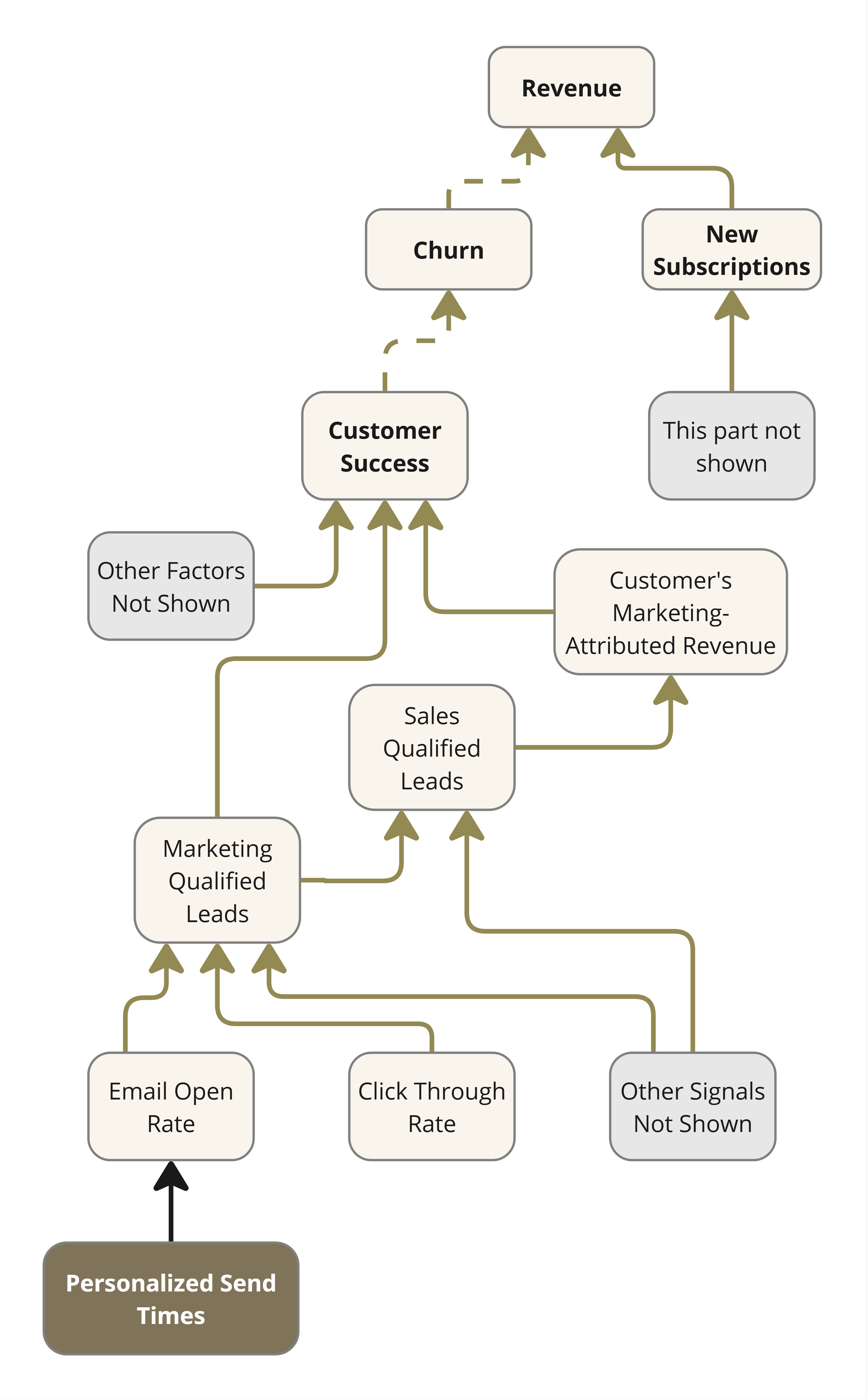
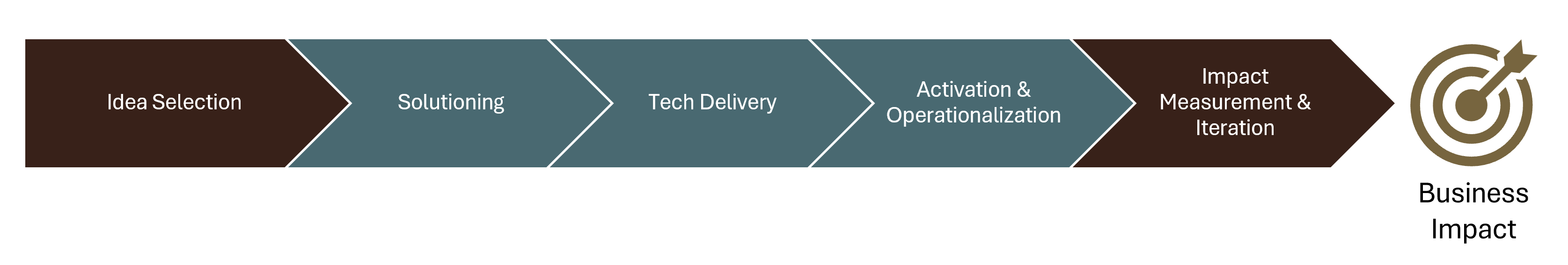
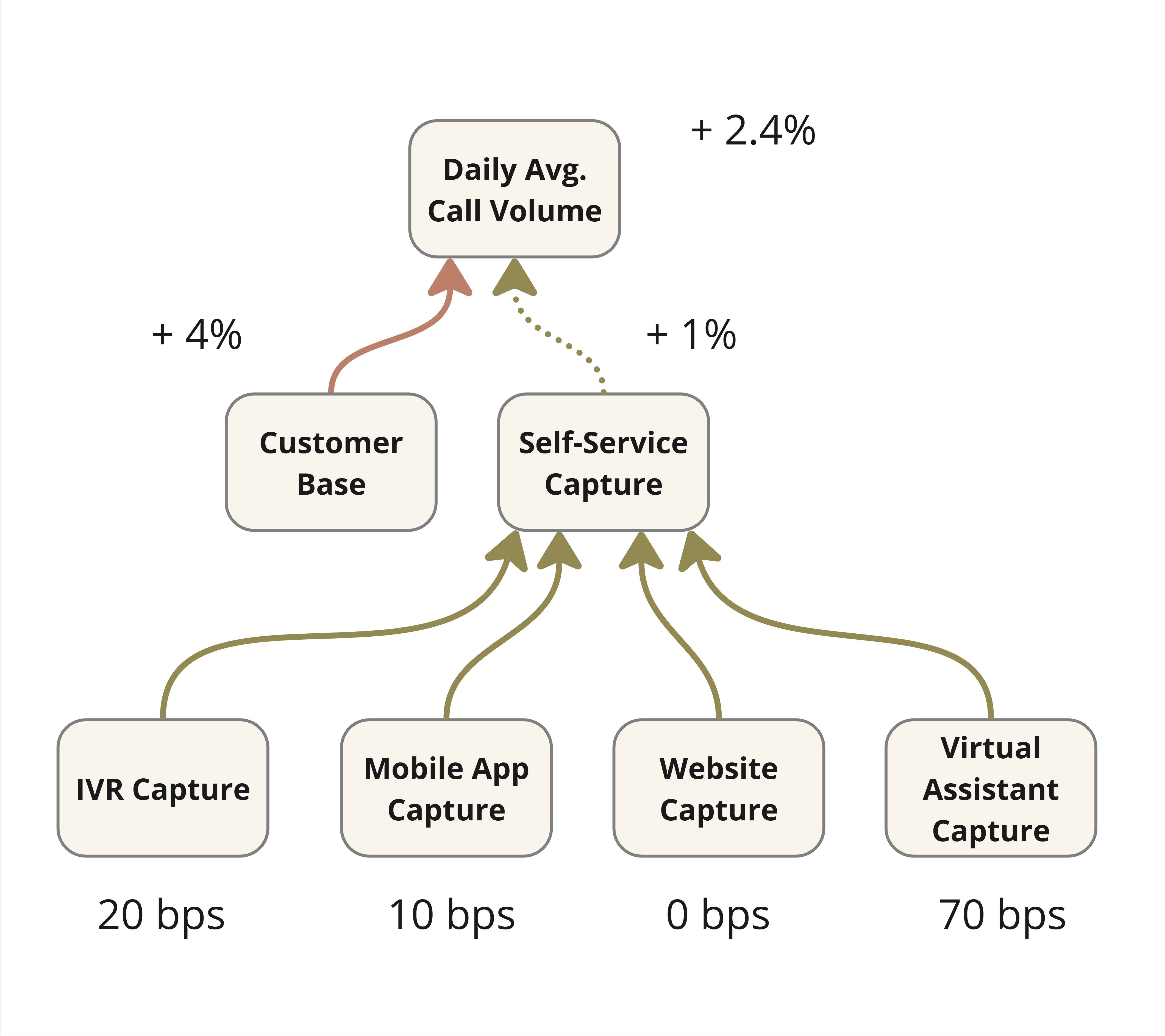
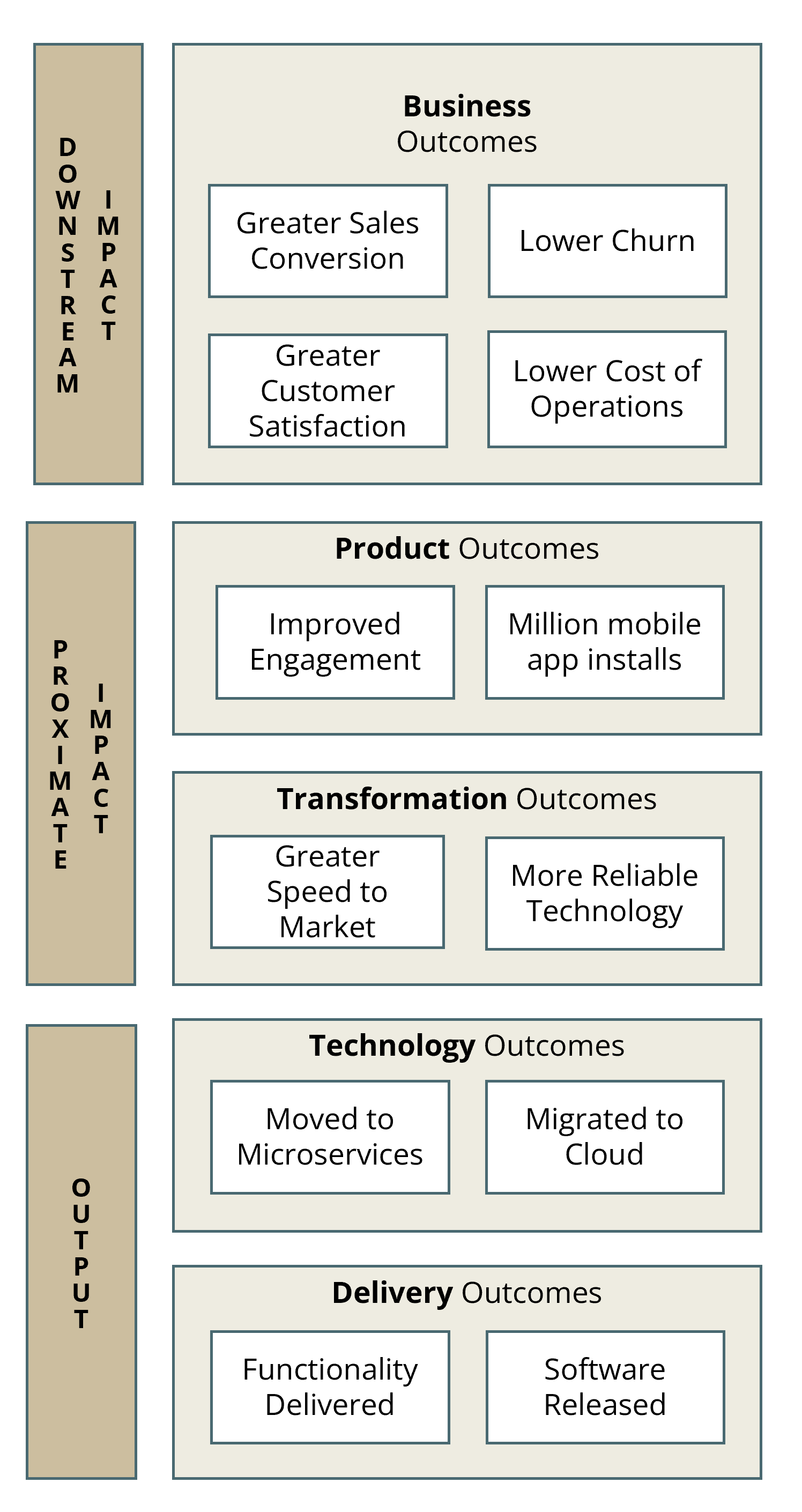
For know-how executives, standardization represents greater than technical housekeeping. It is the systematic means of changing documented brownfield complexity into predictable, automation-ready infrastructure that may scale with enterprise calls for whereas decreasing operational threat.
