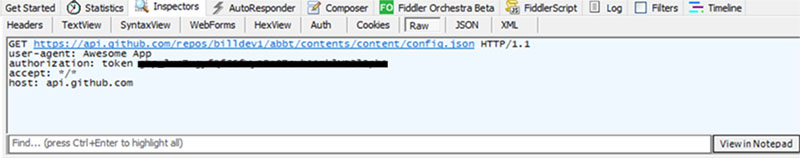

In response to Development Micro Report, this configuration gives essential particulars in regards to the ransomware’s habits and operational parameters, indicating a complicated method to managing and updating the malware.
Using GitHub permits the attackers to take care of a centralized management over the ransomware’s configuration, making it simpler to replace and adapt their techniques.
The ransomware encrypts a variety of file extensions, together with widespread codecs like .exe, .lnk, .dll, and .mp3, whereas skipping particular folders and recordsdata to keep away from detection or interference with system operations.
It additionally terminates varied processes, comparable to activity managers and productiveness software program, to forestall customers from interfering with its actions.
The attackers retailer stolen knowledge in a PostgreSQL database, which helps them monitor infections, monitor funds, and doubtlessly promote delicate data.

Safety Implications and Suggestions
The Albabat ransomware’s means to focus on a number of working methods and its use of GitHub for operational effectivity underscore the necessity for strong cybersecurity measures.

Organizations ought to prioritize sturdy entry controls, common system updates, and safe backups to mitigate the danger of such assaults.
Implementing community segmentation can restrict the unfold of ransomware, whereas person coaching and consciousness packages may also help stop preliminary infections.
Proactive safety options, comparable to AI-powered platforms, can present complete safety by predicting and stopping threats, thereby decreasing the danger of ransomware assaults.
The continued improvement of the Albabat ransomware, with a possible model 2.5 within the works, signifies that these threats will proceed to evolve.
Subsequently, staying knowledgeable about indicators of compromise (IoCs) and leveraging menace intelligence are essential for sustaining efficient cybersecurity defenses towards rising threats like Albabat.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Menace Intelligence Lookup – Strive for Free
