A brand new wave of cyberattacks leveraging the Winos4.0 malware framework has focused organizations in Taiwan via malicious PDF attachments disguised as tax inspection alerts, based on a January 2025 menace evaluation by FortiGuard Labs.
The marketing campaign employs multi-stage payload supply, anti-forensic methods, and automatic safety bypass mechanisms to determine persistent entry to sufferer networks whereas evading detection.
Phishing Marketing campaign Masquerades as Tax Authority Communications
The assault chain begins with phishing emails purportedly despatched from Taiwan’s Nationwide Taxation Bureau, claiming to comprise a listing of enterprises scheduled for tax audits.
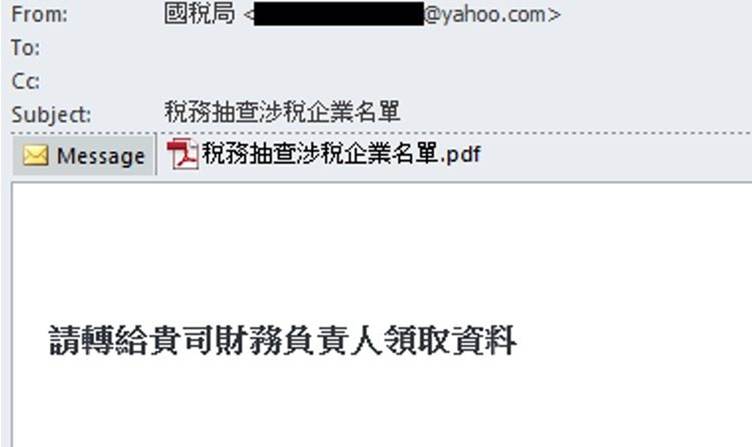

These emails direct recipients to obtain a malicious ZIP archive connected to a PDF doc formatted as an official Ministry of Finance memorandum.
Evaluation reveals the PDF (detected as PDF/Agent.A6DC!tr.dldr) accommodates socially engineered textual content prompting victims to extract and execute the “20250109.exe” loader from the connected archive.
FortiGuard researchers be aware this represents a tactical shift from earlier Winos4.0 distribution strategies noticed in November 2024, which relied on compromised gaming functions.
The strategic use of tax-themed lures throughout fiscal year-end durations will increase click-through charges amongst company finance groups, notably treasurers explicitly named within the phishing content material.
Technical Execution Circulation and Evasion Mechanisms
Upon execution, the loader initiates a three-stage course of:
- Pretend Utility Execution: The “ApowerREC.exe” file (a renamed malicious loader) triggers the import of “lastbld2Base.dll”, whose DLLMain operate decrypts embedded shellcode containing C2 server configurations (IP 9010[.]360sdgg[.]com) and modular plugin parameters.
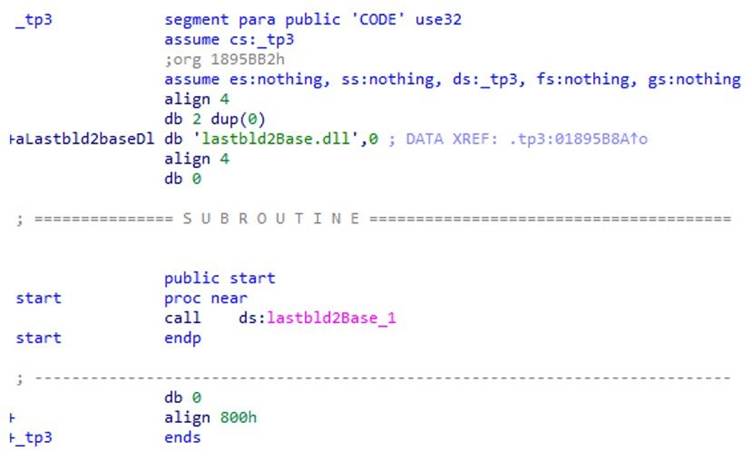

- Anti-Evaluation Countermeasures: The shellcode performs sandbox detection through sequential screenshot differential evaluation, requiring >20,000 pixel variations between photographs captured at 2-second intervals to substantiate human exercise. This stalls automated evaluation programs for as much as one hour earlier than continuing.
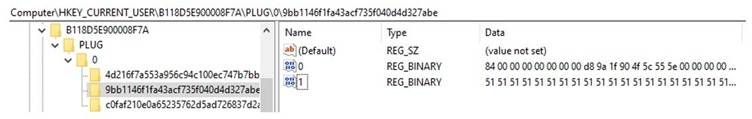
- Registry-Primarily based Payload Storage: Encrypted Winos4.0 modules write to HKEY_CURRENT_USERB118D5E900008F7A, with secondary shellcode dynamically resolving API calls to unpack the ultimate payload.
The core “loginmodule.dll” establishes eight concurrent threads for lateral motion and information harvesting1:
- MainThread: Disables display savers through SPI_SETSCREENSAVEACTIVE and compelled system wake states (ES_AWAYMODE_REQUIRED). Modifies UAC insurance policies by setting ConsentPromptBehaviorAdmin and PromptOnSecureDesktop registry values to 0 beneath HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem1.
- Anti-AV Thread: Terminates TCP connections related to 360Safe, Kingsoft, and Huorong safety processes utilizing GetTcpTable2 API hooking.
- Clipboard Hijacking: Replaces monetary key phrases in clipboard information utilizing regex patterns saved in HKEY_CURRENT_USERB118D5E900008F7Aclipboarddata.
Forensic artifacts present the malware creates mutex objects like GlobalMainThreadB118D5E900008F7A to stop redundant infections and writes keylogged information to C:ProgramDataB118D5E900008F7ARegedit.log.
Mitigation Methods and Defensive Countermeasures
FortiGuard’s response staff recommends:
- Enabling Content material Disarm & Reconstruction (CDR) on e mail gateways to neutralize malicious PDF macros.
- Monitoring registry modifications to HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem for UAC bypass makes an attempt.
- Deploying behavioral evaluation instruments to detect screenshot frequency anomalies and unscheduled system wake occasions.
Fortinet’s anti-malware suite now blocks related indicators as W32/Agent.7BBA!tr and W64/ValleyRat.A!tr.spy, with IP fame companies blacklisting confirmed C2 endpoints.

Geopolitical Implications and Marketing campaign Attribution
Whereas no specific attribution exists, focusing on Taiwanese fiscal programs and utilizing Simplified Chinese language annotations in USB system logs (“USB system inserted/eliminated”) recommend potential ties to cross-strait superior persistent menace teams.
The malware’s infrastructure overlaps with domains beforehand internet hosting gaming malware, indicating doable reuse of operational sources throughout campaigns.
FortiGuard Labs advises organizations to prioritize NSE cybersecurity coaching modules targeted on phishing identification and to implement utility allowlisting for executable recordsdata.
As Winos4.0 continues evolving its evasion toolkit, multi-layered defenses combining endpoint detection and community visitors evaluation stay vital to mitigating these surgically exact assaults.
Acquire Risk Intelligence on the Newest Malware and Phishing Assaults with ANY.RUN TI Lookup -> Strive free of charge