In my earlier Community Computing articles, I established that we’re within the third period of networking through which networks should work smarter, not simply higher. I then outlined how complete documentation offers the muse for community transformation. Now we flip to standardization: The strategic self-discipline that determines whether or not your community investments ship transformational outcomes or costly disappointment.
The Enterprise Case for Community Standardization
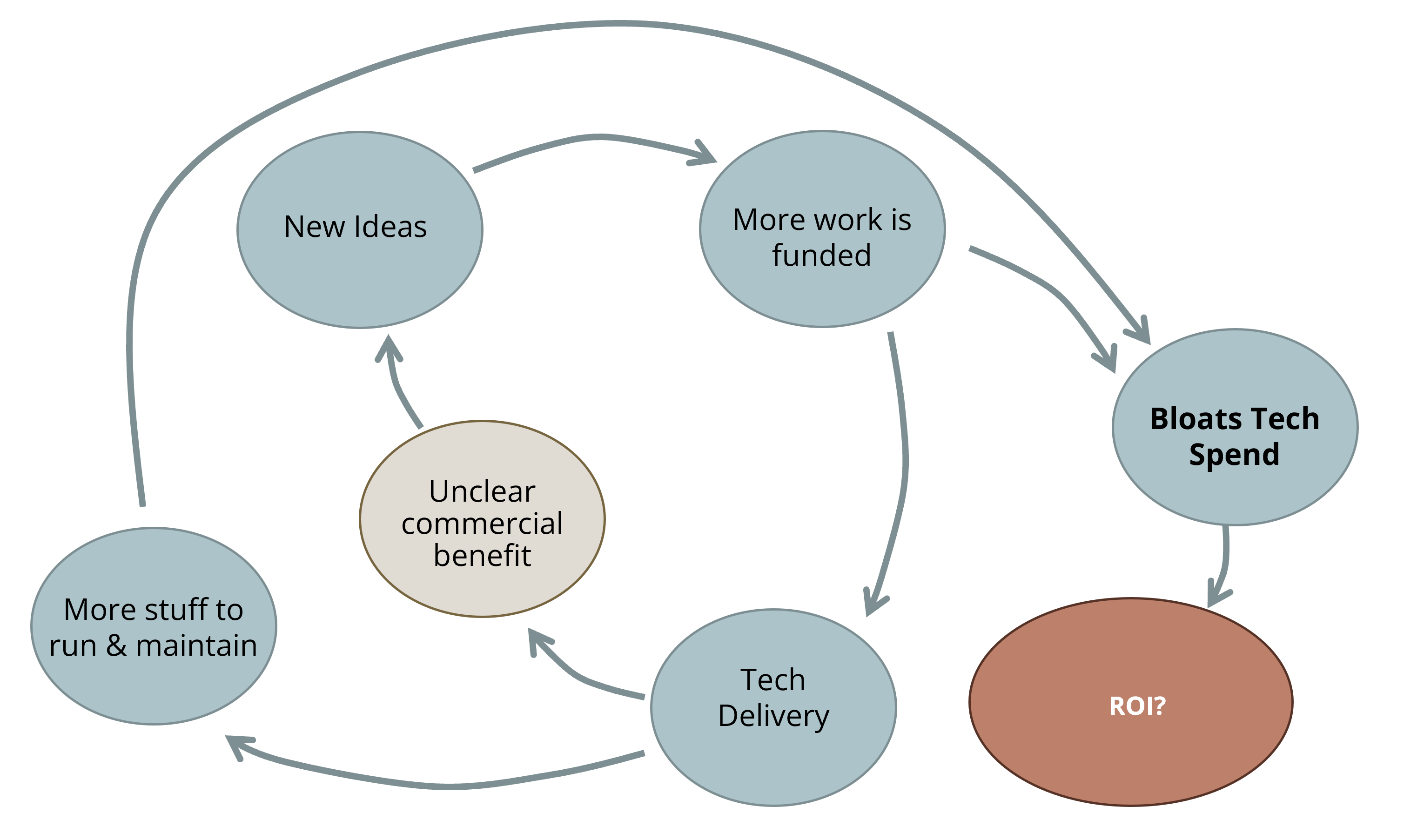
Most CIOs who inherit enterprise networks face a standard actuality: A long time of natural development have created environments that resist modernization. This brownfield complexity instantly impacts your group’s capacity to execute on digital transformation initiatives. Networks that require handbook intervention for routine adjustments create bottlenecks that sluggish innovation, improve operational prices and introduce pointless enterprise threat.
Take into account the monetary implications: A big enterprise may spend weeks planning and executing a easy community change throughout a number of places. With standardized, automation-ready infrastructure utilizing AI-driven insights, the identical change could be deployed in minutes with larger reliability and full audit trails. The distinction is not simply operational effectivity — it is aggressive benefit.
Associated:The Community Intelligence Blueprint
Strategic Standardization vs. Technical Standardization
Govt management should distinguish between technical standardization (essential for engineers) and strategic standardization (essential for enterprise outcomes). Strategic standardization focuses on three business-critical areas:
-
Operational predictability. Comparable enterprise capabilities ought to use related community patterns. Department places of work, knowledge facilities and cloud connections ought to observe constant architectural ideas that allow automated administration and fast scaling.
-
Change velocity. Standardized environments dramatically scale back the time and threat related to community adjustments. This instantly impacts your group’s capacity to answer market alternatives and enterprise necessities.
-
Danger administration. Constant configurations and procedures scale back the chance of human error whereas bettering incident response instances. Standardized environments are simpler to safe, audit and preserve.
Associated:The Clever Community Mandate
The Design-Pushed Transformation Framework
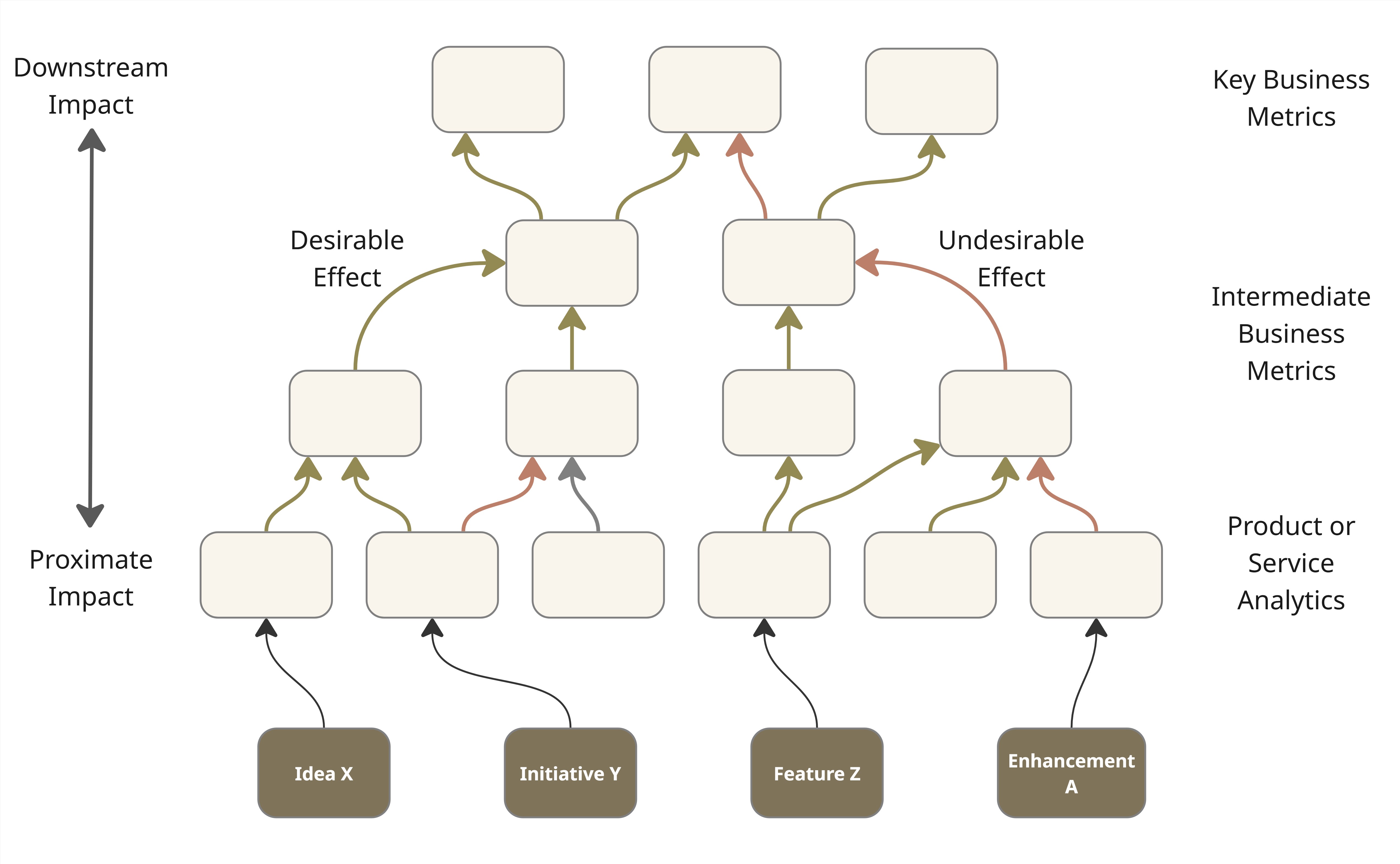
Profitable community standardization enhances design-driven automation, an method that treats community configuration because the implementation of documented, machine-readable design intentions slightly than advert hoc technical choices.
This framework operates on two parallel tracks:
-
Present state optimization. Utilizing your community documentation, establish and systematically remediate configuration inconsistencies that stop automation. This is not about reaching perfection; it is about creating ample consistency to allow automated administration.
-
Future state definition. Outline your goal community structure primarily based on enterprise necessities, not simply technical preferences. This goal state turns into the blueprint that guides each standardization efforts and automation improvement.
The important thing perception for executives is that standardization turns into each the prerequisite for and the result of profitable design-driven automation. You want sufficient consistency to start automating, however automation itself drives additional standardization as you uncover and remediate remaining inconsistencies.
Govt Implementation Technique
Standardization requires govt sponsorship as a result of it entails short-term operational funding for long-term strategic profit. This is the right way to method it.
Begin with enterprise impression
Determine community areas that almost all instantly have an effect on enterprise operations. Focus standardization efforts on infrastructure that helps essential providers or incessantly adjustments enterprise necessities.
Set up clear governance
Standardization is not a one-time undertaking — it is an ongoing operational self-discipline. Set up processes that preserve requirements as your community evolves and grows.
Measure enterprise outcomes
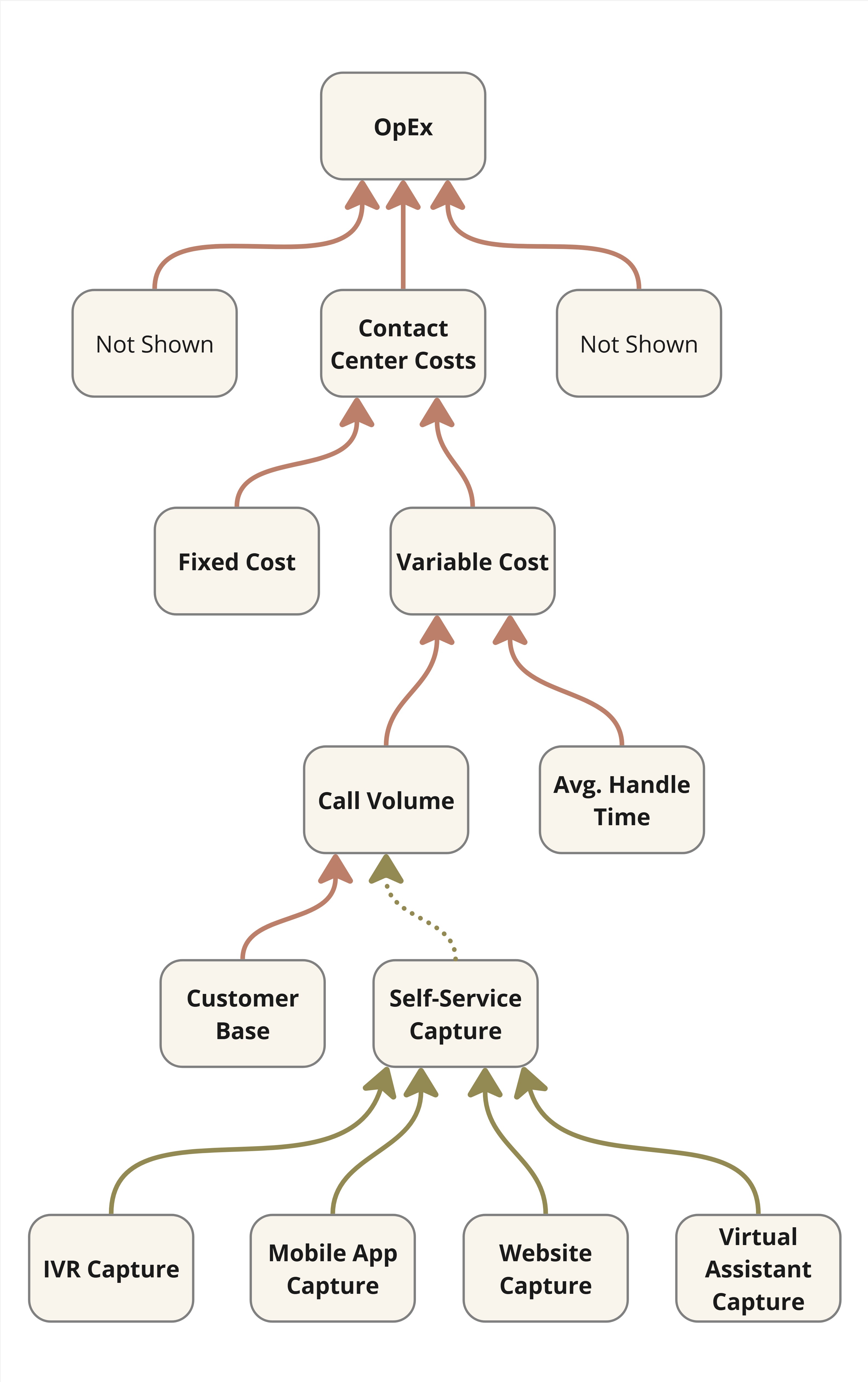
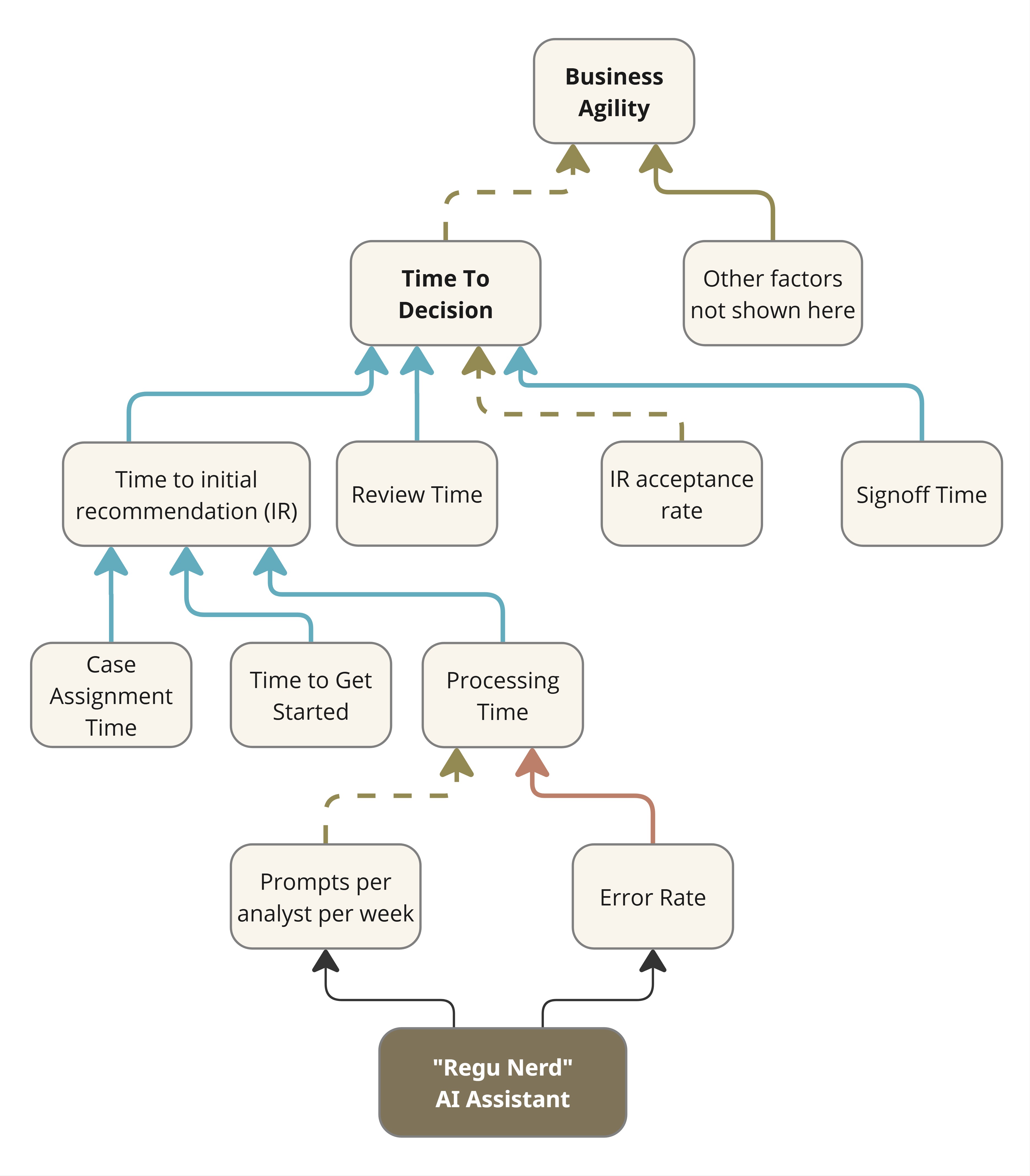
Monitor metrics that matter to enterprise stakeholders, reminiscent of service supply lead time, incident decision velocity and alter fail fee. Technical metrics like automation protection and configuration compliance are essential however secondary to enterprise outcomes.
Plan for cultural change
Standardization requires operational groups to work in a different way. Engineers should shift from craft-based configuration to systematic, standards-based approaches. This cultural transformation requires management help and clear communication about enterprise — and particular person — advantages.
Expertise Funding Concerns
Your know-how investments ought to help the three standardization enablers under.
Configuration administration
These instruments can establish, validate and remediate configuration drift throughout your atmosphere. They need to combine along with your present documentation methods and alter administration processes.
Automated validation
These capabilities constantly confirm community configurations and operational state towards outlined requirements, maybe utilizing AI-powered evaluation. This strikes compliance from handbook auditing to clever, steady monitoring that may predict and forestall points.
Orchestration platforms
These methods can implement standardized adjustments throughout a number of units and distributors whereas sustaining audit trails and rollback capabilities.
Probably the most profitable organizations deal with these investments as enterprise transformation initiatives slightly than technical upgrades, with success measured by operational agility and enterprise enablement slightly than purely technical metrics.
Frequent Govt Pitfalls
After working with know-how leaders throughout a number of industries, listed below are the strategic errors that derail standardization initiatives.
Anticipating fast ROI
Standardization is a foundational funding that permits future automation advantages. Organizations that demand fast returns typically underinvest on this essential section.
Treating it as a technical undertaking
Standardization impacts how groups work, not simply how networks are configured. Govt leaders should sponsor the cultural and course of adjustments required for fulfillment.
Perfectionism over progress
The purpose is not good standardization; it is ample standardization to realize goal outcomes. Organizations that pursue perfection typically miss the following advantages.
Ignoring operational constraints
Standardization should account for enterprise continuity necessities. Transformation approaches that disrupt essential providers will fail no matter their technical benefit.
The Path to Clever Networks
Community standardization represents a strategic inflection level for know-how organizations. Carried out appropriately, it transforms your community from a posh legal responsibility right into a strategic asset that permits fast enterprise response and aggressive differentiation.
The organizations that efficiently navigate this transformation share frequent traits:
-
Govt sponsorship that treats standardization as enterprise transformation.
-
Systematic approaches that steadiness operational constraints with transformation targets.
-
Measurement frameworks that join technical progress to enterprise outcomes.
Your standardization technique should align along with your broader digital transformation targets. In case your community serves as a strategic differentiator, investing in standardization capabilities that allow refined automation makes enterprise sense. In case your community primarily helps — slightly than differentiates your online business — standardization ought to give attention to decreasing operational prices and dangers whereas enabling potential future capabilities.
As soon as you have established standardized, well-documented community infrastructure, you are positioned to implement the automation and AI-driven orchestration capabilities that outline third-era networking.